WCS494 Academic Paper
Maria Martinez
WCS 494 Entrepreneurship
Professor Akeyla Porcher
12/10/23
In the face of today’s rapidly advancing digital age, the absence of cybersecurity awareness is a significant issue in societies worldwide. Given our daily reliance on technology, everyone must comprehend the importance of cybersecurity and the potential repercussions of overlooking it. My team’s innovation is a cybersecurity application, conceived from the realization that many individuals lack education in cybersecurity. Our app aims to address the issue of people not fully grasping aspects of cybersecurity.
Regrettably, older people often become victims of scams and various cyber-attacks. Many individuals struggle to utilize the technology they possess, possibly due to indifference or misunderstanding. Others, while adept at using their technology, fail to identify scams or threats. For instance, a basic phishing email might contain a random string of characters, while others might have just one extra character in the address. Spotting these anomalies can be enlightening, and once noticed, they’re hard to ignore. As technology continues to grow and expand daily, keeping up with every new development can be challenging. Our app will keep users informed about the latest essential news and innovations. If everyone has a basic understanding of cybersecurity and can apply it for self-protection, the internet could become a much safer space for the average user.
Scammers employ a variety of tactics to target older people. They often use phishing scams, where fraudulent emails or websites mimic legitimate sources, such as banks or financial institutions. Fake online stores are set up to sell nonexistent or low-quality products. Investment scams convince victims to invest money in fraudulent business ventures or schemes. Lottery scams claim the victim has won a contest or lottery, while romance scams involve a scammer forming a relationship with the victim before asking for money.
There are several reasons why older people are more likely to fall victim to online scams. First, they may lack familiarity with the internet and its associated risks. Second, they may be more trusting and less likely to suspect fraud. Finally, cognitive decline can make it harder for older people to recognize scams.
Our app is designed to assist with this. If a user wants to know the difference between a real and a fake email address, they could refer to an article or tip we posted on the subject. We would also provide notes on the varying complexity levels associated with the related threat. Online searches on this topic might yield simple steps on how to identify fakes, but this might not be helpful to some who want more information on why and how such things occur. Our app aims to avoid this by providing as much information as possible while maintaining user-friendliness. We don’t want to overwhelm the user.
Our objective is to make the app as user-friendly as possible without skimping on details. Our articles, tips, and general information would cover as much as possible about the most basic threats and more complex ones like a DDoS attack. However, having as much information as possible doesn’t mean overwhelming the user. We don’t want them to be inundated with pages of dull information. We aim to provide the most necessary and important information for the user to take away. We would achieve this by having a good page design and presenting the information in simpler terms that resonate with the reader.
To give you a visual of what our app will look like, imagine a welcome landing page that links to news articles from us or other credible sources about current cyber events or innovations when you open the app. Initially, we would ask the user about their phone type, age bracket, and their self-assessed level of cybersecurity knowledge (beginner, intermediate, advanced/expert). The landing page would also feature a daily targeted article for the user based on their data. We would have a sidebar menu where users can choose from different topics ranging from spam to CATO attacks, organized into related overall topics or categories with drop-down arrows for related topics. As this is not a nonprofit, our app would generate revenue from app store downloads, a premium plan, and ad revenue from ads displayed to free plan users. The premium plan would include an ad-free experience.
To explain the demand and reason for my entrepreneurial endeavor, understanding what cybersecurity means will be necessary. A scholarly journal titled “Defining Cybersecurity”, written by Dan Craigen, Nadia Diakun-Thibault, and Randy Purse explains the definition of cybersecurity. The authors explain the definition as, “Cybersecurity is the organization and collection of resources, processes, and structures used to protect cyberspace and cyberspace-enabled systems from occurrences that misalign de jure from de facto property rights” (Craigen, Diakun-Thibault, and Purse, 2014). Our entrepreneurial innovation will focus on the knowledge of cybersecurity: protecting the user in cyberspace from online scams.
