Cybersecurity Techniques and Operations
Course Background
This was a hands-on course that explores real-world cyber operations through offensive and defensive security practices. The course equips students with the technical and strategic skills essential for cybersecurity professionals, such as network traffic tracing, penetration testing, password cracking, wireless security, and digital steganography. It emphasizes active learning through practical lab work in a virtualized computing environment.
Assignment Reflection
Basic Linux Commands Lab
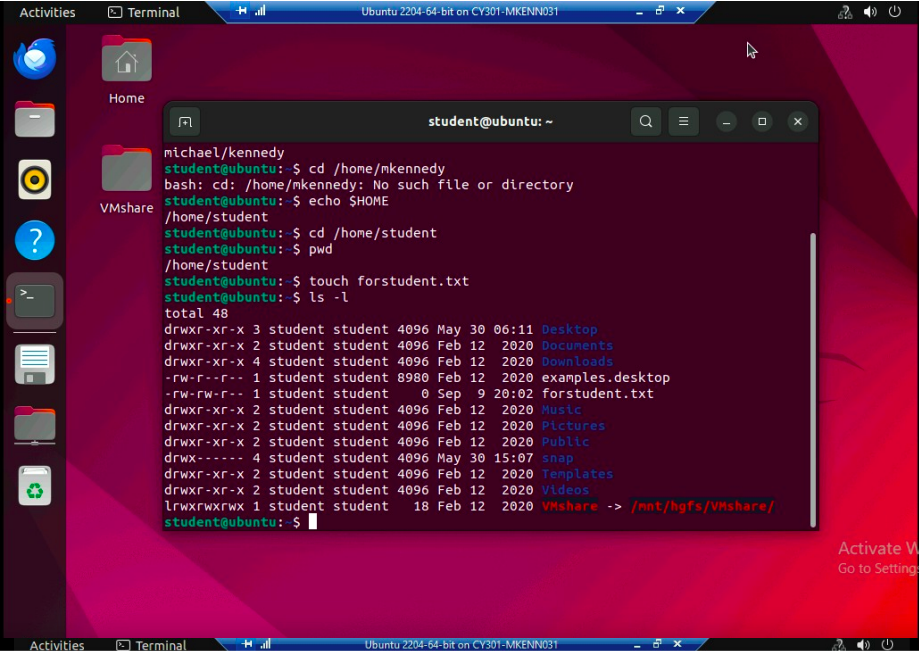
One of the foundational assignments I completed was Lab 1: Basic Linux Commands, where I used a Kali Linux VM in a controlled virtual lab environment (CCIA Hyper-V). This lab focused on practicing essential Linux terminal commands, skills critical in both offensive and defensive cybersecurity operations. The assignment was completed during the first few weeks of the semester, helping establish my comfort in a command-line interface early on. I successfully completed “Lab 1” and earned a score of 95% out of 100.
Relevance
Understanding basic Linux operations is critical for my cybersecurity career goals. Nearly all penetration testing and network analysis tools operate in a Linux environment. This experience not only supported my short-term academic success but also aligned with my long-term goal of working in cyber defense and red team engagements. It formed a technical foundation that will enable me to work with tools like Metasploit, Nmap, and Wireshark in more complex scenarios.
Explaining Commands
pwd: for current directory
echo: with name and escape characters
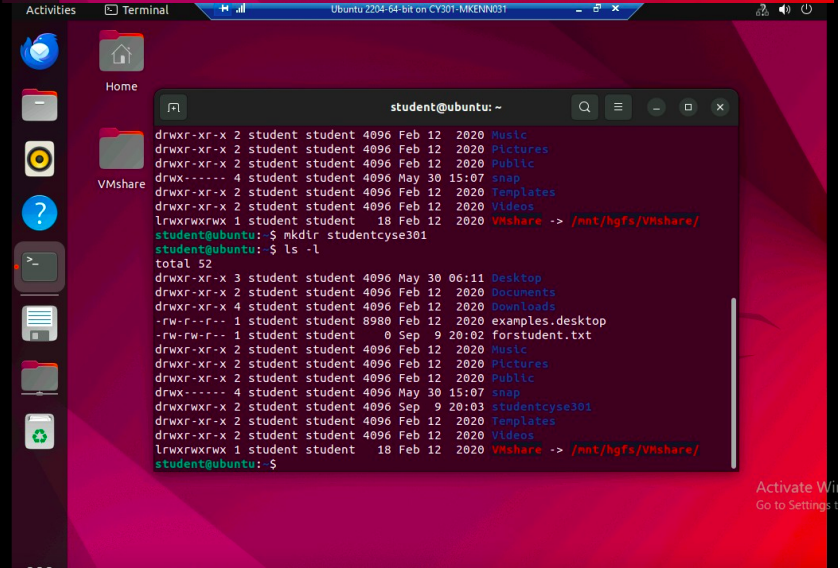
cd: navigation Output of creating a file and a directory using touch and mkdir, and verifying them with ls -l
Output of copying and manipulating /etc/passwd: head -n 6 passwd_MIDAS grep “www” passwd_MIDAS