Task A – Get started with Wireshark
Q1. How many packets are captured in total? How many packets are displayed?
Q2. Apply “ICMP” as a display filter in Wireshark. Then repeat the previous question
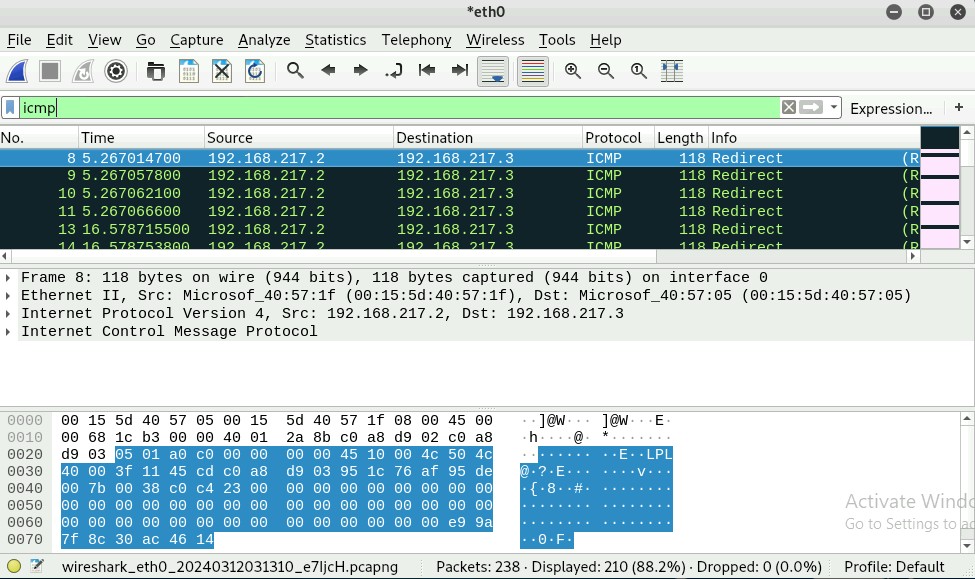
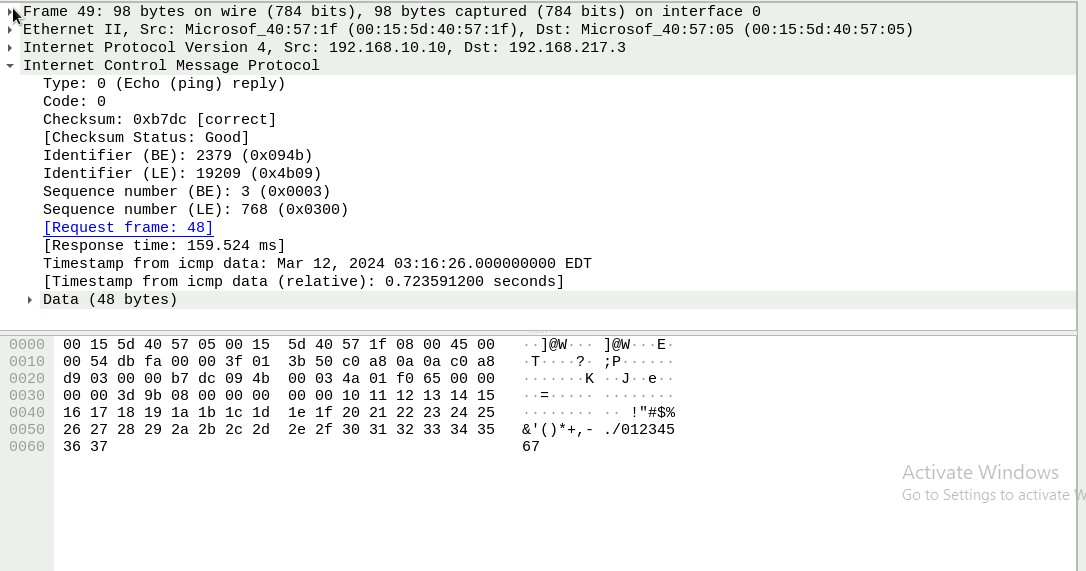
Q3. Select an Echo (reply) message from the list. What are the source and
destination IPs of this packet? What are the sequence number and the size of the
data? What is the response time?
