Journal Entry #1 Topic
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
The NICE framework consists of Oversight and Governance (OG), Design and Development (DD), Implementation and Operation (IO), Protection and Defense (PD), Investigation (IN), Cyberspace Intelligence (CI), and Cyberspace Effects (CE). The areas that I want to focus on for my career are Design and Development and Protection and Defense. Design and Development helps with conducting research to help design and create secure technological systems. In the world of Cybersecurity having a secure environment is a field I find very important, because of the technological advances in this world any company stands risk of being hacked and cyber-attacked and having secure technology is vital. The next are Protection and Defense, this area helps to analyze risks to technological systems and networks, including investigating cybersecurity crimes. This is another vital area in Cybersecurity as vulnerabilities are everywhere and the ability to test and implement defenses based on a vulnerability assessment is the most realistic way to protect technology and my career goal is to become an ethical hacker which helps with this exact role in cybersecurity.
Journal Entry #2 Topic
Explain how the principles of science relate to cybersecurity.
There is quite a few and important ways that Science relates to Cybersecurity. For cybersecurity to understand security threats certain scientific methods can be used like hypotheses, experiments and analyzing data to improve security. Another way science can help secure data is by using a fundamental branch, mathematics. Mathematics can be used for cryptographic algorithms which help secure data. Human factors play a huge role in Cybersecurity and by using science to understand the ways that humans interact with technology and how they secure their data. Cybersecurity involves a lot of research as to finding best practices and methods to keep data as secure as possible, this scientific method is innovation and research. In summary, science helps drive the research, testing, and securing of technologies in order to find the most secure method as well as find weaknesses in security and implement the best practices for keeping people’s data as secure as possible.
Journal Entry #3 Topic
Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches?
The website PrivacyRights.org has a tool called Data Breach Chronology. This tool provides a ton of information about data breaches in the United States. When you first click on the tool you are located on a page called Key Insights Timeline which gives you a run down on breach information that they have in their database, a graph on specific types of breaches and how many occurred for that certain type, and a graph overtime from when they started collecting data in 2005 up until now on breaches that were reported to their database. You also have the ability to search the breaches for specific key words, view breaches by state, and view breaches by category. This tool can be a significant help to researchers as they can pick and choose the information they would like to pull up and find the exact information they are looking for based on how this website filters their data and makes the breach information easily accessible and easy to find with all the built in tools on the website to help researchers find the information they exactly need.
Journal Entry #4 Topic
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
Maslow’s Hierarchy of Needs is a pyramid diagram that consists of 5 parts. The 5 parts are Physiological, Safety, Love/Belonging, Esteem, and Self-actualization. So how does the physiological part of the pyramid tie into my experiences with technology. Well physiological are things like eating and sleeping and I’ve used my phone for tracking the meals I eat which will count the number of calories I have during the day as well as using my smartwatch to analyze my sleep patterns and see what kind of rest I’m getting at night. The next section is Love/Belonging which is security of your body or family, health and property. I can link multiple technologies that have helped in this area, like video surveillance and fire alarms, keeping my family safe from harm when I’m out at work, brings me safety of my family. Next section is love/belonging like family and friendship, and this is easily explained by being able to stay connected to friends and family wherever they may be in the world via cellphone or a computer. The next part of th pyramid is esteem and I think what I am doing now in regard to pursuing a career in obtaining my degree online is fulfilling my esteem and being able to do it online is amazing and not needing to sit down and be in a classroom. Finally, self-actualization is basically creativity, and we see this throughout the whole technological field, with all the new inventions and technologies coming out, the emergence of AI powered tools is all part of self-actualization.
Journal Entry # 5 Topic
Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
The individual motives are Entertainment, Political, Revenge, Boredom, Recognition, For money, and Multiple reasons. Motive rank #1 to me is a no brainer and that is “Money”. Individuals have multiple reasons do commit acts for money and cybercrime is a crime that “could” go unpunished if performed correctly, so people see this as a “get money easy” scheme. I rank motive “Revenge” at #2. Unfortunately, many crimes are linked to revenge and what easier way is there to seek revenge than installing some ransomware or virus on your target and “most” likely getting away with it. “Political” is ranked #3 as this world revolves around presidential elections and political sides on who has the most influence in this country as well as pointing the finger of who did what and who is responsible for treason or whatever the headline might be. #4 is Recognition, people want to feel important or just feel like they are needed and sometimes if they can’t get it ethically, they will do it unethically. #5 Entertainment, someone just may have learned about computer hacking and thought that it sounded simple and tried it themselves without thinking of the consequences. #6 Boredom I don’t see this motive very popular as myself when I’m bored, I don’t pick up a computer and start hacking something as I don’t have the skills but maybe a true “hacker” just does it because they can. #7 Multiple reasons, this is such a broad category that I’m sticking it in last in the rankings just because to me it seems like it is a catch all “motive”.
Journal Entry #6 Topic
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?
