My Personal Narrative Essay
Personal Narrative Essay
Matthew Hunter
3/31/2024
Freshman
My road to figuring out what I wanted to do for a living is quite complicated. My freshman year was honestly quite chaotic. There was this thing that kind of took over the world for a little bit it was called covid. It was super
I have always wanted to help people and I just wanted to find a way that I can I have grown up in a family that my mom was a police officer and then went on to work for the government and my father works for the police department. Also, my grandfather worked for the navy as did my great grandfather. The reason I am saying this is since I have grown up around people helping others and serving their country. The way that I feel like I can help others best is from behind a screen.
Sophomore
I have had a few different jobs. However, I have not worked with anything related to the Cyber field. I worked at a movie theater called Cinema Cafe where I worked as a cook with a lot of my friends from high school.
Junior
My first two years of college really have not been much for cyber security. I learned and completely nearly all of my pre major and all my elective classes and my next two years I really started to ramp up my cyber field so that I could learn more about what the cyber field is truly about and what they do in the real world.
Senior
This year has been a major leap into my cyber security degree and field. I learned and am learning how to code on two different platforms and how to use them. For example, I learned how to code on Python and am learning how to code on Linux. I understand and get how to code. However, I like doing more of the hands-on work like building and fixing stuff, not really the coding.
As I wrote earlier this semester for a discussion board, “my opinion on work experience is that I learn better from work experience because it is more hands-on, and I can use that information. I have always been this way ever since I was a child. This is a great example of how I am. I would rather be thrown into something and learn that way rather than learning from a book. I have no idea why I learn this way. For me, it is a hands-on experience rather than a book work. I work at a hot dog place where you must make everything a specific way and make it look a certain way. The way I learned was that I went and watched and learned from her.”
Artifacts
1. Starting a project with WNK Aviation where we are creating a game for people to buy drones and are able to test them on the game.
2. Starting a project with WNK Aviation where they are creating a drone training and counter defensive training.
3. NIST Framework Learning
4. Learning how to and doing tests on different services
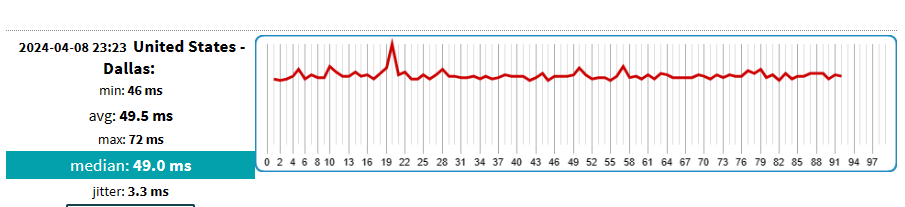
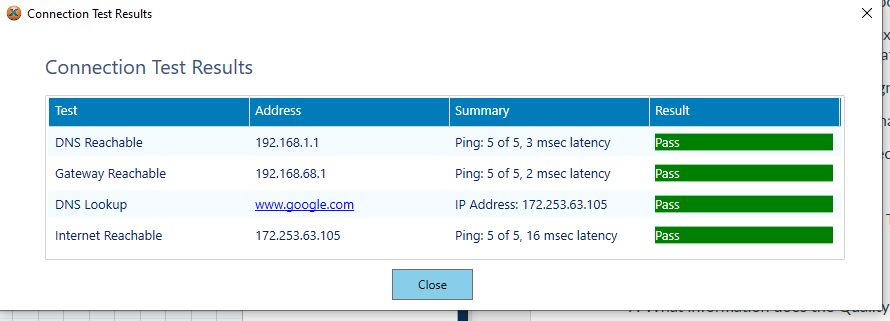
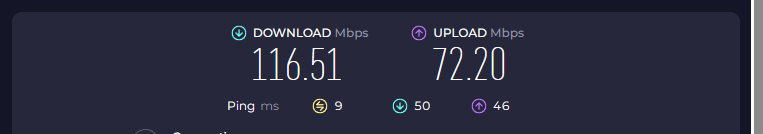
5. Completing an assignment about a major attack in cybersecurity
Assignment 9
Listen to “Episode #29: Stuxnet of the DarkNet Diaries podcast which can be found at https://darknetdiaries.com/episode/29/ Based on the podcast, answer the following questions.
