Cybersecurity as a Social Science addresses the social, political, legal, criminological, and economic dimensions of cybersecurity through a social science framework. Students are introduced to a human factors approach to understanding cybersecurity threats. The class also explores how
cybersecurity is studied by social scientists in psychology, political science, criminology,
economics, sociology, international studies, and other social science disciplines
Cybersecurity as a Social Science was my first interdisciplinary course taken at ODU. The course taught me many concepts regarding interdisciplinary studies. One important factor for me was that Cybersecurity is an interdisciplinary field; meaning that it is comprised of many different areas of studies and can also be applied in different areas of study. Finding out that an individual can work in Cybersecurity and not have technical skills was intriguing. I was able to learn about different field and it allowed me to view Cybersecurity in a different scope. For this page I have decided to include my journal entries and essay papers so you can see my growth throughout this course
Journal Entry #1
Knowing myself, I have known for quite a while that Cybersecurity has been the career field that I wanted to pursue. The next question that would arise was “where in Cybersecurity would I like to explore?”. One thing I struggled to understand was networking, meaning that taking a networking focused route definitely wouldn’t be the right field to go. Although networking is the foundation of all things IT so learning it is essential.
One area I feel I excel in is critical thinking and analysis. Any areas that focus on risk management/analytics is where I would want to focus my career. Some of these jobs include Threat/Warning Analyst, Risk Management, Cyber Defense Analysis; these are all areas that require thinking like a criminal and have strong analytical skills in order to secure information systems. I also feel I display strong leadership qualities, so taking on a position in Overseeing and Governing is also an area that appeals to me.
Areas that I struggle in are programming, therefore I would try to stay away from any areas that would require me to build a system from the ground up; like an engineer. The reasoning for this is because programming causes me to experience burnout.

Journal Entry #2
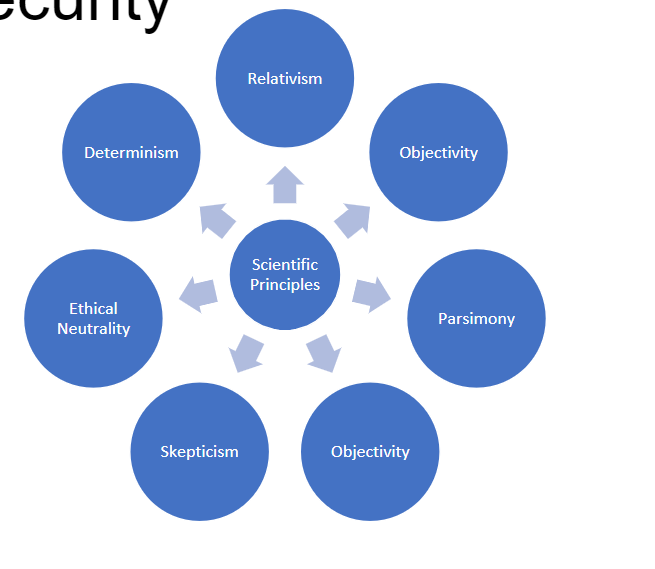
The Scientific Principles are as follows: Determinism, Relativism, Objectivity, Parsimony, Skepticism, Ethical and Neutrality. Through Module 2, I learned how the Scientific Principles can be related Cybersecurity; not through a technical approach but as a social science approach. Meaning all of the principles are applied to Cybersecurity through certain scopes
Relativism- the basic idea that all things are related.
- I like to think of this lens like a cause & effect. One thing happens which will eventually lead to the next. For example, crime is now able to be committed online. This means that cybercrime rates will now rise because it is easier to get away with crimes online . Social concepts are beginning to have a direct relationship with tech
Objectivity- refers to the way that scientists study topics in a value-free manner
- We have to separate our emotions from our research, the goal of scientists is to promote straight facts/decisions without obstructing research with personal bias involved. Kind of when a Jury or a Judge is making a decision; they are trying their best to base the decision using only the law and not their emotions. Of course we know that this isn’t always the case. Therefore making decisions on technology should only be based on our current knowledge without feelings involved.
- The module gives a great example:
- Should tech be used to monitor sex offenders?