Sequence Number: (BE): 3 (0x0003)
Sequence Number: (LE): 768 (0x0300)
The response time is 159.524 ms
The size of the data is 48 bytes
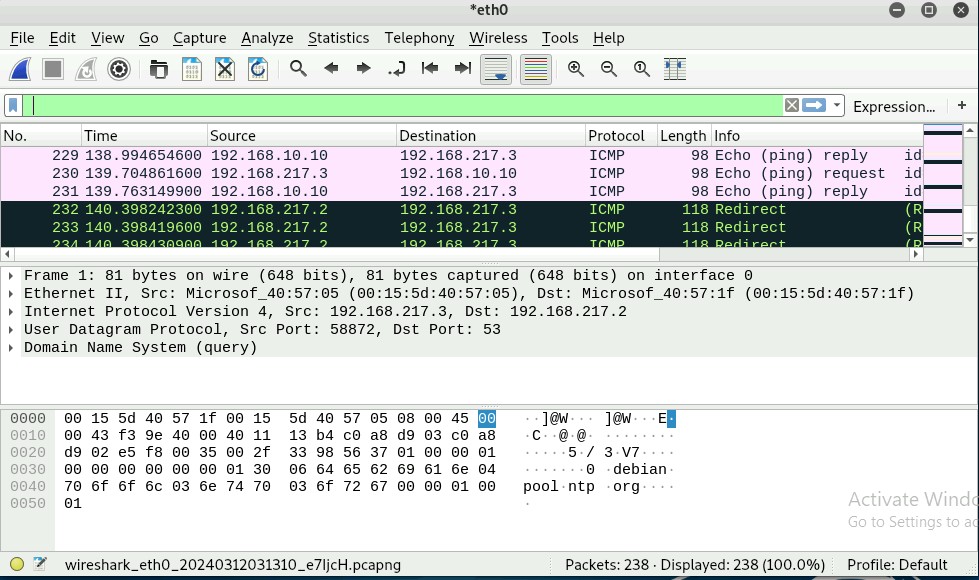
Q4. Apply “DNS” as a display filter in Wireshark. How many packets are displayed?
Out of 238 packets, there are 4(1.7%) DNS packets displayed.
