Journal Entry #1 (pg 28) –
Review the NICE Workforce Framework. Are there certain areas that you
would want to focus your career on? Explain which areas would appeal
the most to you and which would appeal the least.
Workforce Framework for Cybersecurity (NICE Framework) | NICCS (cisa.gov)
If I utilized the NICE Workforce framework into my career, the areas I would find most appealing to me would be analyze and investigate. There are many areas in your cybersecurity company that you can analyze. Data reports can be analyzed so that you can adjust to improve trends of the company economically. Investigating is a must because employees have to be able to understand what the threat is that is harming the company and how they can stop it. Investigations can also be a lesson for how the company can improve their security infrastructures. Both of these areas are obvious, but crucial parts of being in the field of cybersecurity.
The areas that would appeal the least to me would be Oversee and Govern because although every employee in the company has their equal part in the company’s success, the CTO is the one responsible for leading the way. They are the leader and frontman of the plans in development and if I am not the CTO, I don’t have the authority to apply my envisions to the company. This renders the area less relevant to me than the others.
Journal Entry #2 – Explain how the principles of science relate to cybersecurity.
With cybersecurity being a subset of computer science, the science of coding is vital to the construction of hardware infrastructures within companies. Coding serves as the fundamental web that protects assets through the minds of cybersecurity specialists. Not only does coding provide an essential foundation of science for cybersecurity, but scientific research also plays a role as well. Cybersecurity companies often times rely on trusted scientific findings and research to implement the right changes within their infrastructure. This way, through validated data, they know that want they are implementing can lead to significant improvements against malicious threats that harm their infrastructure.
Journal Entry #3 – Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches? Enter a paragraph in your journal.
With the evidence that data breaches are a common threat to companies and are a pandemic in the cybersecurity sphere, researchers can study how companies can develop better strategies to defend against these threats. Researchers can view the list of organizations with the largest number of reported breach notifications on the website with banks being the most targeted. They can focus on these targets as being the ones who need to improve the most and then look on their weakpoints that hackers are exploiting. They can also view the type of data breaches on the website with HACK being first and UNKN being second. Knowing that California, Texas, and New York have been the most targeted as of 2023 (Mapbox), researchers can direct their focus to these states and possibly their banks since they would be tackling two big issues within the data breach pandemic.
Journal Entry #4- Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
The physiological needs section relates to how I learned the fundamentals of using technology when I first experienced it. I learned very important functions of devices that allowed me to be able to properly use them, especially a computer which is an important device for my work today. This relates to how essentials such as air, water, food, and shelter are important to life. The safety needs of learning personal security, employment, and health can relate to how I learned how to protect myself on the internet. The internet is a hostile place and learning how to secure your personal information is very important. With the love and belonging section, even though I adore the use of technology and its convenience, I still make sure to leave room in the day for time with my family and friends. I always make sure to respect others and remember my sense of freedom online even when I am not directly face to face with someone. Lastly, the self-actualization section is vital because I want to strive to be the best that I can be. Self-actualization involves achieving who you want to be and I want to be able to reach my long-term goal of being in the field of Cybersecurity.
Journal Entry #5 – Review the articles linked with each individual motive in the presentation page or Slide #3. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
#1- I believe “political” is the one that makes the most sense as a lot of data breaches these days have conspiracies that these groups are tied to a political party. The groups that commit the act may be doing it for a political agenda, whether that is to defame a figure or to manipulate the election race.
#2- “For money” is another great one because ransomware is becoming a more common form of cyberattack. A lot of economic and financial losses by conglomerates and individuals alike are a result of ransomware. The fact that a lot of times it causes immense pressure on the victim and near guarantees a reward for the hacker is why it makes the most sense. Also, hacker groups tend to have contracts where they are assigned to hack someone with money in return.
#3- “Multiple reasons” can include many things. However, if we are including it in the context of what the most common reasons are for hacking, it makes a lot of sense.
#4- “Boredom” is another senseful reason but also less common. This is because it is a reasoning seen more upon casual hackers or individual hackers. Hackers will often times hack at their own leisure, either to demonstrate their power or intimidate.
#5- “Entertainment” is a reason with lesser sense because but it can also be paired with boredom. Hackers can hack because they are bored and want entertainment. Because of this, both of these reasons can be intertwined.
#6- “Revenge” doesn’t make a lot of sense because it is very situational. It could be a dispute between two individuals or countries. It would have to result in huge extremities in order to reach these circumstances.
#7- “Recognition” believe it or not doesn’t make sense. Although you can consider hacker groups hacking big conglomerates such as Google or Apple to be a form of them wanting recognition, it doesn’t make much sense because hackers a lot of times prefer to be unknown. The whole point of a hacker concealing their identity is because they don’t want to be caught.
Journal Entry #6 –
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?