- Obviously we know that sex offenders should be closely monitors because of the type of people they are, but we have to make sure we are providing only knowledge to making these decisions. For example: “tech should be used to monitor sex offenders because people will be able to know if there is a sex offender in their radius”
- Should tech be used to monitor sex offenders?
Parsimony- K.I.S.S- Keep it simple student
- Science is already confusing as is, the goal is to keep it as concise as possible to the common man. When creating theories or answering questions relating to the cyber world, although we could provide a textbook response, the goal is to keep it simple.
Empiricism- studying behavior that is real to our sense
- Our knowledge comes from what we have experienced. In short this means that, we cannot rely on our “gut-feelings” to understand/make decisions of the cyberworld
Ethical Neutrality- Is this ethical?
- We have to make sure that any decision made on the cyberspace is ethical; yes, we can make a decision that will definitely help us combat criminal but will it hurt our normal civilians as well?
- Ex: Blocking a certain website that cyber-criminals use to perform their illegal activities. However, we have to think about the normal civilians that also use this website, what it is used for, and how they could be affected by such a decision.
Determinism- this happened because of that
- The basic idea that behavior is based on a previous event in the past. People act on free-will and often make decision off of past events.
- For example:
- I want to hack into my school’s system and change my grade, however that might not be a good idea because someone has done it before and get expelled
- I want to place a ransomware attack on a big name company, people in Russia do it all the time and never get caught.
Journal Entry #3
The information displayed on PrivacyRights.org will be useful to researchers. The site breaks down the information from category, to state, timeline, you can search for breaches, etc. These filters will allow for researches to narrow down their research and get the information needed (anyone information needing dating back to 2005).
For example, let’s say a researcher is looking for data breeches that happened within the state of Texas; all the person will have to do is select Texas and more info will present itself.
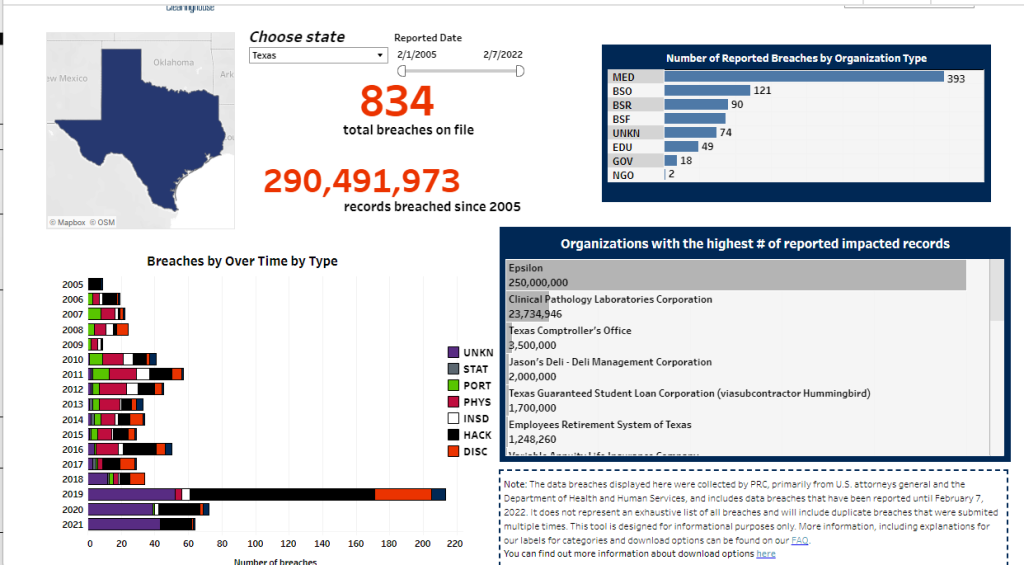
If was a researcher looking for information to study, I would be using this resource to the highest extent, it is deemed useful and resourceful.
Journal Entry #4
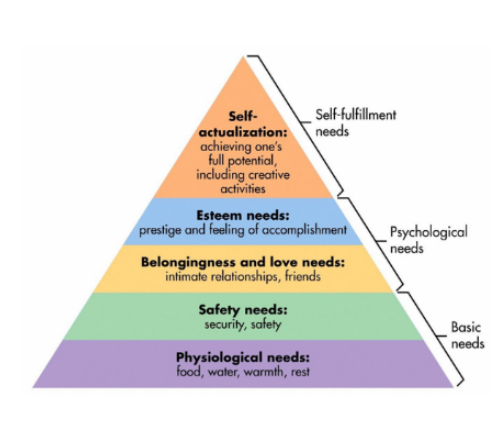
Maslow’s Hierarchy of needs consists of Physiological needs, Safety needs, belongingness and love needs. Although this is a theory that stems from Psychology, this can relate to technology as tech has a heavy influence on our lives in today’s age.
