Week 1:
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
Certain areas that I would like to focus my career on is protection and defense because your responsibility is to protect, identify, and analyze risks to technology systems or networks. In addition, investigating cybersecurity events or crimes related to technology systems and networks. The most appealing role is defensive cybersecurity because your responsible for analyzing data collected from various cybersecurity defense tools to mitigate risks. It seems fun to find ways of mitigating risks and trying to find different solutions. The least appealing role to me is cyber operations planning. Honestly, this is because it seems like a heavy workload developing cybersecurity operations plans. You have to participate in targeting selection, validation, and synchronization; and enable integration during the execution of cyber actions. This responsibility seems pretty stressful.
Week 2:
Explain how the principles of science relate to cybersecurity.
Relativism relates to cybersecurity by understanding how one system leads to changes in other systems. From our modules it states that objectivity is critical to those studying cybersecurity from a social science perspective in doing their research while addressing issues related to cybersecurity. Parsimony is more challenging to keep an explanation as simple as possible related to why people commit cybercrimes. Empiricism could have a negative effect related to cybersecurity because you shouldn’t rely on opinions or hunches to frame understanding of cybercrime and cybersecurity. Ethical neutrality is beneficial when studying cybercrime through a social science lens because it allows you to find ethical issues. Determinism is beneficial for cybersecurity because it helps us have a better understanding of why people choose to hack and do illegal things related to important data and information of others.
Week 3:
Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches? Enter a paragraph in your journal.
After visiting PrivacyRights.org, it provided a lot of important information about data breaches. This information can be very helpful and useful for researchers who want to study breaches because the website provides different kinds of datasets and graphs of breaches that occurred from two decades ago to present day. It shows what locations most breaches have occurred in the United States. For example, it provides a map of all the states in the U.S. and what states had data breaches reported more frequently than other states. The website also includes what type of breaches they were and what organizations were affected. After analyzing the data that is provided researchers may be able to identify trends and patterns of the most frequent breaches and their causes which could be hacking, human error, etc. They could also understand what kinds of information seem to be most at risk. This knowledge can help researchers predict future vulnerabilities and come up with more cybersecurity strategies and solutions.
Week 4:
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
The experiences I have had with technology are related to Maslow’s Hierarchy of Needs. Starting with the basic needs of security and safety, I have experienced small viruses on my phone from random advertisements that would pop up quickly in the top right corner of my screen while I was researching certain websites, and I had accidentally clicked on the advertisement from it being in the way of where I tap my finger on the screen. Then I would get a notification that a virus has affected my device. I never had much knowledge during those times on how to prevent viruses from occurring so I usually would become very irritated when it happened. Also, I can relate the most to the physiological need of technology. Being able to have a phone for years has created a bad habit of wanting to use it most of the time every day of my life. Especially since social media is very popular now. Times when I have misplaced my phone, I would become worried and upset because I would feel like I am missing out on different things from social media or being contacted from my friends and family. Even though I have a bad habit of scrolling on social media for too long I still become drained after. I usually am affected negatively more than it is positive. The main problems I have experienced are comparing myself and life with others and being affected by other people’s opinions from a general post that pops up on my feed. Social media can be very toxic because of people’s opinions whether that be clothing, the lifestyle you have, or the way you look. This has affected my self-esteem in the past, I believe that it can be very difficult for a lot of people to reach self-actualization and become truly satisfied with what they have. This is because most care about being judged by others, comparing their lives, and feeling like everything is a competition. If these problems never existed, I don’t think people would continue to desire for more after they have already achieved their main goals.
Week 5:
Review the articles linked with each individual motive in the presentation page or Slide #3. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
1.For money: Financial gain is the main motivation behind a lot of cybercrimes. To steal money from people and businesses so they can earn as much money as possible for whatever they want to spend it on.
2.Political: Some cyberattacks are motivated by political goals or ideological beliefs. In order to further their goals or express disapproval of policies, hacktivist organizations attack organizations. Younger hackers, for example, have embraced the hacktivism trend, which has increased difficulties in cybersecurity.
3.Recognition: Some people commit cybercrimes in order to become well-known or respected in particular societies. Also, to have that feeling of fitting in with a particular group.
4. Revenge: Cybercrimes against alleged wrongdoers might be motivated by personal grudges. For example, victims of revenge porn frequently feel let down by the legal system, resulting in the motivations of these online crimes.
5. Entertainment: Some hackers commit cybercrimes for fun or because they are bored. The person responsible for the 700 million profile data scrape on LinkedIn stated that they did it “for fun.” Which doesn’t really make sense to me because there are plenty of other things to do for fun. I feel that the man still knew that he wasn’t supposed to collect that much data of other people’s personal information.
