Essential Work Habits
Throughout my academic and professional journey, I have demonstrated strong essential work habits critical to success in cybersecurity. I consistently work methodically and with attention to detail, as shown by high grades on cybersecurity exams and positive feedback during internships. I exhibit eagerness to explore technical questions thoroughly, maintaining adaptability and enthusiasm even when tackling complex problems. My strong analytical and diagnostic skills are proven through incident response exercises and vulnerability assessments conducted in coursework and real-world simulations. I stay updated on current vulnerabilities and security practices through continuous research and professional development. These habits ensure that I deliver reliable results and maintain a strong commitment to cybersecurity best practices.
Soft Skills
Communication and interpersonal abilities are essential in cybersecurity roles, and I have built a strong foundation in these areas. I have delivered technical presentations to classmates and professionals, effectively communicating complex cybersecurity concepts in an understandable manner. I have also demonstrated strong writing skills through research papers and technical documentation assignments. In team settings, I apply active listening skills to fully understand project requirements and client concerns, ensuring collaborative success. My ability to articulate and listen makes me an effective communicator both with technical teams and non-technical stakeholders.
Solid Technical Foundation
My technical training has provided me with a strong foundation across critical areas of cybersecurity. I have hands-on experience with the administration and management of Windows and Linux operating systems, networking principles, and virtualization tools such as VMware. I understand general programming concepts and have completed projects in languages like Java, Python, and Bash scripting. I am knowledgeable about the design and evaluation of system and network architectures, as demonstrated in coursework and lab simulations. Additionally, I understand the operations of firewalls, load balancers, routers, and switches, and how they contribute to securing and optimizing networks.
Detailed Knowledge of Key Technologies
I have gained detailed, hands-on experience with several key technologies essential to cybersecurity operations. My coursework and labs have included work with open-source security tools, Linux server management, Microsoft Active Directory configurations, and wireless security testing. I have practical experience in database modeling and securing web applications. I am familiar with compiled and interpreted languages like Java and Python and have applied this knowledge in security scripting tasks. Furthermore, I understand the principles behind network security implementations, social engineering risks, and physical security measures and have a foundational understanding of telephony technologies. These experiences give me a comprehensive view of cybersecurity systems and threats.
Work ethic
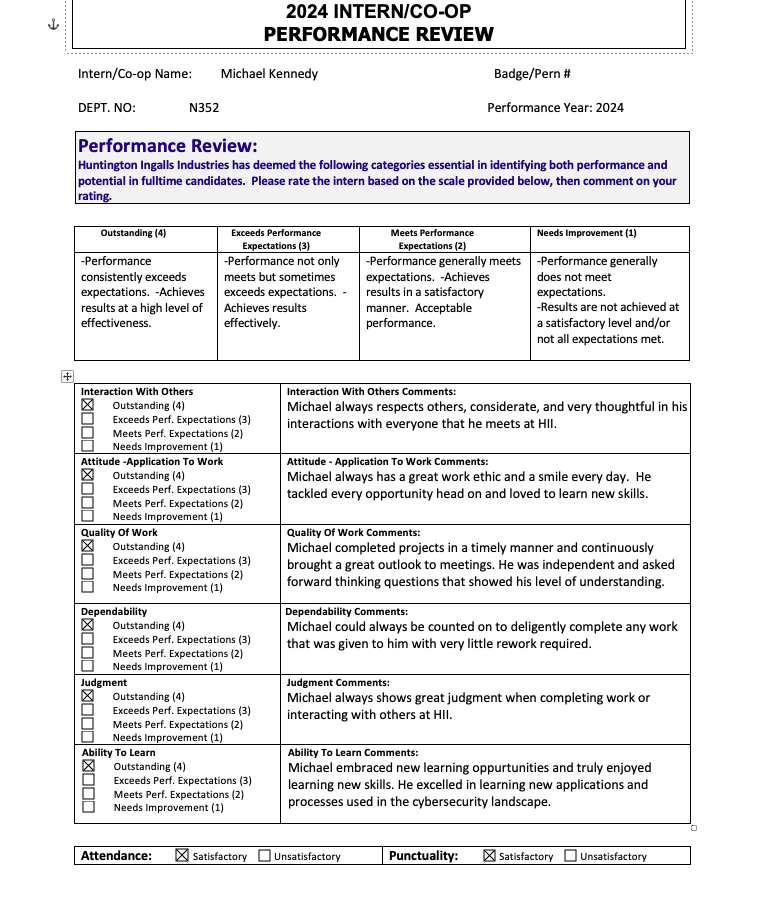
Here is a performance review reflecting my work ethic and skills:
Technical Skills
Threat Analysis
- Learned through: Professional work and academic courses Cybersecurity Fundamentals (CS462) and Cyber Strategy and Policy (CYSE525)
- Background: I applied threat analysis techniques during my internship at Huntington Ingalls Industries (HII) by assessing vulnerabilities, identifying potential risks, and contributing to proactive mitigation strategies, directly reducing exposure to security threats.