As stated in the slides, “digital technology has almost become a physiological need”. I sat and pondered on what that statement really meant, then it hit me; it has become entuned in our minds that we need to have access to the digital world or to some type of technology. I think about the times where I am just endlessly scrolling through social apps like TikTok, Instagram, Twitter; sometimes I could be scrolling for so long and even notice how much time has passed. When I really reflect, I am thinking about how I will swipe from one app and move on the next, like a muscle memory. Waking up in the morning the first thing I’ll do is check my social media platforms. All of these components are me fulfilling my physiological needs.
When thinking of Safety needs, I believe this is simply just ensuring that only what I want to display to the digital world is what is being displayed. I do this by making sure accounts are private, not too much is being shown in posts, and overall just making sure that I am not oversharing.
Belongingness and love needs is a stage that I feel affects many people. Everyone wants to feel like they belong and receive affection. In relation to the digital world, this is dictated by the number of followers an individual may have. People tend to believe that the amount of followers you have, puts in at the top of the “hierarchy of popularity”. To simply put it, no one likes to pay attention to the accounts with low following.
Esteem needs is defined as “prestige and feeling of accomplishment”, when posting on social media, people often have goals for the amount of interaction that they would like their posts to receive. For example, a person may want a certain number of likes on their Instagram post or a certain numbers of retweets on their Tweet. When achieving these goals we feel accomplished and when under performing some may begin to develop the mindset of “what can I do better”, this can cause an unhealthy relationship with the digital world as your mind can begin to become consumed over likes, shares, etc.
Self actualization is that awakening stage, that stage where you realize that the digital world is consuming our brains and that changes need to be made. Here you have come to the realization that you have control over the digital world and that it doesn’t control you, and as Maslow stated in this stage “all individuals strive for self-actualization, though few of us ever meet that need”.
Journal Entry #5
After reading and gaining a deeper understanding of the 7 different cybercriminal motives, here is my rank:
- Money
- I strongly believe that people are heavily by two things: poverty and greed. In fact those two things play hand-in-hand. If a person has the intelligence and are in poverty then they will begin to look for solutions to themselves out of that hole. If the person is fueled by greed then they will have that hunger for me. Who doesn’t like money? Especially when it is “free” and you are able to hide your tracks as well. Our society and economy is money-driven, the more money you have, the better off you are in this life.
- Entertainment
- Some criminals commit crimes simply because they are good at what they do and genuinely enjoy what they are doing. For some, cybercrime is nothing but a hobby; I believe that apart from being money driven, entertainment is what will drive someone to commit a cybercrime. An NBA player may play basketball because they make lots of money, but that doesn’t mean they enjoy it. Another NBA player may play basketball because they love it and being good at it is just a bonus.
- Revenge
- Lots of people react out of anger when someone has wronged; the first thing that may pop in their head is “how can I get back at this person?”. Not everyone acts on this instinct but when someone does you know that they are extremely fueled with anger. This is why I put revenge as 3 because if a person has remorse then there conscience will kick in before acting on the anger.
- Multiple reasons
- Personally, I believe that cybercriminals are first driven by one motive then there may be secondary motives. This belief is the reasoning for the ranking, I won’t fully eliminate the idea of multiple reasons but I do believe that this is rare.
- Political
- Not everyone is political, especially in today’s age. I believe that only a small number of cybercriminals are politically driven. The cybercrimes you hear that do relate to politics are usually major, but rare.
- Boredom
- You can closely relate boredom and entertainment. I would like to argue that both motives are to pass time. However with boredom there is no thrill that a criminal may receive in contrast to Entertainment.
