Intrusion Detection Systems
Stephen Rockefeller
Cyber Security
CYSE 250
Old Dominion University
Abstract
The ability to detect unwanted intrusion in real time is critical in protecting a system or network from malicious attacks. Intrusion detection systems are essential to providing users a safety net in which they can protect their business or personal data from being breached or compromised. External and internal intrusions present an ongoing global battle that must be fought daily. Along with the increase in computer use, cloud-based systems, remote working, and network complexities, comes a host of new vulnerabilities, gaps in protection, and more complicated security issues that need to be overcome. Vulnerabilities can easily be exploited by malicious attackers in many forms and within many platforms. Even with the most advanced and proactive intrusion detection systems, vulnerability remains a high priority in cyber security. Improving methods of cyber-security is paramount, and new techniques, such as artificial intelligence, are leading the way in research. As cyber warfare grows around the world and attacks become more complex, so does the need for more intricate forms of intrusion detection to secure personal data, intellectual property, and our national security.
Key Words: Intrusion Detection, Vulnerabilities, Cyber-Attack, Artificial Intelligence
Introduction
Intrusion detection systems are designed to identify malicious activity within a computer system and network traffic. The goal of an intrusion detection system is to identify security breaches that the normal, human user is not able to detect. The major components of an intrusion detection system include securing the network perimeter, securing the network interior, and authentication of users. Implementing an intrusion detection system allows a system or network to quicky identify threats, alert the user, and act against the attack. What appears to be missing from this initial encounter is the ability of the system to take the necessary action to obstruct the attack reliably and successfully. The current intrusion detection systems are designed to recognize unsolicited activity and act to block or remove the intrusion however, the growing complexity of cyber-attacks leaves the current systems less effective and in need of more advanced capabilities. As with any early detection system, the goal is to eliminate the threat and prevent or terminate the attack. Businesses, private individuals, and government agencies are the target of ongoing threats and cyber-attacks. It has become imperative that solutions be found to impede those attackers attempting to infiltrate systems and networks. Whether it is an individual’s personal data, a company’s intellectual data, or a government’s national security, the threat of cyber-attacks continues to grow exponentially, therefore elevating the need for swift, preemptive, and evolving security measures that remain ahead of these threats.
Intrusion Detection Systems
Intrusion Detection Systems are tools implemented to detect the infiltration of unauthorized use of a computer or network. Intrusion detection systems are algorithms designed to detect malicious activity or intrusion within a network (Adnan, Di, and Kaja 2019). These systems work to promote the safety of a network by promoting confidentiality, identification, and security within the system. By detecting unauthorized use or improper use within a system, intrusion detection systems can react by notifying the user of a potential threat. Abraham, Mukkamala, and Sung (2005), describe two specific types of intruders: external intruders and internal intruders. External intruders are unauthorized users of information and systems that they attack. An external intruder gains access from outside in an attempt to steal private data. External intruders will often employ malicious attack schemes such as denial of service and distributing malware as a ploy to steal data. Other scams might include phishing emails that lure a victim into accessing links that will provide the attacker access to the system. Internal intruders are comprised of those who have access to restricted information and systems. Internal intruders can be the result of poor work policies within an organization. Internal intrusion can be as simple as poorly trained employees who create unneeded vulnerabilities or other more dramatic instances such as corporate sabotage from a disgruntled worker.
Abraham, Mukkamala, and Sung (2005), report that intrusion detection has become a critical issue due to the increasing number of worldwide cyber-attacks. What they have discovered is intrusion detection is highly subjective and can result in false-negative warnings as well as false positive warnings. The majority of intrusion detection systems are designed to react to specific behaviors intended to signal malicious activity. The authors state most intrusion detection systems are very expensive due to requiring a large amount of data be stored for audit analysis. It becomes necessary for the system to collect large chunks of data that can be mined and analyzed in order to be able to determine intrusions. The additional storage and CPU space needed for these large chunks of data, creates financial limitations for most individuals and businesses (Abraham et al., 2005).
There are two specific types of intrusion detection systems that make up the systems being used to protect technology. The first is a host-based system referred to as HIDS. A host-based system resides on a network node or on a computer that is connected to a network. A host network system is similar to a virus or malware scanner insomuch that it will scan traffic in search of malicious activity. The second type of system is a network-based detection systems referred to as NIDS. Network based systems are directly connected to a network and act as a sniffer to detect malicious activity. NIDS will monitor all traffic within a network, and once an intrusion is detected, will signal for additional action to be taken (Albin, 2011).