The problem of older users, more specifically fifty years of age and up, falling victim to online scams and hackers has been seen time and time again. Claire Seunguen Lee and Yi Ting Chua explain the importance of cybersecurity awareness in their scholarly journal titled “The Role of Cybersecurity Knowledge and Awareness in Cybersecurity Intention and Behavior in the United States”. In their journal, they explain the significance of cybersecurity in protecting individuals, corporations, and national security from cybercrime and cybersecurity incidents. They highlight the increasing awareness of cybersecurity among the public, media, and academic domains. Our innovation aims to provide knowledge for these people when it comes to being safe and educated about cybersecurity measures.
Claire and Yi Ting explain how there is the existing research on cybersecurity is divided into two strands. The first is research in computer science and engineering, focusing on concepts, techniques, and development. The second is research in social sciences, such as criminology and media/communication studies, which is largely confined to cybercrime, security, and privacy. Furthermore, they note the gap in the literature regarding cybersecurity “knowledge”. While previous studies have focused on security behavior/intentions and privacy protection, there is less research on the individual characteristics and the level of cybersecurity knowledge that may affect one’s experiences with cybercrime. Our innovation will help close the gap in cybersecurity knowledge so fewer people fall victim to any online scam.
Claire and Yi Tings’ research aims to overcome these limitations by using a nationally representative dataset of United States citizens by the Pew Research Center. It seeks to explore factors predicting cybersecurity knowledge and differences in such dynamics among different groups. Their research questions include: Are Internet usage and smart device usage associated with cybersecurity knowledge? How does gender affect cybersecurity knowledge? What factors contribute to uncertainty in responses about cybersecurity knowledge? Data was used from a survey conducted from June 17 to 27, 2016 with respondents being internet users 18 and older.
Dependent variables: The respondents’ cybersecurity and cybercrime knowledge were measured using a factor analysis based on 12 survey questions. The outcome variable is conceptualized as internet literacy and computer literacy. Correct answers were coded as 1 and incorrect answers as 0. The total number of correct responses was used as the dependent variable for the remaining models on respondents’ cybersecurity and cybercrime knowledge. An additional dependent variable was created to measure the lack of cybersecurity and cybercrime knowledge, which measures the total number of items a respondent was unsure of or refused to answer. This was done to explore if predictors for the absence of knowledge would differ greatly from the total number of correct answers. The study includes key independent variables related to users’ routine activities, such as Internet and social media usage, frequency of Internet use, smartphone ownership, and social networking site (SNS) use. The frequency of Internet use was measured on a 5-point Likert-type scale, with higher scores indicating greater Internet usage. The use of mobile devices and smart devices to access the Internet was measured as binary variables, as was SNS use.
Control variables included sociodemographic factors like age, gender, employment status, education, and income, which are known to influence Internet use and cybersecurity knowledge. Age was measured as a continuous variable, while gender, education level, monthly household income, and employment status were measured as categorical variables. Ethnicity was recorded into five different binary variables to account for different responses. The data they found is listed below.
Table 1 of the study presents the Internet usage patterns of the 1,055 respondents. All respondents reported accessing the Internet in the last 12 months, with a significant majority (80.5%) using the Internet almost constantly. Most respondents accessed the Internet at least once a day. Regarding the devices used for Internet access, 77.3% of respondents reported using cellphones, tablets, or other mobile handheld devices. This aligns with the self-reported use of social media sites and smartphone ownership, which was reported by about three-quarters of the respondents.
