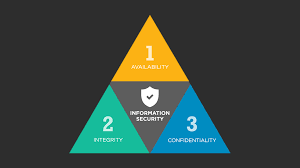
It is important to note that the CIA Triad has nothing to do with the Central Intelligence Agency. This is a model for security that different business can use. This stands for Confidentiality, Integrity, and Availability (The CIA Triad). Confidentiality deals with only giving access to people with the rights or authority. Integrity deals with making sure the data is not changed by users who do not have the right to alter information. Availability deals with making sure that the different information is able to be reached and access whenever staff needs it. Ben Miller is the creator of the CIA Triad. There are a lot of examples of CIA things that companies can implement. Some examples are two factor authentication, or ATMS. The two factor uses confidentiality as you need two different logins to access data. The confidentiality part of the triad deals with authentication and authorization. Authentication is when the system determines the identity of the person. It will use things such as several types of passwords to verify the person. Cryptographic keys and biometric are examples of these. Authorization deals making sure only people who are responsible or have permission can access things. An example of this that I thought of was when we login to blackboard. We only have access to data that our teachers allow us to see. We do not see everything our teachers have. Specific integrity is example can be corruptions dealing RAMs, “That’s at the exotic end of the spectrum, but any techniques designed to protect the physical integrity of storage media can also protect the virtual integrity of data” (The CIA Triad). A common example of availability is the denial-of-service attack. In all, the CIA Triad is all about the businesses and organizations thinking smarter about protecting their information. They in a sense are inspiring a way of life.
Works Cited
Fruhlinger, Josh. “The CIA Triad: DEFINITION, Components and Examples.” CSO Online, CSO, 10 Feb. 2020, www.csoonline.com/article/3519908/the-cia-triad-definition-components-and-examples.html.