- What was the intended target of the Stuxnet attack, and why was it deemed a high-value target?
The intended target of the Stuxnet attack was the nuclear program of Iran. Because it was how they were making nuclear weapons and progressing.
- Who is believed to have created and launched the Stuxnet attack, and what motivated them to do so?
The us and Israel created the Stuxnet. Because of the threat of the nuclear program of Iran.
- How was Stuxnet able to evade detection for such a prolonged period, and what led to its eventual discovery?
The Stuxnet was more evolved than normal technology. It was discovered by Sergey Ulasen and he found it working on a computer.
- Which two U.S. government labs were utilized, and what specific activities occurred at each facility?
One of the labs were called the Idaho National Lab which is under the energy department. The other lad was a secret lab in Tennessee in Oakridge National Labotory.
- Which two U.S. Presidents were involved in the Stuxnet attack, and what were their respective roles in the process?
The two Presidents who were involved were George W. Bush and President Barack Obama. They had to authorize these secret attacks.
6. Assignment-3-Working with vi editor
7. Assignment #1 – Basic Linux Commands
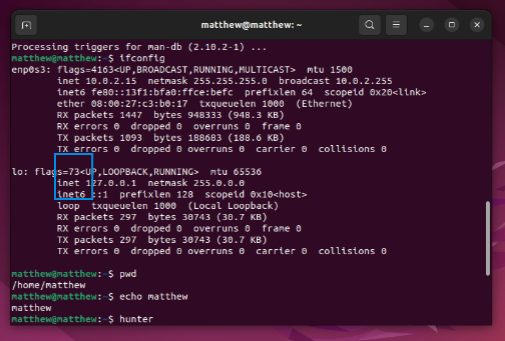
8. CYSE 270: Linux System for Cybersecurity
Lab 7 – Manage Local Storage
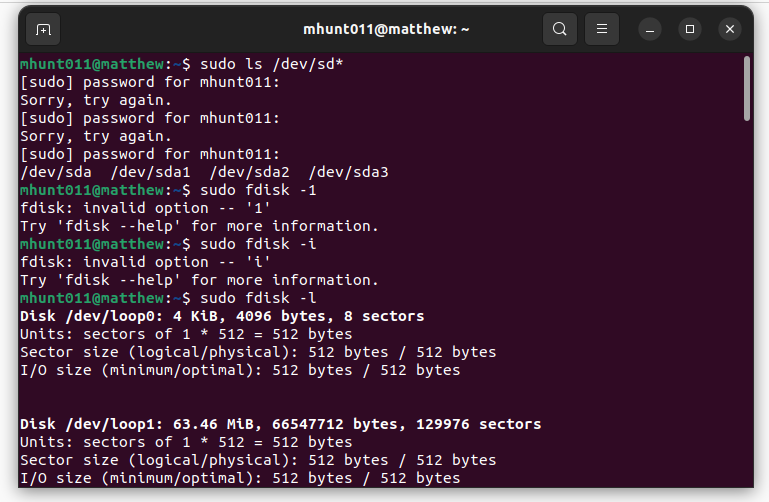
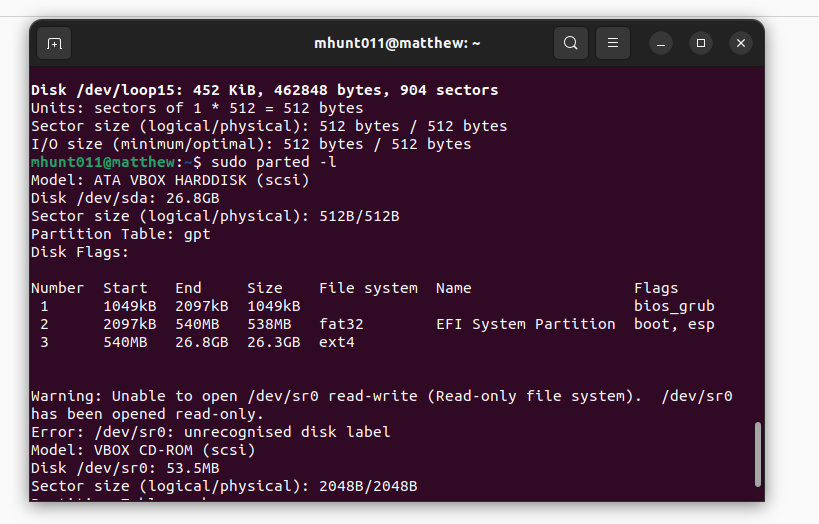
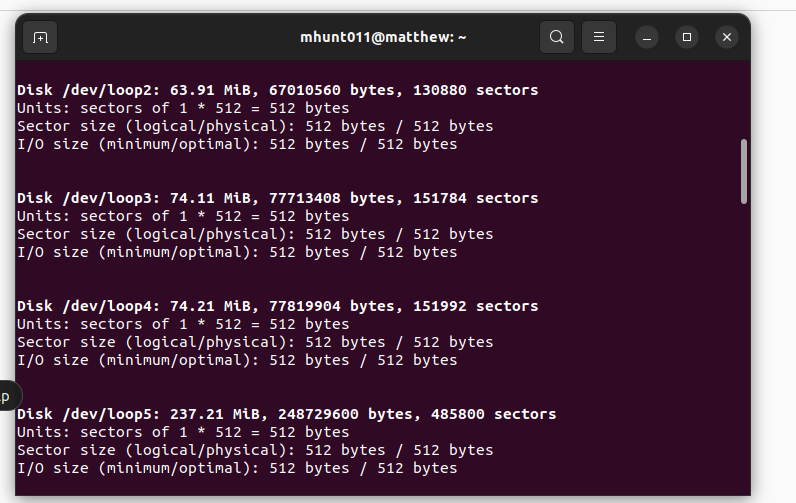
9. CYSE 270: Linux System for Cybersecurity
Assignment: Lab 4 – Group and User Accounts
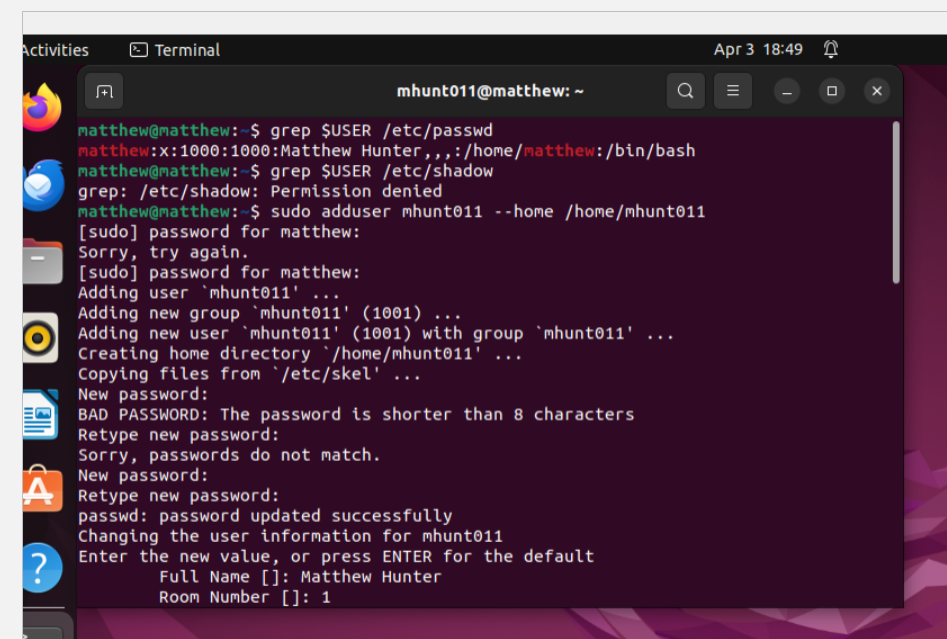
Skills
- Learning how to code on Linux
2. Learning how to code on Python
3. Learning how to get through passwords the tool called Brutus
Resume
Matthew Hunter
Chesapeake, VA 23322
7573241939
scion20172020@gmail.com
Skills
Scanner proficiency
Package and pallet staging
Cargo Sorting
Adherence to loading schedules
Following Instructions
Coding using Python and Linux
Experience
January 2022 – April 2024
bestbuy – Chesapeake, VA
Truck Unloader
January 2022 – December 2023
Cinema Cafe Edinburgh – Chesapeake, VA
Cook
August 2018 – November 2018
Subway – Chesapeake, VA
Sandwich Artist
Education and Training
Expected in December 2025