There also exists two different approaches to intrusion detection systems (Alqahtani, Hamed, et al. 2020). An anomaly-based intrusion detection system is based on the detection of anomalies that occur during use. An anomaly can be described as any activity that falls outside of the established data set or communication style pre-configured within a system. An anomaly-based system monitors activity and searches for irregularities in traffic and use. While this type of detection is useful, it has shown to create false positive accounts of intrusion due to the high level of traffic and noise on specific sites and networks. The second type of intrusion detection system is a signature-based scanning search for predetermined and preconfigured attacks based on specific patterns found in different types of malwares. This might include byte sequences in network traffic that appear similar to that of malware or other types of malicious viruses. This type of detection is known as sweeps or probes and can be efficient when the type of attack is pre-configured however, it does not work when the pattern is not known or recognized (Adnan, Di, and Kaja 2019). Graph 1 and 2: Illustrate Hose Based and Network Based IDS Systems
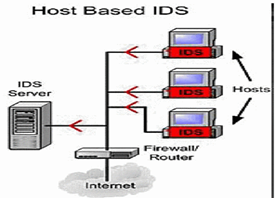
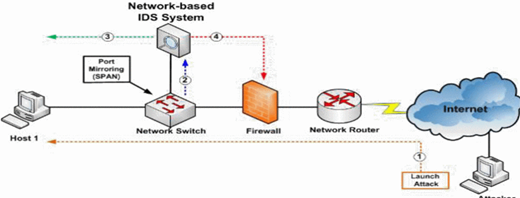
Graph 1 Graph 2
(Gaddam & Nandhini, 2017)
Specific Intrusion Detection Systems Studied:
One of the most well-known intrusion detection systems currently in use is SNORT. Gaddam and Nandhini (2017), describe SNORT as a single thread open-source network intrusion detections system. Snort consists of packet sniffers, preprocessors, detection engine, and a log and alarm system. Initially a packet is sniffed and if it coincides with specific pre-configured rules, it is then processed. The advantage of this intrusion detection system is the ease in which it can be deployed as well as its capabilities over various topographies. Gaddam and Nandhini (2017), describe SNORT as an efficient intrusion detection system against simple attacks however, they note that further development of more complex defense systems is needed to guard against more complex attacks. The graph below is an illustration of the SNORT process.
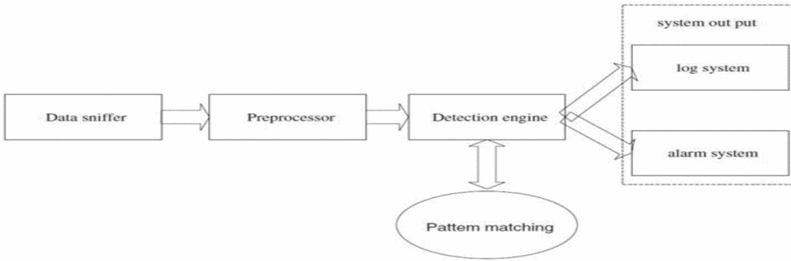
(Gaddam & Nandhini, 2017)
Suricata is a newer intrusion detection system that provides open-sourced intrusion detection and prevention. Unlike SNORT, Suricata is a multi-thread system and therefore is capable of monitoring multiple CPU/cores as necessary (Albin, 2011). The author studied the effectiveness of both Snort and Suricata and found that its ability to deploy native multi-thread operations makes this system more reliable with increase in network bandwidths. The author noted, in his study, Suricata has another advantage in its use of a hyper-text transfer protocol that allows it to monitor traffic for attack strategies.
The following illustration shows Suricata process:
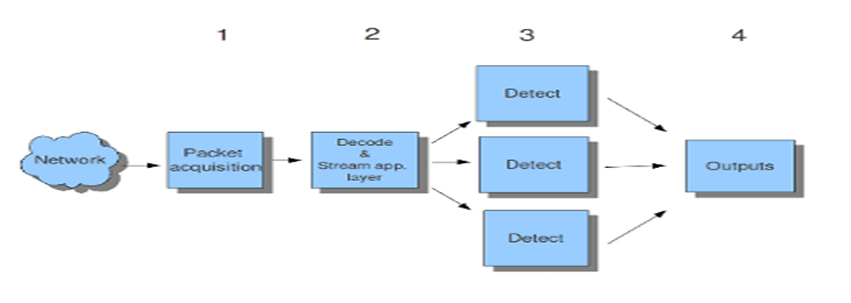
(Suricata)
OSSEC, another well-known intrusion detection system, is an open-source host-based intrusion detection system that performs log analysis and integrity checks. OSSEC is a host-based intrusion detection system capable of monitoring one system or thousands of systems. OSSEC utilizes both anomaly and signature-based detection.