Table 1. Descriptive Statistics (N = 1,051).
| Variables | Mean | SD | Min | Max |
| Frequency of Internet use | 0.775 | 0.418 | 0 | 1 |
| Smartphone ownership | 0.744 | 0.437 | 0 | 1 |
| SNS use | 0.733 | 0.443 | 0 | 1 |
| Education | 20.906 | 0.978 | 1 | 4 |
| Gender | 0.539 | 0.499 | 0 | 1 |
| Employed | 0.596 | 0.491 | 0 | 1 |
| Household income | 12.40 | 4.562 | 1 | 19 |
| MSA status | 0.744 | 0.437 | 0 | 1 |
| White | 0.721 | 0.449 | 0 | 1 |
| Black | 0.087 | 0.281 | 0 | 1 |
| Latinx | 0.117 | 0.327 | 0 | 1 |
| Other | 0.046 | 0.209 | 0 | 1 |
| Multiple race/ethnicity | 0.030 | 0.169 | 0 | 1 |
| Categorical variables | N | % | ||
| Gender | ||||
| Female (1) | 568 | 53.8 | ||
| Male (0) | 487 | 46.2 | ||
| Education | ||||
| Less than high school | 89 | 8.4 | ||
| High school | 291 | 27.6 | ||
| Some college | 306 | 29.0 | ||
| Bachelor’s degree or higher | 369 | 35.0 | ||
| Employed | ||||
| Employed (1) | 629 | 59.6 | ||
| Unemployed (0) | 426 | 40.4 | ||
In summary, the text underscores the importance of cybersecurity, identifies gaps in the current literature, and proposes research questions to further explore the factors influencing cybersecurity knowledge. It aims to contribute to a better understanding of what influences American citizens’ knowledge about cybersecurity. This review of the literature has helped our group use statistics and data to better model our innovation to be more effective. I have been able to take data conducted from studies like the one mentioned above to further our group’s entrepreneurial innovation of providing education for internet and computer knowledge.
A scholarly journal titled “There’s No App for That: Calibrating Cybersecurity Safeguards and Disclosures” written by Roland Trope is another review of cybersecurity literature my group dove into to further our entrepreneurial innovation. The introduction discusses the evolution of cybersecurity, highlighting that the term has become an oxymoron due to the increasing prevalence and severity of cyber threats. For a long time, companies preferred not to disclose breaches, leaving the extent of damages unknown. However, with data breach reporting statutes now in effect, the financial implications of breaches have become clearer. Trope mentions as an example “Sony PlayStation Network breach in 2011-2012, which compromised approximately 100 million customer accounts and cost an estimated $200 million in remediation, not including the costs of defending against fifty-eight class action suits” (Trope, 2012).
The scholarly journal also discusses the rapid deployment of new communications technologies, often outpacing efforts to assess and mitigate associated vulnerabilities. Trope found that the period between 2011 and 2012 saw cyber-attacks become more widespread, severe, and financially damaging. This has increased the pressure on enterprises and their legal counsel to broaden their cybersecurity measures beyond protecting the enterprise and its assets. The longer it takes an enterprise to detect and respond to an attack, the harder it will be for them to demonstrate that they have observed “reasonable commercial standards of fair dealing” (Trope, 2012). With this scholarly journal, we can see that whether you are just one person or a multi-million-dollar company, cybersecurity measures and knowledge must continue to advance as cybercrime rises year by year with the advancements of technology. With older people being a huge target group for online scams and cybercrime, our innovation will address this problem by providing the knowledge to avoid getting scammed.
Authors Carlene Blackwood-Brown, Yair Levy, and Steven Terrall, professors at the College of Engineering and Computing Nova Southeastern University, wrote “Senior Citizens and Cybersecurity Awareness”. They explain how one of the largest targeted groups of cybercrimes is senior citizens, “Senior citizens are one of the most vulnerable groups of Internet users who are prone to cyber-attacks” (Claar & Johnson, 2012; Grimes et al., 2010). Furthermore, they explain how it has become a more prevalent problem as more senior citizens are using the internet each year, as demonstrated in the graphic below.