Old Dominion University Norfolk, VA
Cybersecurity
Reflection
Matthew Hunter
4/20/2024
Reflection
This semester and over my four years at Old Dominion University I have done a lot of research and have learned so much information about the social meaning of cybersecurity and the impact that cybersecurity-related technical systems have impacted our world and what we can do to help. I have also learned what my future holds with a degree in cyber security and the path I may want to take in the cyber field. There are a few different options that I may want to do first is a solutions engineer. This type of job requires many different skills, for example coding, and I have those types of skills, also being familiar with a lot of several types of cybersecurity. In my time at Old Dominion University, I have learned a lot of different things when it comes to these types of jobs and what they entail. A few examples of them is being familiar with frameworks.
I learned so many different things about cybersecurity which also helped me get a fellowship with a cyber company called WNK Aviation. I also did a ton of research on my favorite item which is the NIST Framework. I also did a lot of course work with coding.
The section I wrote here is from a past class which explains how much effort I use. “The NIST Cybersecurity Framework is used in many companies around the world. The NIST cybersecurity framework from what I have learned seems to be especially important in the cyber field. The NIST Cybersecurity Framework is a policy for guidance in protecting your company, business, etcetera. It is “5 functions to simplify and streamline the process of improving cybersecurity infrastructure.” There are many benefits to having the NIST Cybersecurity Framework and using it. Having the NIST Cybersecurity Framework can make you or whoever has it safe because of the Five Functions that it has which are, Identity, Protect, Detect, Respond, and Recover. The first function Identity stands for finding what is being hacked and what inside of the businesses are being hacked. For example, finding out what the threat level was and what was being hacked. Next the Protect function means, that the business who had the NIST Framework implemented in their