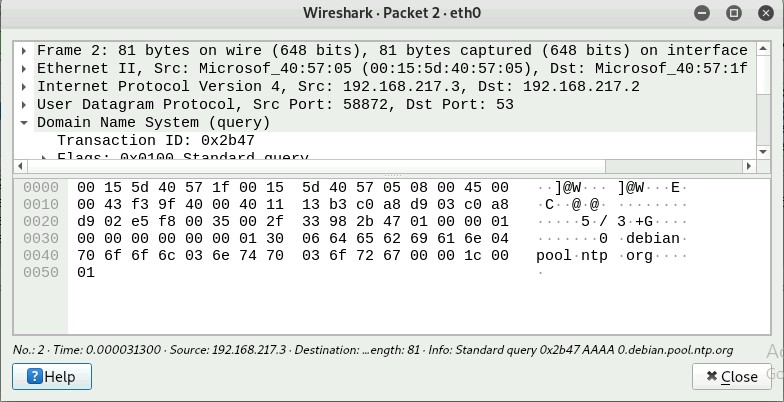
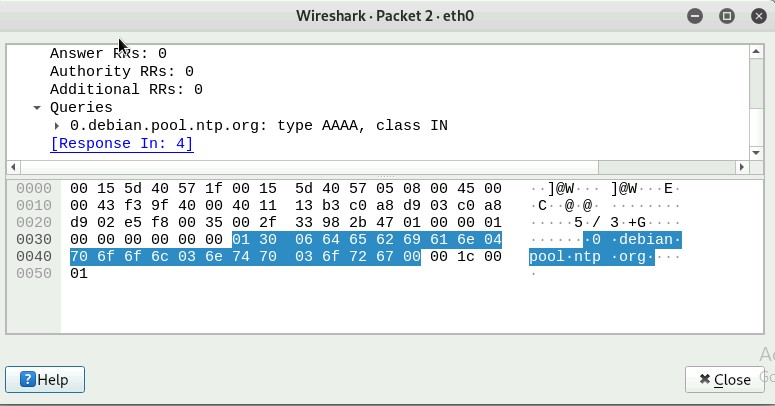
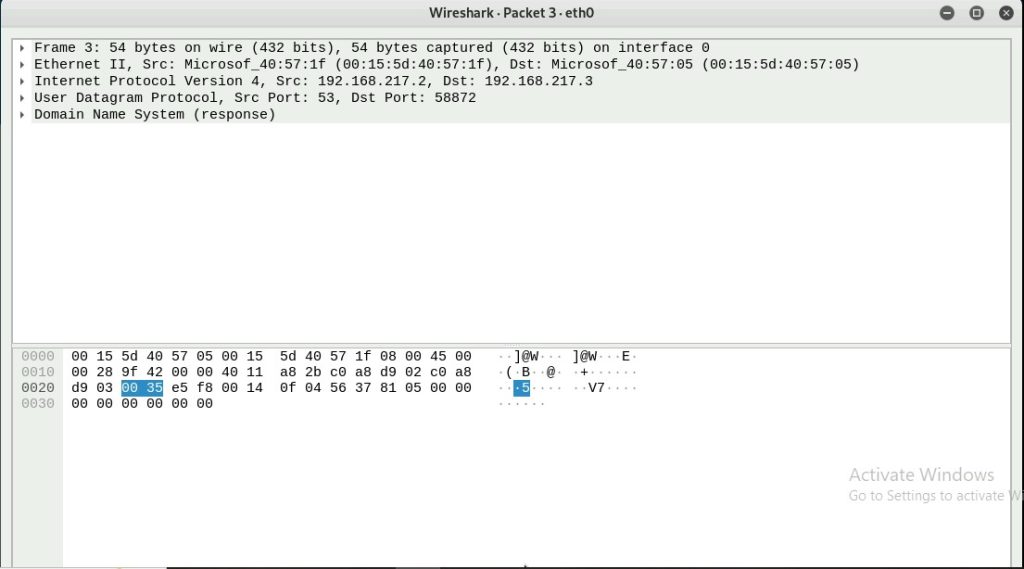
Q5. Find a DNS query packet. What is the domain name this host is trying to
resolve? What is the source IP and port number, destination IP and port number?
Please express in the format: IP: port.