- Recognition
- If I am doing something illegal, the last thing I would want to happen is to be recognized for my actions. Criminals like to do things in the dark and definitely do not like to draw attention to themselves. Personally, recognition shouldn’t even be on this list. Anyone that wants to be recognized for committing illegal acts for glory and praise is indeed a crazy person
Review Article #1
9/28/2023
Journal Entry #6
- Walmart
- A fake website may be walmart.eu , walmart is known to have a couple domain names but that is not one of them
- http rather than https. HTTP means that the site is not secured, being that walmart is a large corporation an http://walmart.com may be a fake
- Amazon
- A lot of phishing scams usually disguise themselves as Amazon, saying to redeem a gift card or that an order they have placed has been canceled. It’ll tell you to sign in and steal your information. Make sure to check the address bar and verify that everything is correct. Also if you have your password saved for that site, see if autofill recognizes this website address. If it doesn’t then the site is likely fake
- Abcnews.
- There was a website that acted as abcnews and posted fake stores or exaggerated stories of certain topics. However what set them apart was the fact that the website title was abc.com.co. The “.co” is what set them apart, however this is not as noticeable especially if the site is replicating to the point where they are posting their own news articles.
Journal Entry #7
Picture #1 – “When you’ve been goofing off all day in class in the professor begins going around looking at your work”
The body language of this picture made me think of someone that trying too hard to make it seem as if they are actually doing something, which is why I decided to give the meme this title.
Picture #2 – “When you lied on your resume to get a senior systems engineer position and you receive your first task”
The eyes of this dog gives me the idea of “What did I just get myself into”, due to this I thought of this hilarious meme title. Being a systems engineer is not easy work, so I believe this is the face you’ll make if you receive a task you cannot do.
Picture #3 – “Professional headshot day”
The smile, the body position, the alignment, the picture just gives off the vibe of professional headshot. Everyone smile!
Picture #4- “When you assignment is due at 11:59 and it is 11:57”
The main reason I chose this was not because of the person, but more so looking at the sun setting. This created the idea in my head of racing against of the clock.
Picture #5 – “When you’re trying to focus on the meeting but your phone keeps going off”
Ever been distracted because your phone keeps on going off? There’s no better way to resolve that by flipping it over so you can’t see any notifications. Don’t forget to turn your ringer off!
Picture #6 – “When your company has a strict no cell phone in the office policy and you sneak away to the bathroom”
The way the woman is smiling and she seems so confined to a space, it gave me the idea that she is doing something she is not supposed to. The bars of the stairs made me imagine a bathroom stall, I put the two ideas together and this was the final result.
Picture #7 – “It’s time to post the discussion board but nothing is flowing, so you begin to look at your classmates to get ideas”
The variety of Instagram posts gave me the idea of when you’re scrolling through DB posts
Picture #8 – “When you just returned from your 2-week vacation and you open your email for the first time since leaving”
After analyzing this picture, I kept on getting in my brain “brace for impact” vibes, the way the person was holding their computer and the way the body was leaned in.
Picture #9 – “When it’s presentation day and you’re working on finishing your assignment while waiting for your turn”
No one is paying attention to the person that is currently presenting, it seems as if they are all working on something on their own devices, this brought me back to the days when it was presentation day and class and some students still were not finished with their assignment
Picture #10 – “When you’re on your company trip and you have to take pictures”
This is the only reason why you’ll take pictures in the cold
Journal Entry #8
After watching this video, It has been confirmed to me that one thing the media will do is overexaggerate. The media has portrayed the image in our brains that cybersecurity is a really scary and cool field, that requires typing a bunch of keys into your keyboard, 1-2 minor setbacks, and completing hacks in under 2 minutes. Although this is not truly incorrect, it’s also not fully correct. For one, Cybersecurity can be really scary and cool but not in the way that we see in movies. Cybersecurity in the real world is not has graphical images like how the movies portray. In every Cybersecurity movie, you’re always going to see the hacker type really fast on their computer and after a couple minutes in say “I’m in”. This process is not as quick, obviously the movies scale it down for the sake of time but this is important to note. I really enjoyed watching this video, I feel Keren did a great job breaking down each scene and explaining what was wrong and what was good. Her being a professional hacker, I’m sure she was cringing internally to a couple of the scenes that were present.
As I think about how the media exaggerated Cybersecurity, it makes me think about just how much the media can exaggerate other topics and issues. This is why as people living a media influenced world we always need to make sure that we are fact checking the information being presented to us.