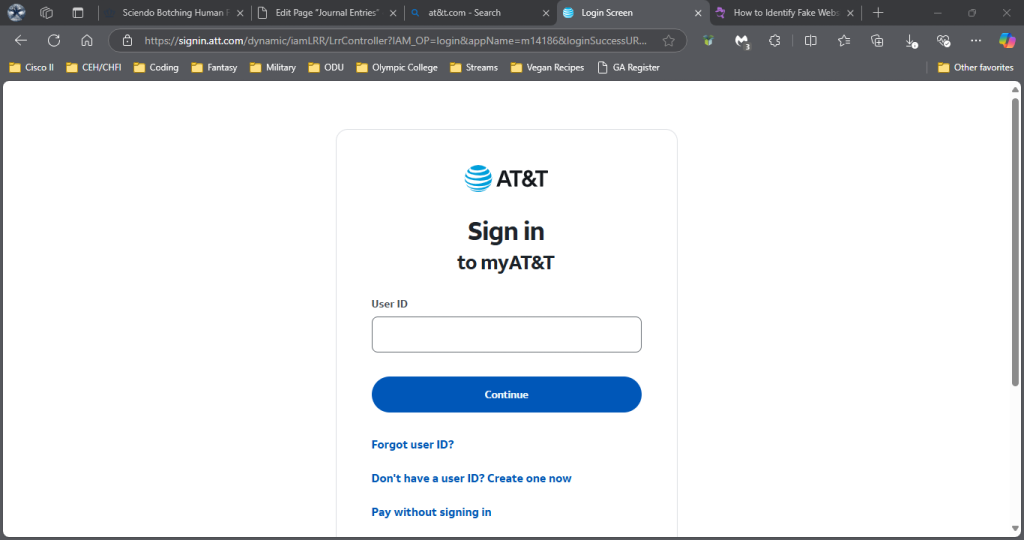
Here is the actual AT&T login page.
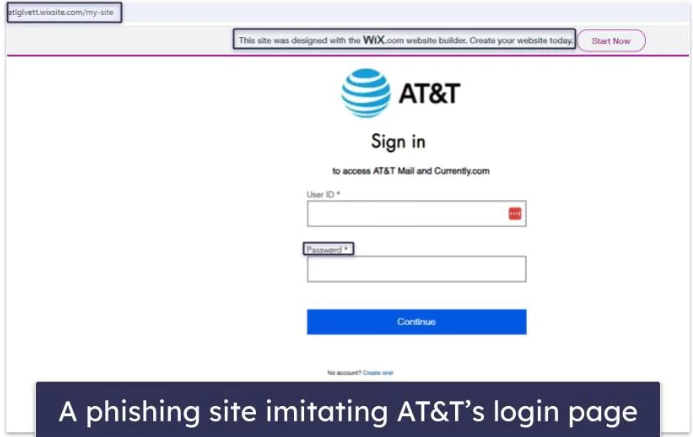
Here is the fake AT&T login page.
Visually fake websites are meant to look exactly like the real one. However, there are ways to spot differences and pay attention to make sure you’re on the real website, especially if you’re clicking a link from an email. First thing to look out for is the companies usually tend to have their hostname the same as their actual company, like at&t.com and as you can see the phishing website has something else like website.com or even att.com without the & symbol.
Journal Entry #7 Topic
Review the following ten photos through a human-centered cybersecurity framework. Create a meme for your favorite three, explaining what is going on in the individual’s or individuals’ mind(s) and explain how your memes relate to Human-centered cybersecurity.

This here icon is a person about to browse the internet, either at work or home or wherever the user may be. Human-centered cybersecurity uses research to provide policy makers, decision makers and cybersecurity professionals with to provide adequate information of the human element relating to technology. A lot of technologies can provide security to individuals on their own, however, the human element that this meme is warning about are the factors like humans clicking on fake website links, falling for phishing scams or even just navigating to bad websites that install malware onto the computer.
Journal Entry #8 Topic
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity.
Journal Entry #9 Topic
Complete the Social Media Disorder scale. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
How did you score?
– I’d say I scored quite well as I don’t have social media as in (Facebook, X, And Instagram). I do have LinkedIn but don’t feel the need or necessity to open it up daily to post updates.
What do you think about the items in the scale?
– The questions directly target individuals suffering with the need to be seen or heard on social media and I just don’t have that desire. But I see how this could be an eye opening experience to some people.
Why do you think that different patterns are found across the world?
– Like I said in the last question some people may see this as an eye-opening experience, and they realize their issue and try and resolve it. Others may not see that they have such an issue and continue on with their behavior, not worried at all.
Journal Entry #10 Topic
Read this and write a journal entry summarizing your response to the article on social cybersecurity.
Journal Entry #11 Topic
As you watch the video, think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
Journal Entry #12 Topic
Read the sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
Journal Entry #13 Topic
Read the article and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
Journal Entry #14 Topic
Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.