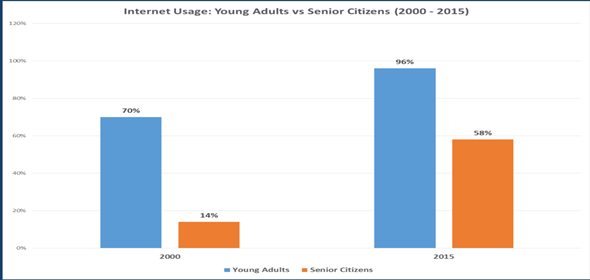
The authors explain, “One in five American senior citizens is a victim of online financial fraud, costing more than two point six billion dollars per year” (Willis, 2015). The senior citizens who are victims of online theft are often left with decreased self-confidence and huge financial loss. Awareness of cybersecurity and knowledge of how to use the internet safely is a major need in today’s time, which is why it makes a promising entrepreneurial endeavor for our innovation, which is comprised of cybersecurity knowledge specifically targeted at older people.
“Cyber Risk and Cybersecurity: a Systematic Review of Data Availability” is a scholarly journal written by Frank Cremer, Barry Sheehan, Michael Fortman, Arash Kia, Martin Mullins, Finbarr Murphy, and Stefan Materne. The authors present a systematic review of studies on cyber risk and cybersecurity databases, revealing a predominance of datasets in the field of intrusion detection and machine learning. The paper highlights the scarcity of datasets on cyber risks, which poses a significant challenge for cyber insurance stakeholders due to the dynamic nature of cyber risks and the lack of historical data. The authors suggest that mandatory reporting of cyber incidents could enhance understanding and awareness of cyber risks among companies and insurers and facilitate more in-depth research into these risks. They also propose that the availability of more data could lead to a common understanding of cyber risks among insurers, supporting risk-based pricing.
The paper provides a comprehensive overview of peer-reviewed datasets and other available datasets in cyber risk and cybersecurity, which could help companies assess their internal cyber posture and cybersecurity measures. The authors identify several areas for future research, including the need for more publicly available datasets that reflect current environmental conditions, the integrability and adaptability of cybersecurity and cyber risk datasets, and the ability for stakeholders to identify machine-readable cybersecurity datasets. They argue that these advancements could improve intrusion detection systems, allow for clearer comparisons between datasets, and enable concrete benchmarks to be applied.
The goal of our entrepreneurial endeavor is to prevent cybercrime towards people that do not have a strong foundation of cybersecurity knowledge. As mentioned above in the scholarly journal, datasets regarding cybercrime need to be made public so that they can be researched. Entrepreneurship plays a role in preventing cybercrime that the scholarly journal mentioned. Promoting a risk-aware culture can help prevent cybercrime. Taking the initiative to implement security technologies is another way entrepreneurs can prevent future assaults. Anyone will be able to use our innovation to educate themselves in this realm (will still be targeted towards the older generations as they are newer to the internet).
To become an entrepreneur, one must be able to combine multiple disciplines into any endeavor or business they are pursuing/creating. Authors Johanna Jacob, Michelle Peters, and T. Andrew Yang wrote the scholarly journal titled, “Interdisciplinary Cybersecurity: Rethinking the Approach and the Process”. They explain in their journal that the rapid advancement in computing and technology and its widespread adoption in almost every human activity has ushered in an era of interdisciplinarity. This involves understanding and applying knowledge from one field within the context of one or more other fields. “Interdisciplinarity is defined as the combination of two or more disciplines into a single, cross-discipline learning experience” (Jacob, Peters, and Yang, 2020). The section emphasizes the importance of an interdisciplinary education in cybersecurity, incorporating theories from disciplines such as criminology, legal studies, and economics. It also provides details on the theoretical framework that underpins the quantitative study. Even though our innovation has to do with cybersecurity, multiple different fields are brought together to create this innovation. Cybersecurity, leadership, and business are just some of the disciplines that were needed to create this innovation of ours.