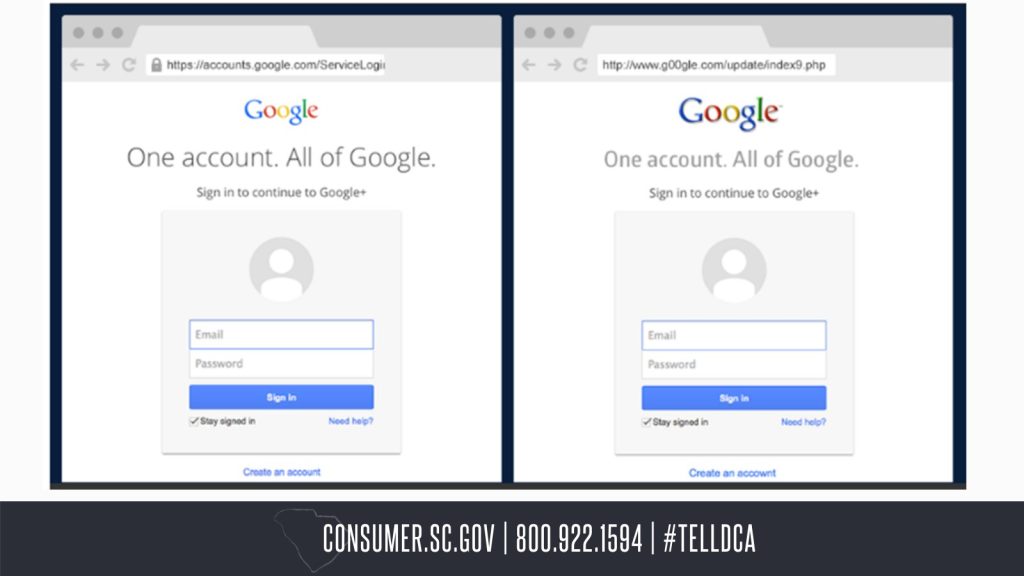
This example here is a fake website because it raises to major red flags: a fake URL and abnormal logo. The URL spells out google with numbers which is strange because it never contains that in other Google navigations. The other red flag is that the Google logo looks different than normal. It looks as if it is an older version of it.
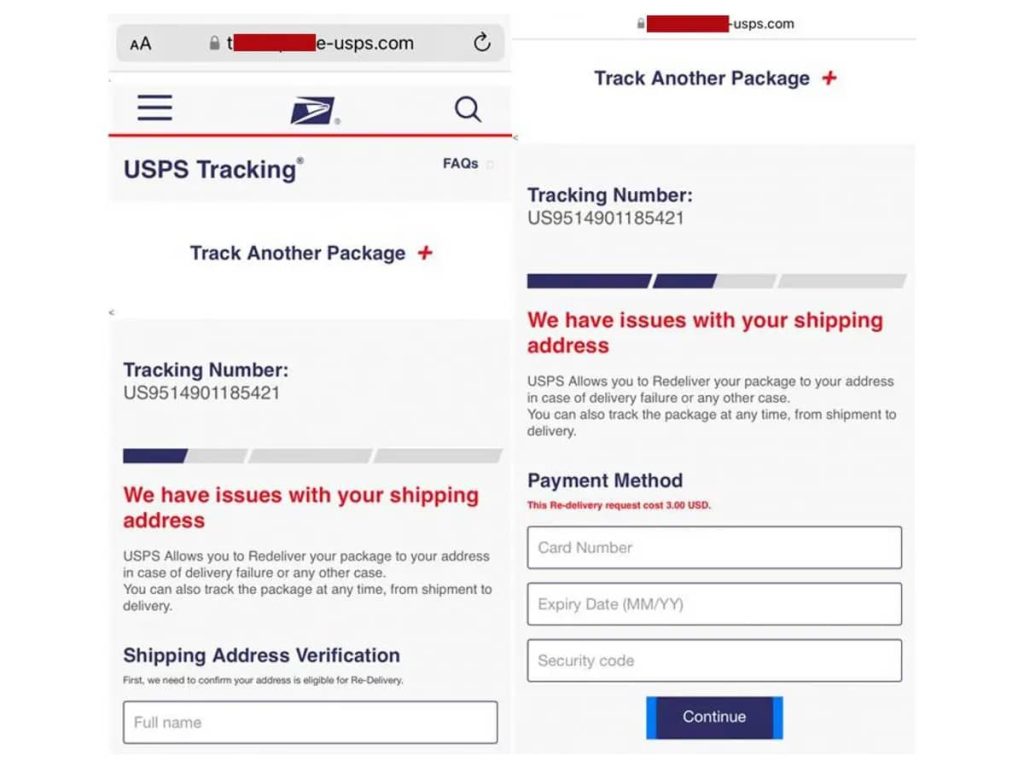
This second one here compares to images, where the left one is the real one and the right is the fake. The reason is because the right one is asking for a payment method for an issue as simple as adjusting your address. Companies will never ask for your payment information nor any form of payment when all that is needed is to fix the address on your order. Once they get your payment information, it is bad news for you and good for the hacker.