The illustration below demonstrates the OSSEC process:
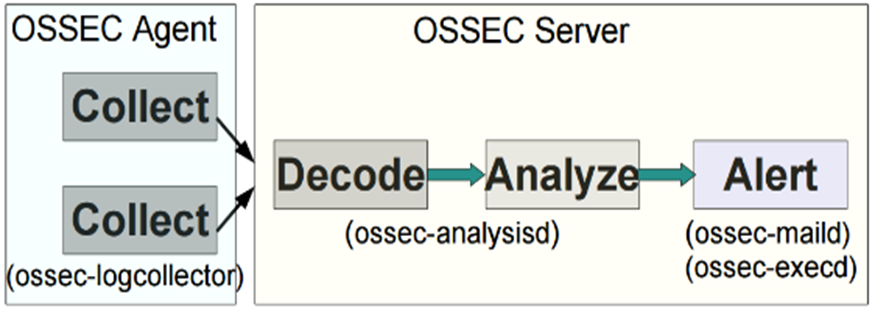
(Malik, 2016)
Research surrounding the efficacy and reliability of specific intrusion detection systems is ongoing. Albin (2011) conducted research on both Snort and Suricata to determine which system provides the most accurate and reliable intrusion detection. The researcher found that in one experiment between the two systems, Suricata provided a higher rate of reports than Snort when compared to the same traffic. He concluded that due to several error messages, further study would need to be conducted to be conclusive in his findings. Overall, this research noted that both Snort and Suricata provide capable intrusion detection, yet both have benefits and flaws. This study found that Suricata requires a much higher memory and RAM than Snort yet offers multi-thread capabilities useful for multiple CPU monitoring. Albin (2011), noted that Snort remains a leading system however, with the continued growth of bandwidth, systems such as Suricata that provide multi-thread capabilities will become more necessary.
The comparison of Snort versus OSSEC involves comparing a network-based system against a host-based system. Singh and Singh (18) studied OSSEC and Snort to determine the advantages and disadvantages of both systems. What the researchers found very appealing of OSSEC is the immediate email notification this system provides once an intrusion is detected. They determined the best approach to deciding on what type of intrusion detection system starts with determining your exact needs. Whether a company or individual, needs must be factored into the process of choosing the best intrusion detection system.
Research and New Methodologies
At forefront of discussion surrounding intrusion detection systems, is the need for efficient, affordable, and reliable approaches. Anomaly based and signature-based systems share equally beneficial aspects however, neither presents itself to be full proof. Bhattacharyya et al, (2013), provide research involving a hybrid method designed to develop a more efficient and effective system to detect known and unknown attacks with a high level of proficiency. Their research centers around multi-level hybrid intrusion detection systems. They studied three levels of attack detection that included supervised method, unsupervised method, and outlier-based method. They concluded that a multi-level hybrid intrusion detection method based on a supervised, unsupervised, and outlier methods produced very good performances. The detection rates were high when tested in real life intrusion data sets (Bhattacharyya et al., 2013). They concluded the need for continued research into the most effective methods for detecting malicious attacks and intrusions is primary. As we have seen in this study, the need for more advanced methods in detecting intrusion is imperative in order to stay ahead of attackers vying for personal and secure data.
Hartmann and Kabir (2018) researched an experimental method incorporating SNORT, a network intrusion detection system, but arranging the grouping differently in hopes of creating a more efficient and successful system. SNORT is a network intrusion detection system that has rules-based logging that performs content pattern matching to detect various types of attacks and probes. Snort provides user friendly, light weight capabilities that other, more commercial intrusion detection systems can’t provide (Roesch, 1999).