The domain name the host is trying to resolve is 0.debian.pool.ntp.org
The source IP is 192.168.217.3 and the port number is 58872
217.3:55872
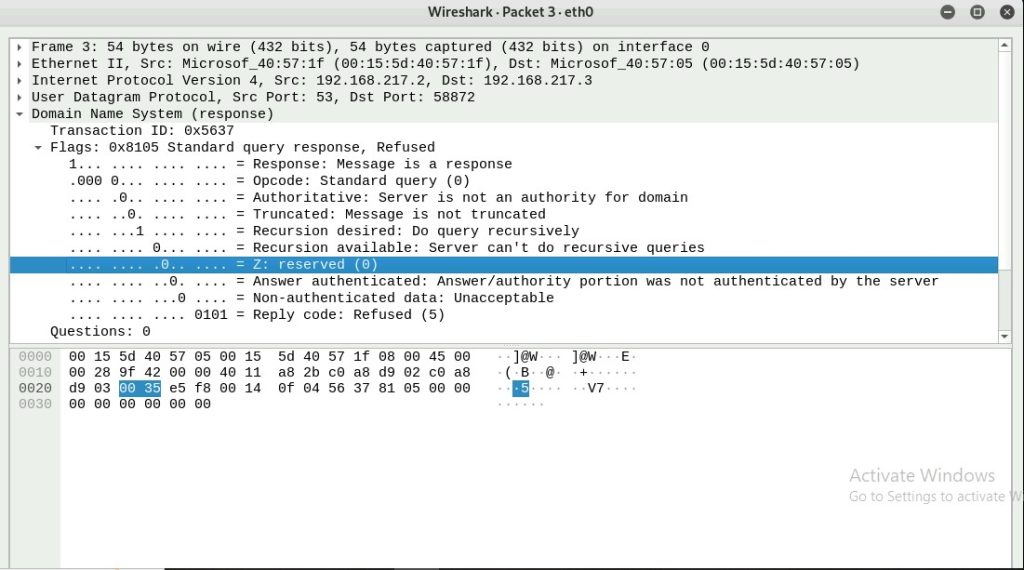
Q6. Find the corresponding DNS response to the query you selected at the previous
step, and what is the source IP and port number, destination IP, and port number?
What is the message replied to from the DNS server?
The source IP is 192.168.217.2 and the source port number is 53. The destination
IP is 192.168.217.3 and the port number is 58872.
The message from the DNS server is 58872
Sniff ICMP traffic (10 + 10 = 20 points)