A scholarly article titled “Cybersecurity Leadership” written by Nicole Radziwill emphasizes the importance of incorporating cybersecurity into quality and risk management efforts, particularly in production and critical infrastructure environments. It provides insight into some first principles that can be applied to start closing the gap in cybersecurity knowledge among quality managers. Leadership within cybersecurity and entrepreneurship is important to recognize as any field has a leadership side to it. Our innovation was not possible without some form of leadership to build, guide, and market it. Leadership is important in developing a business when it comes to motivating the team members who are helping to build it, promoting problem-solving, promoting decision-making, fostering innovation, improving efficiency within the team and business, and enhancing its success. In summary, leadership is essential for guiding a team toward achieving its goals, fostering innovation, and ensuring the success of both business and app development projects. It’s about creating a vision and inspiring others to help achieve it. This review of literature has helped my team and I to understand why it is important to develop an app to help bring awareness and answer any questions about cybercrime and why multiple disciplines are necessary to solve a problem, like the one our innovation solves.
Creating a cybersecurity application is a very complex process that requires knowledge outside of my major (cybersecurity). Leadership, business knowledge, accounting, and marketing expertise are also needed education components that are necessary to create any application. Leadership plays a pivotal role in app development. Leaders are needed to help create the vision for the application, inspire and motivate the team, and help make key decisions. They inspire the team to think creatively and solve complex problems. When the leader is effective, they can help promote efficiency and help ensure the best outcome for the application.
The development of an app also requires a keen understanding of business aspects. The app’s revenue model, which could be a combination of in-app purchases, advertisements, subscriptions, or other methods, is a fundamental business element. It’s essential to understand the target market and their needs to design an app that provides value and meets user expectations. The business strategy should also take into account various factors such as competition, regulatory requirements, and potential partnerships.
Marketing plays a pivotal role in the triumph of an app. It initiates with market analysis to understand the needs and preferences of users, which in turn shapes the design and features of the app. Marketing strategies amplify the app’s exposure, fostering user acquisition and interaction. These strategies may include optimization for app stores, marketing on social media, influencer marketing, and email marketing. A meticulously planned and implemented marketing campaign can escalate downloads, amplify user engagement, and ultimately, augment revenue.
In the realm of a profit-oriented app, the role of accounting is paramount. It’s tasked with the compilation of the app’s financial statements, which includes monitoring the revenue streams from the app, such as income from in-app purchases, ad revenue, and subscriptions that our innovation will encompass. In our entrepreneurial journey, accounting will be instrumental in keeping tabs on the expenses related to the app’s development and upkeep. These costs encompass software development, server hosting, maintenance, updates, and staff remuneration. Accounting is also crucial in formulating budgets for the app’s development and marketing costs. It plays a key role in predicting future income and expenditures, which is vital for strategic planning. Accounting offers a transparent view of the app’s financial status, guides strategic decisions, ensures adherence to regulatory standards, and is a significant contributor to the app’s overall success.
The significance of psychology in app development, especially in the realms of user experience and user interface design, cannot be overstated. By delving into human behavior, cognitive functions, and emotional reactions, we can significantly improve an app’s usability and attractiveness. Cognitive psychology principles, for example, can guide the creation of intuitive interfaces and efficient navigation routes. Insights from social psychology can shape the incorporation of social networking elements or teamwork tools in the app. Furthermore, recognizing individual variances, such as age or cultural background, can assist in tailoring user experiences. Psychologists also participate in user research, which tests if the app is experienced as planned. They collaborate with the production team to comprehend the app’s objectives and convert those objectives into researchable queries. Psychologists also aid in the advancement of AI technologies utilized in apps, including therapeutic chatbots and facial recognition systems. They also explore human-computer interaction, digital therapeutics, and automation ethics. In summary, psychology offers valuable insights into human behavior and cognition, which can be harnessed to create more efficient, engaging, and successful apps.