Journal Entry #9
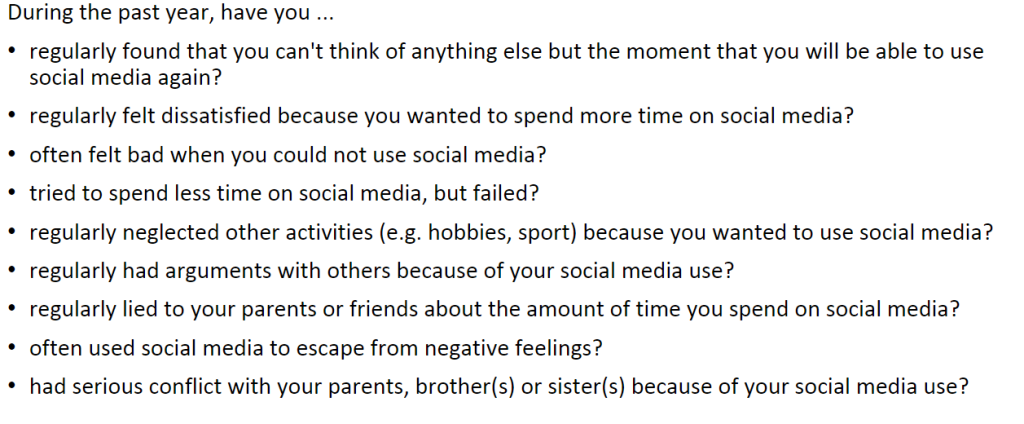
I completed the social media scale and could conclude that none of these questions applied to my life to the point where I could answer yes. Reading these questions made me realize just how far gone people are in this world. To even be that deeply involved in social media to that extent is even scary for me. The most surprising question to me was the question that mentioned serious conflict due to media usage. Overall, I think this scale is not a good one; the questions present are too extreme and need to be scaled down more. I feel lots of people won’t be able to apply these questions too themselves and will believe that they don’t have a problem with their media usage when that is not the case. I believe that there are different patterns of media usage across the world because not everywhere is the same. Some countries are more advanced than others in terms of tech, other countries have laws that prohibit media usage and excessive usage, also some countries are just not as reliant as others on the usage of social media, lastly the fear of the unknown: some countries may fear the dangers that come with social media and may choose to escape by not using it at all. I believe that all these factors contribute to the differences in media usage across the world.
Article Review #2
Journal Entry #10
The video describes a cybersecurity analyst as the “first line of defense in monitoring a network”. Describing an analyst as someone that is constantly monitoring networks, educating employees, and checking for flaws. Although the need for analysts are high, some areas have a higher demand than other and will often pay more. The reason for this is the areas are high in population and technology making them an easy target for cyber related attacks. Unlike most careers that require a degree, you do not necessarily require a degree to get into the IT/Cyber work field; a person can enter the field just by getting certified. In fact the speaker in the video even mentions not going to school to accumulate debt in you plan on working IT but rather just get certified. Our resume can be our best friend and also our worst enemy, you have to ensure that your resume in is tip-top shape but employers highly use it as a means of hiring or not hiring you.
Journal Entry #11
As I began reading through the article, one of the points that stood out to me was the emphasis between regular cybersecurity and social cybersecurity. Instead of humans hacking tech, social cybersecurity refers to humans hacking other humans. After reading this, I really had to sit and reflect on that statement as humans being the victims/target is something that is not stressed enough. The article does a great job of explaining social cybersecurity and its emergence, consequences, and how it can be used. Our greatest enemies are not outside forces but instead it is ourselves, if we are not careful hackers can use our own selves to manipulate and exploit especially in the military world. “Leaders must understand social cybersecurity in order to defend these internal weaknesses from external manipulation”. I believe that it is important that we educate the world that humans can hack other humans. Such a statement sounds silly, but it is very true. I think of the amount of people that have been social engineered and I know that there is a problem present.