company shows who should be notified, and what plans are in play just in case of a hack coming out of nowhere. The Detect function stands for monitoring all the systems to make sure nothing is wrong, and nothing is being hacked. Using the Detect function should be one of the most essential functions in my opinion. With this function you can stop hacks and if the hack gets through your defenses you need to have backup systems in place just in case the first set of equipment or programs fail. The Respond function contains the damage from the hack and what steps were taken once it occurred. For example, what is the first thing you are going to do when you find out you have been hacked, you need to find out what was taken or corrupted from your file and how much damage the hack did. You also need to make sure that if you are hacked to follow the right steps in preventing it from happening again and make sure that they are in order. Also, figuring out how the hack happened and what can be done to prevent it from ever happening again. Finally, the Recover function is where if the hack has passed through your systems or if it was stopped you need to focus on what to fix and focus on what to get back online first. These are the core values of the NIST Cybersecurity Framework. All jobs should have this cybersecurity framework implemented into their businesses or company’s because it can save so much from going wrong or being hacked.”
I have learned so much from this class and my other classes at Old Dominion University, especially on how to write and how to help my future progress. The reason that I am saying this is because for my field of work that I am hoping to go into, I am going to have to write a lot. I do not enjoy writing at all but the stuff that you taught in this class made it easier and a little more fun to write. I feel more informed from this class and am ready to move onto the next class and am starting to feel a little bit more confident in my writing abilities. I am glad to have taken this class and to have been taught a lot about what goes into writing. I am glad to have taken this class and cannot wait for many more to come. Thank you for teaching such a great class and I hope I can get you as a teacher again.