6.Boredom: It’s never an excuse to engage in cyberbullying just because someone is bored. It is disrespectful and affects others negatively mentally and physically. Also, parents and guardians of children should work harder to protect their children from social media and track what they are accessing since social media is frequently used in today’s time.
7. Mutiple Reasons: Some of the causes of cybercrime are difficult to understand. Gaining more knowledge about the several reasons people hack will help people better understand this complex problem.
Week 6:
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?
https://www.tiffany.com/? This website is real because it displays HTTPs with the official branding name.
TiffanyCoShop.com (Fake luxury retailer store) this URL has extra characters and lower quality design which gives a sign that this is a fake website.
https://www.starbucks.com/ This website is real because it displays HTTPS and has a consistent design with no misspelling.
https://www.nike.com/ This website is real because it has no misspelling ,displays HTTPS, and its shows all of their contact information at the bottom of the website.
In the screenshot below, I think this website is fake because it offers deal with large discounts for sneakers that are usually way higher in price.
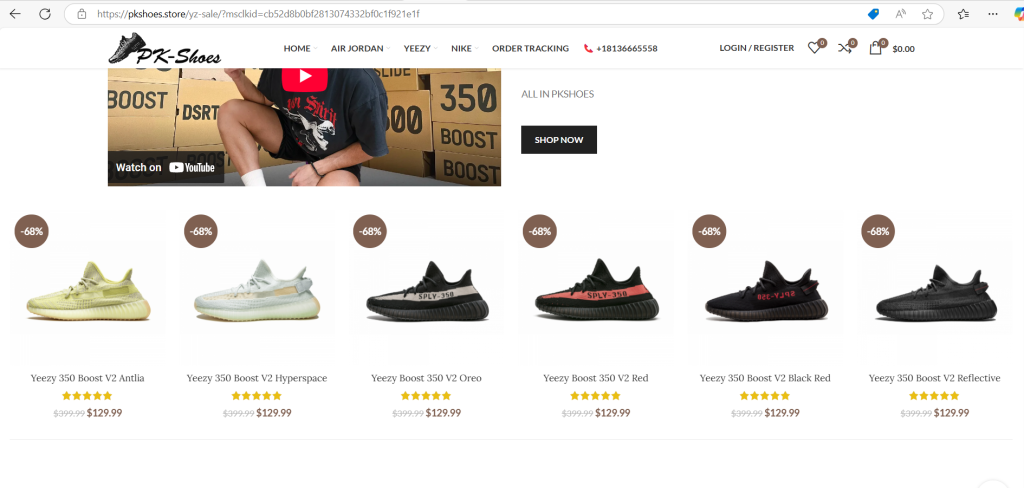
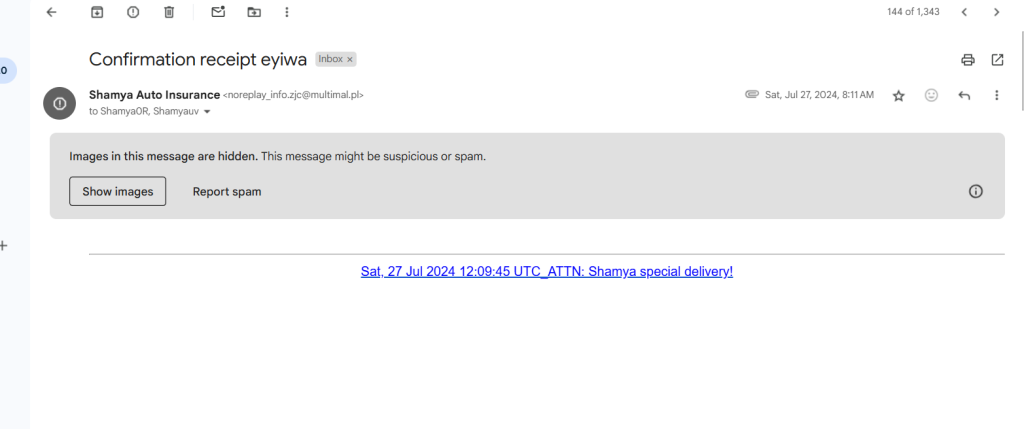
This is a screenshot of one of the spam emails I have received that included a fake link for “auto insurance”, Besides my email account notifying me that it is most likely a scam. I know personally what insurance I have and don’t have. Also, the email name is very random, and I can see that they sent this to other Gmail accounts that have the same fist name as me.
Week 7:
Review the following ten photos through a cybersecurity human systems integration framework. Create a meme explaining what is going on in the individual’s or individuals’ mind(s).
https://unsplash.com/photos/BXiLSwwvqrY
“When you’re scrolling through your feed about recent phishing email incidents and realize your vulnerable because its sounds exactly like the email you responded to earlier that morning”
This meme relates to human systems integration because this is a mistake that can happen if a person does not receive cybersecurity/work training that guarantees that users and employees can operate systems in a safe and effective manner.
