Author's posts
Mar 05
Research Paper Proposal
Please complete the following information: Student Name: Nadia Simpson Research Name: Attack on Microsoft Servers Research Objectives: 1. Talk about the vulnerabilities with Microsoft servers that could have caused the attack 2. Explain the methods that the hackers used to exploit the system which led to the breach 3. The steps that Microsoft took to …
Mar 05
Research Paper- CYSE280
Abstract: This paper will be discussing the 2021 Microsoft Exchange Server breach Introduction I chose to write about the 2021 Microsoft Exchange Server which impacted both the government and financial sector which interested me because of the methods that hacker group used in order to infiltrate the exchange servers and the impacts of the breach …
Mar 05
Lab 2 | Active and Vulnerability Scanning
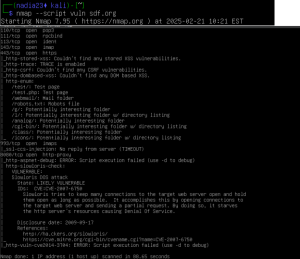
Old Dominion UniversityCYSE 450: Ethical Hacking and Penetration TestingLab 1: Active Reconnaissance and Vulnerability ScanningHandout Date: February 06, 2025Due Date: February 20, 2025, 11:59 pmTotal Points: 30 Question 1: Active Scanning T1: Using both host and dig commands, demonstrate whether the host sdf.org is live or not. Attach screenshots showing the results. 4 points • …
Mar 05
Lab 1 | Lab Preparation
Old Dominion UniversityCYSE 450: Ethical Hacking and Penetration TestingLab 1: Lab PreparationHandout Date: January 23, 2025Due Date: January 30, 2025, 11:59 pmTotal Points : 10 Following the tutorials shared in the Week 0 module install the following softwares: VirtualBox/UTM, Kali Linux( In VirtualBox/UTM, Metasploitable 2 (in VirtualBox / UTM), Nmap (in Kali Linux ). Run …
Mar 05
Assignment 4: Ethical Hacking
At the end of this module, each student must submit a report indicating thecompletion of the followingtasks. Make sure you take screenshots as proof.You need to power on the following VMs for this assignment. Task A. Exploit SMB on Windows XP with Metasploit (20 pt, 2pt each) In this task, you need to complete the …
Mar 05
Assignment 6 – Hide your secret!
Assignment details: Lab Preparation:• For students who are using Windows Laptop/Desktop, you can choose to complete the assignmentlocally. You can download the required lab files from Canvas (“M6 – Lab files.zip”).• [Mac User Only] Access a Windows VM named “ODU Labs General” in the group “ODU GeneralLabs WorkSpace” on ODU MoVE (move.odu.edu). This VM provides …
Mar 05
Assignment #7 – Make your own VPN server
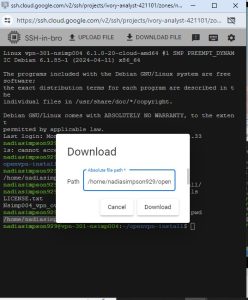
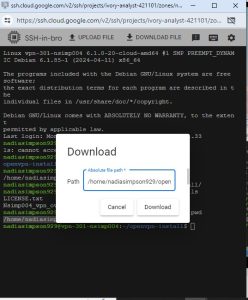
Assignment directions: (35pt ) Create a Linux Instance on GCP named vpn-301-YourMIDAS (showthe IP address and region assigned for the VM). (35pt ) Configure the server and generate a client named “yourMidas_vpn.ovpn” and download it from the server. (30 pt) Connect to your VPN server from a laptop or cell phone client and show the …
Mar 05
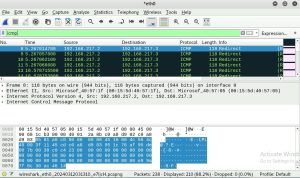
Assignment 2: Traffic Tracing and Sniffing
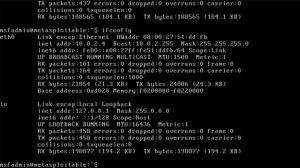
Task A – Get started with Wireshark Q1. How many packets are captured in total? How many packets are displayed? Q2. Apply “ICMP” as a display filter in Wireshark. Then repeat the previous question Q3. Select an Echo (reply) message from the list. What are the source anddestination IPs of this packet? What are the …
Mar 05
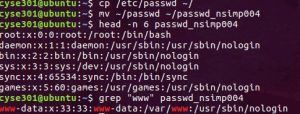
Assignment #1 – Basic Linux Commands
Task A: Practice with the Basic Linux Commands You can take one screenshot to cover the answer for multiple tasks. 2. (10 pt) Display your current directory in a terminal 3. (10 pt) Use the echo command to print your name to the console. 4. (10 pt) Display your first and last names in two …
Mar 05
Short Research Paper 2
Nadia SimpsonOld Dominion UniversityCYSE300Malik Gladden9/17/2023 As organizations increasingly rely on digital platforms to handle sensitive data of their users, the importance of creating strong cybersecurity policies for information systems has never been more critical. An effective cybersecurity policy ensures that all components of an organization’s IT infrastructure, especially high value systems such as web, database, …