Open two terminals on External Kali VM. Use one ping Ubuntu VM, and use the
other ping Internal Kali
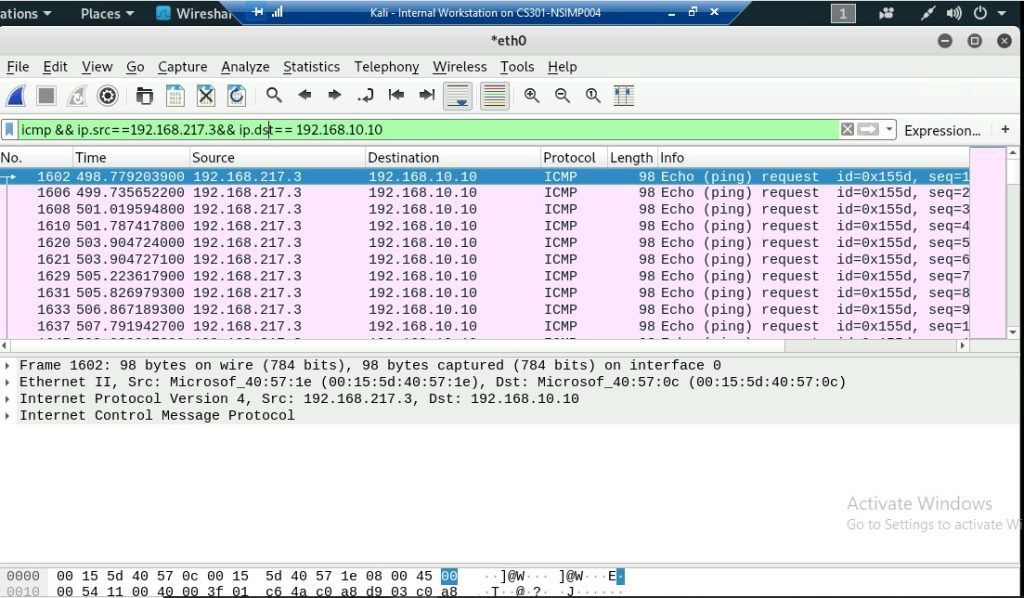
This is the screenshot of Internal Kali being pinged 192.168.10.13
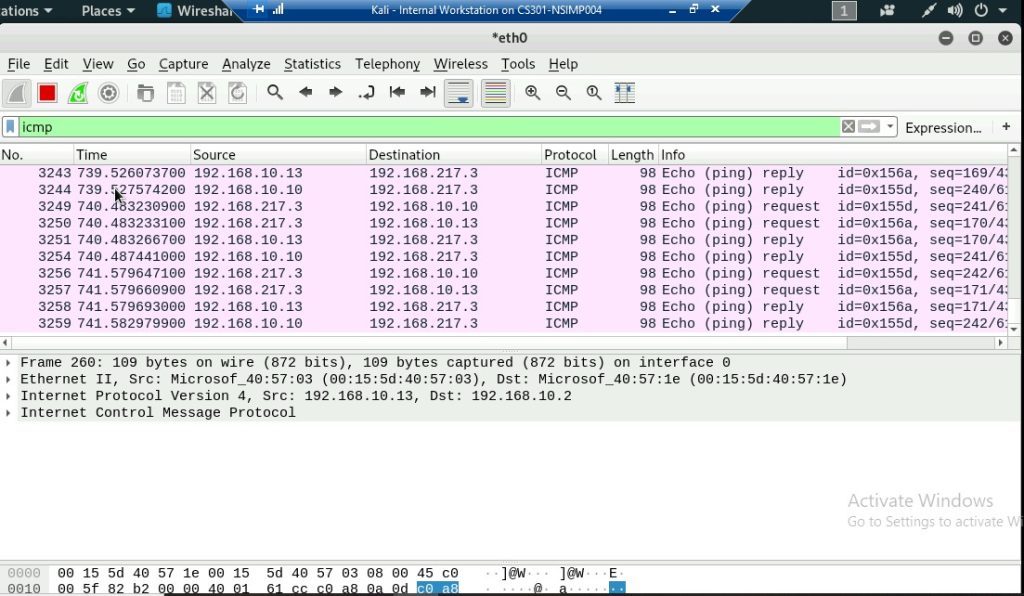
This is a screenshot of Ubuntu VM being pinged 192.168.10.10
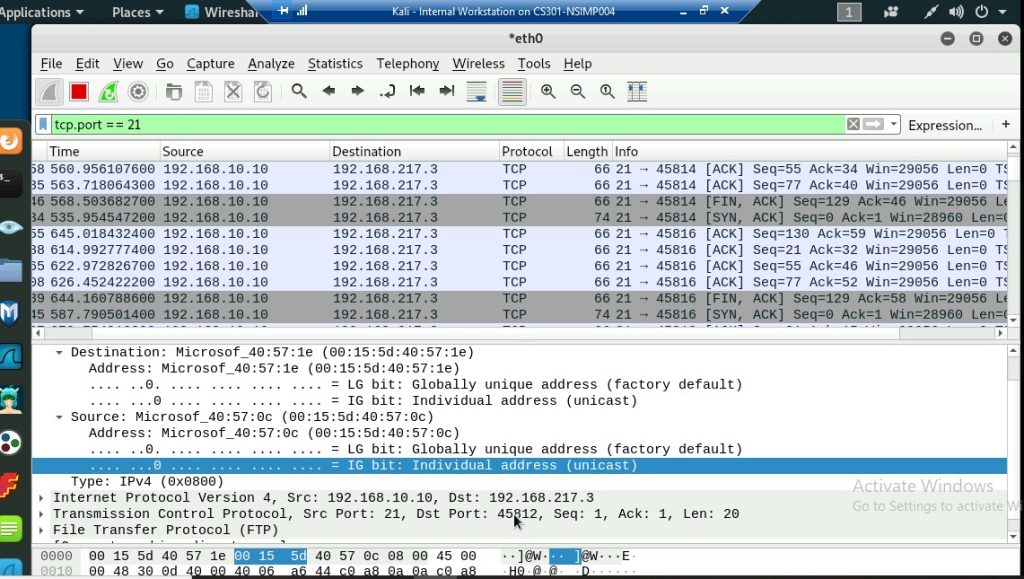
a. Apply proper display or capture filter on Internal Kali VM to show active ICMP traffic.
b. Apply proper display or capture filter on Internal Kali VM that ONLY displays ICMP request originated from External Kali VM and goes to Ubuntu 64-bit VM.