Week 8:
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity.
Most movies and tv shows are meant to be dramatic for entertainment but I feel that only a few have some realistic scenes for cybersecurity. For example, the movie “WarGames” showed the scene of a young guy that found a sheet of paper of recent passwords in a draw that were most likely used on multiple accounts that allowed him to have easy access to hack. That clip in the video showed real life problems of security risk. However, most films distort the reality of cybersecurity by making their profession seem way easier than it actually is. Hackers are basically shown as superheroes that can quickly hack complex systems in less than one minute by typing extremely fast on the keyboard. In reality, it takes way more patients in cybersecurity to solve through problems of different systems and achieving task through teamwork. Movies and shows will make you believe cybersecurity task could be done effortlessly by one person. For people to have a true understanding of the amount of time and skills that are needed with this job they would have to gain most of their knowledge from actual cybersecurity professionals.
Week 10:
Complete the Social Media Disorder scaleLinks to an external site.. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
I scored a 4 out of 9 on the social media disorder scale. I think the scale is a great way to acknowledge and confront social media addiction. Also, I think there are different patterns found across the world to expose different levels of social media addiction based on statistics.
Week 11:
Read this and write a journal entry summarizing your response to the article on social cybersecurity
After reading this article on social cybersecurity I think the main point of it was to inform and influence public opinion and create instability within societies without using traditional military actions. This warfare is known as social cybersecurity. Social cybersecurity purpose is to protect society by understanding and fighting online influence campaigns. This article urges coordination among different disciplines, using knowledge from social sciences, data science, and cybersecurity to strengthen the defenses against this kind of attack. Maintaining national security is not a matter of physical borders anymore. We need to be proactive in the virtual space to maintain society as cohesive and trustworthy.
Watch this videoLinks to an external site.. As you watch the videohttps://www.youtube.com/watch?v=iYtmuHbhmS0Links to an external site.
, think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
The job of a cybersecurity analyst relates to social behaviors in a few ways. Cybersecurity analysts have to be systemic thinkers, not only to know about individual threats, but also about how one vulnerability can affect entire networks. The video also explains the need to be team players, collaborating with other departments and professionals. Overall, reflecting the idea that great cybersecurity is a team effort built on trust and unity. In addition, analysts must possess technical and social skills especially when educating non-technical users about phishing or insider threats. Communication is very important because analyst must explain complex threats simply. Also, concepts of civic duty and continuous learning are essential because cybersecurity analyst must keep track of evolving threats and adhere to high ethical standards since they have access to sensitive information.
Week 12:
Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
The Marxian and Classical economic theory relates to this letter. An example from the Marxian theory could be that Glasswasherparts.com used a third-party company, which probably cut operating cost but potentially compromised security. Consumers’ personal information (credit/debit card information) was exposed by this cost-saving tactic by putting profit over protection. An example from the classical theory could be that the business must be encouraged to safeguard information since breaches damage reputation and profits. Therefore, the letter helps maintain confidence from the customers to keep demand from lowering.
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
This article informs us that bug bounty policies are economically beneficial and play a significant role in proactive security solutions. By encouraging ethical hackers to find and reveal vulnerabilities and that organizations can resolve potential security problems before malicious exploitation. Bug bounty policies provide collaborative ideas and a community-oriented approach to cybersecurity by aligning the organizational and security research interests.
Week 13:
Andriy Links to an external site.SlynchukLinks to an external site. Links to an external site.has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
The five most serious violations are faking your identity online, collecting information about children, sharing passwords, addresses, or photos of others. bullying and trolling, and using torrent services. Faking your identity online is serious because pretending to be someone else or giving false personal details is identity fraud. It can also destroy trust in online communication. Collecting information about children is illegal under the Children’s Online Protection Act which demands parental permission before collecting information from children. These violations can result in illegal consequences and endanger the safety of children. Sharing passwords, addresses, or photos of others can be a breach of privacy rights and result in harassment or identity theft. Bullying and trolling can turn into criminal offense charges and jail time because it can affect people negatively mentally and physically. Lastly, using torrent services is unfair and illegal because it is copyrighted material which doesn’t give credit to the creators.
Week 15:
Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
Davin Teo informs the audience how digital forensics combines technology and the understanding of human behavior. His professional life demonstrates that digital forensics investigators utilize social science information, including psychology, sociology, and ethics. Investigators examine the behaviors, motivations, and patterns within the digital data rather than the raw data itself. His work suggests that it is important to equally learn about the human side of cybercrime along with technology. His experience shows that digital forensics is about integrating many disciplines so that technology and social sciences come together to uncover problems of different cyber incidents.