In summary, the creation of a successful app is a collaborative effort that necessitates effective leadership, a robust business strategy, and focused marketing. Leaders motivate and steer the team, while business aspects ensure the app is valuable and has a sustainable revenue model. Marketing tactics amplify the app’s visibility and user engagement, propelling its success. Collectively, these components work in synergy, facilitating the development of an app that connects with users and accomplishes business goals.
The process of assessing the efficacy of our innovation is multifaceted, involving a blend of diverse metrics and key performance indicators. One of the indicators will be user interaction. This gauges the extent of interaction with the innovation. A high level of interaction often suggests that the innovation is striking a chord with its target audience (fifty and up since the younger education have more access now to cybersecurity education than ever). Our projected profitability will also be another indicator. This entails estimating the potential financial benefits of the innovation. It offers a prospective view of the efficacy of the innovation. Furthermore, our realized profitability after 6 months will give us the most accurate measure of profitability our innovation has accrued. When we can compare realized profitability with projected profitability, it will offer insights into the precision of initial projections and the financial success of our innovation. Another indicator is monitoring the expenses associated with our innovation. This includes our costs for development, operations, and marketing. Another indicator is the impact on the targeted audience (older people). If we see a statistical change as well as user reviews on their ability to keep themselves safe online from cybercrime after using our educational application.
In conclusion, assessing the efficacy of innovation involves a comprehensive evaluation of various factors, including user interaction, profitability, costs, cultural impact on the targeted audience, and specific innovation KPIs. It demands a systematic approach and a profound understanding of the innovation’s objectives and the context in which it operates. Since our application will be available in the app store, we can also judge its effectiveness on how many downloads we see. We can measure this on a quarterly basis. Another important factor is that we will regularly update it. The cybersecurity and tech realm advance daily, and so does the crime within it. This is a product that once paid for, will continue to provide a product with new educational points within it constantly.
In the digital age, cybersecurity has become a critical concern. With the increasing reliance on technology, the need for robust cybersecurity measures is more important than ever. This innovation is the development of an educational cybersecurity app and the steps that are involved in turning this concept into a reality. The first step in developing an educational cybersecurity app is conceptualization. This involves identifying the target audience (older generations), understanding their needs (cybersecurity education), and defining the learning objectives within the application. Our app aims to educate users about various cybersecurity threats, safe online practices, and ways to protect their digital assets. It will be user-friendly, engaging, and interactive to ensure effective learning.
Once the concept is clear, our next step is design and development. This involves creating a blueprint of the app, deciding on the features, and designing the user interface. Our objective is to make the app as user-friendly as possible without leaving out important details. Our articles, tips, and general information would cover as much as possible about the most basic threats and more complex ones like a DDoS attack. However, having as much information as possible doesn’t mean overwhelming the user. Too much text and too little graphics does not allow for the most efficient cognitive processing. We will achieve this by having a a page with the important design principles taken into consideration. For example, segmentation design principle and multimedia design principle.
The app will include modules on different cybersecurity topics, quizzes to test knowledge, and resources for further learning. It’s crucial to ensure the app is compatible with different operating systems for wider accessibility. After the app is developed, it’s important to conduct thorough testing. This includes functionality testing, usability testing, and security testing. Any bugs or issues identified during this stage should be fixed to ensure the app works seamlessly.
Once the app is tested and ready, we will be able to launch it. This involves making the app available on various app stores and promoting it through different channels to reach the target audience. Social media like Facebook will be one of our main sources of advertising our innovation. We will set up a Facebook business page to build our online presence on there. We can then start running our advertisements. The success of our ads will depend on how good our content is. We will make sure the ads have a clear message, compelling visuals, and a strong call-to-action.
AARP magazines are another outlet that we will advertise in. Reaching out to communities with senior citizen gatherings (nursing homes for example) will give us more opportunities to market our innovation. Post-launch we will collect user feedback and make necessary updates. We will have surveys that the users can fill out and update us on how well the app works for them, as well as any improvements we can make to the app. This helps us in improving the app and ensuring it continues to meet the needs of the users. Regular updates also help in keeping the app’s content current with the latest cybersecurity trends. Since technology develops rapidly, so does the crime within it. Keeping our app updated constantly is a very important component. Since this is a for profit application, the product needs to be worth the user spending money on it, and we can ensure its worth the money if the user is constantly able to get updated on the latest online scams.
