Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career. In the video, the speaker explains how he was originally working in accounting that eventually led to him assisting in the company’s …
Category: CYSE-201S Journal
CYSE-201S SPRING 2024 COURSE
Apr 07 2024
Week 13 – Journal Entry
Andriy Slynchuk has described eleven things internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious. Out of the eleven illegal internet activities, the five that stand out to me the most: Collecting Information about …
Mar 31 2024
Week 12 – Journal Entry
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try exploring the cyber infrastructure using …
Mar 31 2024
Week 12 – Journal Entry
Read this sample breach letter, “SAMPLE DATA BREACH NOTIFICATION,” and describe how two different economics theories and two different social sciences theories relate to the letter. A good way to approach this type of situation, and apply social & economic theories, would be to incorporate theories based off of four perspectives that could be involved: …
Mar 24 2024
Week 11 – Journal Entry
Watch this video. As you watch the video, think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation. The main social theme that arises involves digital defense, specifically the combination of cybersecurity and digital defense as a social theme. Some …
Mar 22 2024
Week 11 – Journal Entry
Read this and write a journal entry summarizing your response to the article on social cybersecurity. The article, referenced above, illustrates the criticality and importance of adapting to the new capabilities of technology in regard to the defense of the U.S. as well as the militaristic capabilities of the U.S. One topic of the article …
Mar 18 2024
Week 9/10 – Journal Entry
Complete the Social Media Disorder scale. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world? Here are my answers respectively to the questions (questions are long so only answers to the questions are provided): 1. No, 2. No, …
Mar 04 2024
Week 8 – Journal Entry
Watch this video and pay attention to the way that movies distort hackers. Hacker Rates 12 Hacking Scenes In Movies And TV | How Real Is It? – YouTube After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity. The media has a negative influence on …
Feb 25 2024
Week 7 – Journal Entry
Create a meme for your favorite three [images], explaining what is going on in the individual or individuals’ mind(s). Explain how your memes relate to human-centered cybersecurity. An important aspect/characteristic/necessity in human-centered cybersecurity is the knowledge of the individual accessing the device or network. If individuals are not properly and/or thoroughly educated about the best …
Feb 19 2024
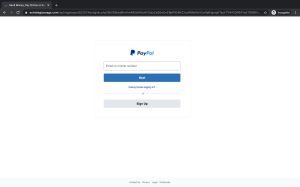
Week 6 – Journal Entry
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake? Below are three examples of screenshots of fake websites pretending to be real websites that I found on the internet: One of the most telltale signs of a fake website is …
- 1
- 2