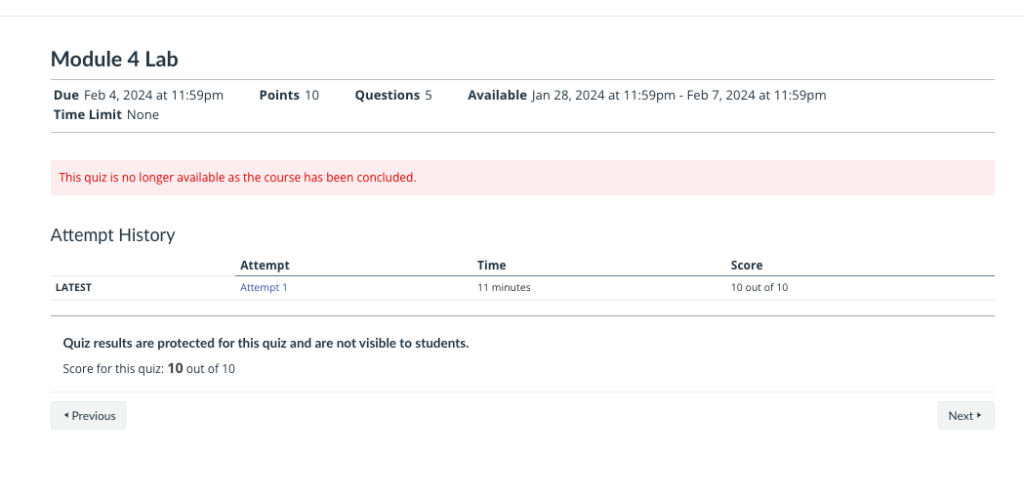
In this lab, I applied foundational concepts of cybersecurity to conduct a thorough threat analysis. The primary objective was to identify potential security threats within a given network environment, assess the vulnerabilities, and recommend appropriate mitigation strategies.
Network Security Monitoring
- Learned through: My role as a Network Administrator at Old Dominion University and IT Systems Administrator at the City of Petersburg.
- Background: I gained practical experience monitoring network security while configuring routers, switches, and firewalls, identifying potential network security incidents and minimizing downtime. I supported security protocols such as VPNs and firewalls to maintain secure access.
Identity & Access Management (IAM)
- Learned through: Hands-on work with Active Directory and security software management at City of Petersburg and Life Christian Academy.
- Background: I administered user accounts, set security policies, and managed access permissions to ensure compliance with security standards. This role gave me a foundational understanding of IAM practices and protocols.
Incident Response
- Learned through: My internship at HII.
- Background: I was involved in assisting with incident response efforts, where I supported teams during security audits and ensured that incidents were documented and responded to in compliance with industry standards, contributing to audit success.
Unfortunately, due to compliance and company policies, I have limited options for sharing or showcasing my work, including images, as it involves sensitive information.