Developing an educational cybersecurity app involves several steps, from conceptualization to launch. However, the effort is worthwhile as it contributes to raising awareness about cybersecurity and promoting safe online practices. With the right approach and commitment, turning this vision into reality is certainly achievable.
After developing a cybersecurity app, the next steps for us involve launching and promoting the app to reach the target audience, which is the older generations. Before launching, we will have to conduct extensive testing to ensure the app functions as intended. We do not want any hiccups or bugs ruining the credibility and hype of the new application. This includes usability testing, performance testing, and security testing. Any bugs or issues identified will be resolved.
App Store Optimization is a key step in preparing for our launch. This involves optimizing the app’s title (AllSafe), description, and keywords to improve its visibility in app store search results. High-quality screenshots and a compelling app icon can also enhance the app’s appeal. A detailed launch plan will be developed, outlining the launch date, promotional activities, and post-launch support.
Promotion is crucial to generate buzz and attract users to our innovation. This will involve social media marketing (Facebook), AARP magazines, and my group going in person to local senior citizen gatherings to explain our application. Offering a limited-time discount or exclusive features can also incentivize downloads, so we will offer a seven-day free trial as an incentive.
On the launch day, our app will be published in the app stores. We need to monitor the app’s performance closely and resolve any issues promptly, especially within the first couple of months after launching. After the launch, providing excellent customer support is crucial for our buisness. This includes responding to user queries, resolving issues, and regularly updating the app based on user feedback. Engaging users post-launch is another key to the app’s success. This will involve push notifications, in-app messages, and regular content updates to keep our users engaged and encourage them to use the app regularly.
Launching a cybersecurity app involves careful planning, effective promotion, and ongoing support. By following these steps, our app will reach its target audience and achieve its objectives.
References
Blackwood-Brown, C., Levy, Y., & Terrell, S. (n.d.). Senior citizens and cybersecurity awareness – nova.edu. https://www.nova.edu/gwep/igti/presentations/2016-igti/senior-citizens-and-cybersecurity-awareness.pdf
Craigen, D., Diakun-Thibault, N., & Purse, R. (2014). Defining cybersecurity. Technology Innovation Management Review, 4(10), 13–21. https://doi.org/10.22215/timreview/835
Cremer, F., Sheehan, B., Fortmann, M., Kia, A. N., Mullins, M., Murphy, F., & Materne, S. (2022). Cyber risk and cybersecurity: A systematic review of data availability. The Geneva Papers on Risk and Insurance – Issues and Practice, 47(3), 698–736. https://doi.org/10.1057/s41288-022-00266-6
Jacob, J., Peters, M., & Yang, T. A. (2019). Interdisciplinary cybersecurity: Rethinking the approach and the process. Advances in Intelligent Systems and Computing, 61–74. https://doi.org/10.1007/978-3-030-31239-8_6
Lee, C. S., & Chua, Y. T. (2023). The role of cybersecurity knowledge and awareness in cybersecurity intention and behavior in the United States. Crime & Delinquency. https://doi.org/10.1177/00111287231180093
Radziwill, N. M. (2018). Cybersecurity leadership. Quality Management Journal, 25(2), 109–109. https://doi.org/10.1080/10686967.2018.1436356
Trope, R. L. (2012). “There’s No App for That”: Calibrating Cybersecurity Safeguards and Disclosures. The Business Lawyer, 68(1), 183-195. http://proxy.lib.odu.edu/login?url=https://www.proquest.com/trade-journals/theres-no-app-that-calibrating-cybersecurity/docview/1266042351/se-2