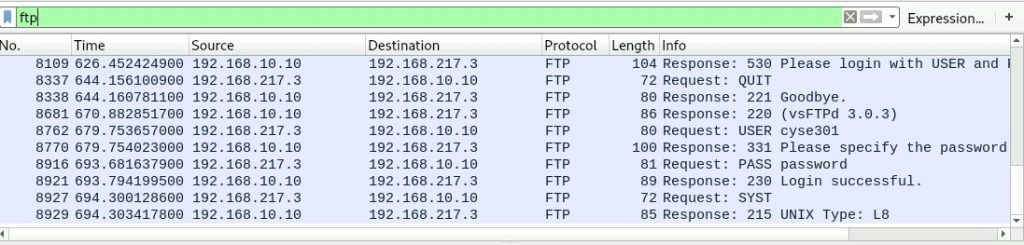
2. Sniff FTP traffic (10 + 15 + 15 = 40 pts points
a. Ubuntu VM is also serving as an FTP server inside the LAN network. Now, you
need to use External Kali to access this FTP server by using the command: ftp
[ip_addr of ubuntu VM]. The username for the FTP server is cyse301, and the
password is password. You can follow the steps below to access the FTP server.
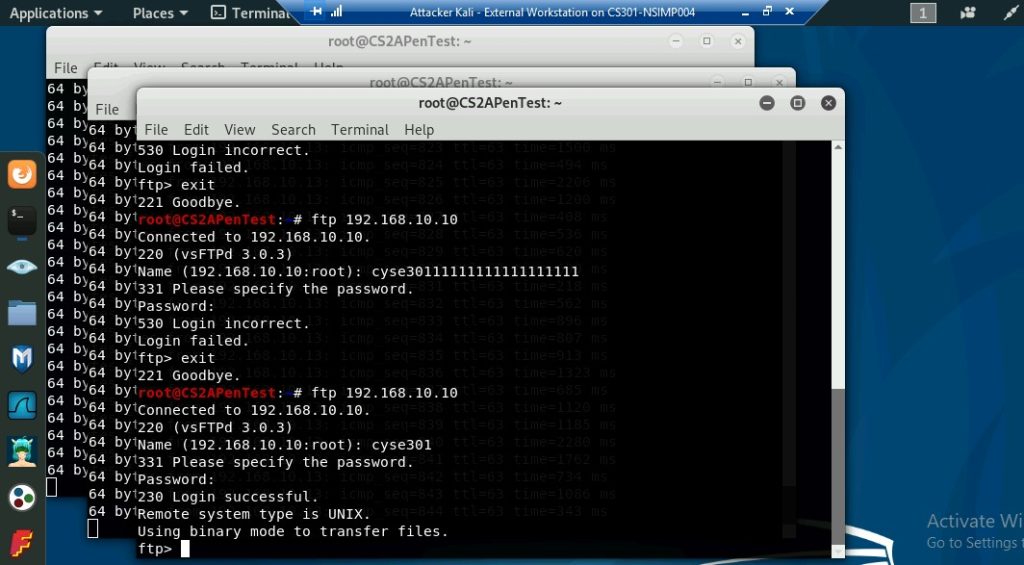
b. Unfortunately, Internal Kali, the attacker, is also sniffing to the communication.
Therefore, all of your communication is exposed to the attacker. Now, you need to
find out the password used by External Kali to access the FTP server from the
intercepted traffic on Internal Kali. You need to screenshot and explain how you find
the password.
I found the password by typing in ftp on wireshark and it displayed the username and password used by the external kali.
c. After you successfully find the username & password from the FTP traffic, repeat the previous step (2. a), and use your MIDAS ID as the username and UIN as the password to reaccess the FTP server from External Kali. Although External Kali may not access the FTP server, you need to intercept the packets containing these“secrets” from the attacker VM, which is Internal Kali.