Journal Entry #12
In this article a study is conducted on programs that consist of different companies to test for bugs within their code/network, the article analyzes types of companies, the age of companies, and so on in order to determine the type of company that would be the most susceptible to attacks. These type of programs are referred to as bug bounties; defined as, “programs where gig economy security researchers are compensated for pinpointing and explaining vulnerabilities in company code bases”. The article noted that 93% of companies lack Vulnerability Disclosure Policies (VDPs), these policies allow for researchers to submit vulnerabilities to these companies without having to worry about repercussions. The article dives deeper in to bug bounties, giving a background insight on how these programs came about. The article also continued to share reasons as to why a company would participate, the effects of participation, and why hackers (bounties) decided to create such programs. Upon concluding the study, the researchers were left with six findings. First is that hackers are price insensitive, meaning that they set prices on what they feel is right and nothing right, hackers also have the leverage to do this due to the number of available hackers being scarce. Second was that bug bounties are effective for all companies. Third, companies in certain industries will have fewer reports. Fourth, new programs have a statistically insignificant impact on the number of reports companies receive. Fifth is that over time programs will begin to receive fewer reports . Lasty, was that the article acknowledged their own fault and mentioned that there is little knowledge about bug bounty markets, suggesting that future research should have a focus on identifying and measuring what factors determine hacker supply.
Journal Entry #13
The Marxian economic theory states that “those with power exploit those without power for economic gain”. The conflict theory states that “society can be understood through power differences and inequalities”. In the letter, the company is that is sending the letter is the power/higher power, the recipients/customers are the ones with lower power in this scenario. The company knows that they need to retain the trust of their customers for future monetary gain, in order to do that they will need to remain transparent to their customer/lower case. I believe this is the main reason for the letter, not for the protection of the customers, but just the company thinking in terms of the future and knowing that this was the best decision to make. The Laissez-faire economic theory states that “governments should not intervene in the economy except to protect individual rights”. Symbolic interactionism states that “society can be understood through interactions between individuals”. In the letter it was mentioned that they have contacted and will cooperate with the local law enforcement. In this scenario the government was staying out of normal economic ventures until information was leaked (individual rights), due to this they had to step in to help with investigation. The response to how the customers will react to the letter is something that will need to be watched closely, some may be outraged, others might be understanding, and others may cut ties with the company as a whole. Hearing that the law has stepped in could even possibly ease them a little bit, the reaction (symbolic interactionism) is something that I am sure is highly anticipated for the company.
Journal Entry #14
The first most serious violation is using torrent services, torrent services are really started to become a common thing. At first it was just for already released movies and tv shows, but now that streaming has become popular, you can now use torrent services for watching live streams such as sports games, news broadcasts etc. People hear the word free and don’t actually realize that they are unknowingly committing an illegal act and stealing profits from networks and creators. Next is extracting audio files from YouTube, many people like to extract music from YouTube to have a personal copy of the song, whether it be for a playlist, creation of a CD, and just wanting a downloaded version. Most times in order to even extract this audio, you have to use a 3rd party site which is probably 10/10 illegal. Illegal searches on the Internet; this one is an interesting one to me. Although this is illegal, I believe that most times when an individual is conducting an illegal search it is genuinely because they are curious rather than trying to commit an illegal act. Although it is unfortunate, I understand that the proper precautions need to be set and that is why activity after these searchers can be monitored. Bullying and trolling is common sense in today’s world, but even though it is common sense, it seems that as the social media world grows, so does bullying. The reason why people bully over the internet is because the chances of getting caught are significantly reduced compared to bullying in person. Unfortunately the amount of cyberbullies are so large that it is rare to see someone get apprehended for the act. Collecting information about people younger than 13 is another one of those common sense crimes. The unfortunate thing is that some children lie about their age to join a social media platform, this is a common thing among children.
Career Professional Paper
Journal Entry #15
Davin Teo was a digital forensics scientists that had been in the field for 15 years. Teo mentioned that in his time there was no coursework to get into digital forensics, stating that “you either fall into it or get put into it”. I find it very interesting that Davin had a career in accounting, but because he didn’t just limit himself and started to apply himself in IT, he was able to be presented with more opportunities in life landing himself a position with one of the big 4 account firms. I feel David’s story is one that many can relate to; often times we see ourselves venturing in a career field where we don’t really feel is for us, I believe the difference between Davin and other’s is that Davin didn’t remain stagnant, he continued trying out various things until he finally found his “niche”. Davin is a reminder that your degree does not define who you are, a reminder to be the change that you want to happen. Due to his basic knowledge of IT, Tao was able to dip his foot into something greater along the way. We shouldn’t be afraid to try new things.