Abdullah et al, (2020), studied the use of artificial intelligence in the form of machine learning and deep learning capabilities. Their research analyzed the sub-category of artificial intelligence known as machine learning. In terms of intrusion detection, machine learning can be described as a subset of artificial intelligence that learns from the data it is given and continues to improve and expand its knowledge. A familiar everyday example of machine learning is a music streaming system. This system takes the data given, what music the listener likes, then expands the menu to include additional, similar music based on the original data set. Abdullah et al, (2020) stated, machine learning is a highly effective tool to detecting intruders on networks. They also studied the efficiency and effectiveness of deep learning technology. Deep learning technology is a subset of artificial intelligence and machine learning. Deep learning goes a few steps further than machine learning by creating an artificial neural network that can learn from the data set it is given and go on to make its own decisions. What these researchers discovered is deep learning technology is highly popular however, its complexity and high use of resources create an obstacle for users that will still need to be reconciled. The researchers determined further research is needed to implement a hybrid model using both machine learning and deep learning but utilizing a less complex algorithm in order to make it more accessible.
Conclusion:
Research continues in the development of effective intrusion detection systems. Society’s demand for technology appears to be outpacing the methods needed to protect users from malicious and unwanted intruders. With the development of technology such as cloud-based storage, new security issues continue to arise. Cloud based storage has created gaps in security that will need to be addressed sooner than later. Currently there are several highly effective intrusion detection systems on the market including the three that are discussed in this paper; Snort, Suricata, and OSSEC. Although these systems produce effective defenses against intrusion, they are not as reliable against the ongoing surge in cyber-attacks and the increasing complexity of hackers and their methods. What is needed in the world of cyber-security are efficient and effective systems that can evolve along with the evolution of cyber-attackers. The technology industry must be able to develop systems that can incorporate artificial intelligence, whether in the form of machine learning and deep learning or a hybrid combination of these technologies, which can outpace the rapidly growing assault on personal, business, and national security data. In recent months we have seen the ransom-attack on the Colonial Pipeline. The attackers held data for ransom and demanded 4.4 million dollars in bitcoin. Although a lot of this money was recovered, this is only one example of cyber-warfare that is taking place globally. The global threat of cyber-attacks continues to increase. These threats will not go away and will continue to become more potent as the complexity of cyber-attacks continue to emerge. Researchers and cyber-security experts must continue to study and develop new methods to usurp the threats of cyber-attackers. The use and expansion of artificial intelligence is one key that may be able to help secure our data against these attacks however, further research and development of intrusion detection systems is critical in our search for data security.
References
Abdullah, J., Ahmad, F., Ahmad, Z., Shahid Khan, A., & Wai Shiang, C. (2020). Network intrusion detection system: A systematic study of machine learning and Deep Learning Approaches. Transactions on Emerging Telecommunications Technologies, 32(1).
Abraham, A., Mukkamala, S., & Sung, A. (2005). Cyber-security challenges. Enhancing Computer Security with Smart Technology, 125–164.
Albin, E. (2011). A Comparative Analysis of the Snort and Suricata Intrusion-detection Systems (49th ed.). Naval Postgraduate School.
Alqahtani, Hamed, et al. “Cyber intrusion detection using machine learning classification techniques.” International Conference on Computing Science, Communication and Security. Springer, Singapore, 2020.
Adnan, Shaout, Di, Ma, and Kaja, Nevrus. “An Intelligent Detection System.” Applied Intelligence 49.9 (2019): 3235-3247.
Bhattacharyya, D. K., Borah, B., Gogoi, P., & Kalita, J. K. (2013). MLH-ids: A multi-level hybrid intrusion detection method. The Computer Journal, 57(4), 602–623.
Gaddam, R. T., & Nandhini, M. (2017). An analysis of various snort-based techniques to detect and prevent intrusions in networks proposal with code refactoring Snort Tool in Kali Linux Environment. 2017 International Conference on Inventive Communication and Computational Technologies (ICICCT).
Hartmann, S., & Kabir, M. F. (2018). Cyber security challenges: An efficient intrusion detection system design. 2018 International Young Engineers Forum (YEF-ECE). https://doi.org/10.1109/yef-ece.2018.8368933
Malik, P. (2016, December 27). Retrieved February 17, 2022, from https://www.tothenew.com/blog/benefits-of-using-a-host-based-intrusion-detection-system/.
Roesch, M. (1999). SNORT- Lightweight Intrusion Detection for Networks. The Usinex Association.
Suricata.yaml. 10.1. Suricata.yaml – Suricata 6.0.0 documentation. (n.d.). Retrieved February 17, 2022, from https://suricata.readthedocs.io/en/suricata-6.0.0/configuration/suricata-yaml.html