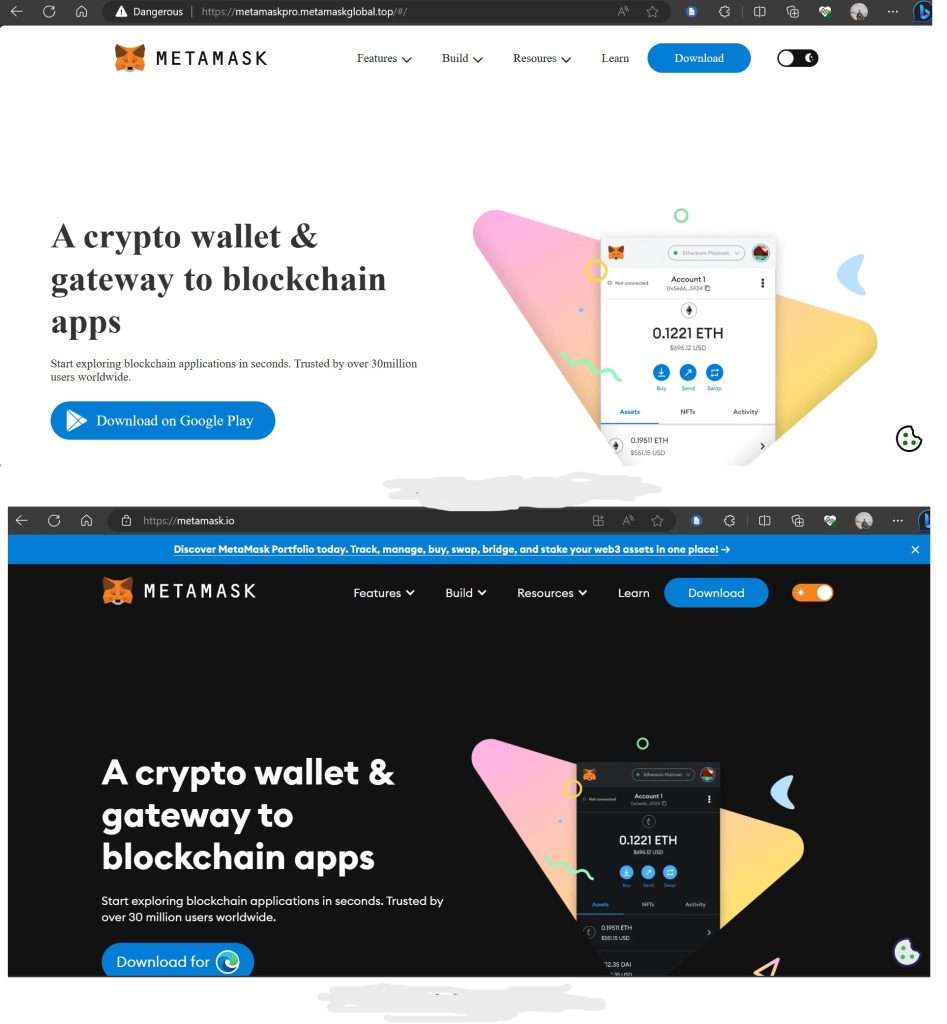
In this final one, fake websites don’t always deviate from suspicious URLS. They can also showcase through visuals on the website. What might seem different than normal on the website could potentially be a red flag. As noted in this example, the red flags of the fake one on top is that the font is different, almost generic, and that it doesn’t have the black background. If the website looks almost too plain and you think something is offputting, chances are you are right.
Journal Entry #7 –
Journal Entry #8 –
Read this and write a journal entry summarizing your response to the article on social cybersecurity
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity
Cybersecurity is influenced by the media in exaggerated ways as demonstrated in the movie scenes shown. Often times it will depict unrealistic settings or methods that are absurd compared to the real world of cybersecurity and what a hacker would actually do in the given situation. The cybersecurity depictions in movies are often times what you don’t want to do in real life because they are invalid methods of being a hacker. Because of this, it doesn’t teach outsiders to cybersecurity the actual experience of it because it is unrealistic on how the movie depicts it. This is why movie directors should bring experienced hackers or professionals in the cybersecurity field so their movie can have realistic elements and that the person can detail how they perform their methods.
Journal Entry #9 –
Watch this Video: Social media and cybersecurityLinks to an external site.
Social media and cybersecurityLinks to an external site.
I completed the Social Media Disorder Scale and only scored 1 out of the 9 questions. The reason I only scored one is because I’m not particularly a social media person and I don’t go on them much. They aren’t something I rely on as a form of hobby or communication with others. I do believe that these are accurate questions to be asked to people who have developed a consumed hobby with social media to the point it has developed a negative influence on their life. Everyone is going to vary on their scores because people are exposed to varying amounts of technology around the world. Some people have access to lots of technology while others are exposed to next to none. The ones who are exposed to it more are more likely to develop social media disorder than the ones who aren’t
Journal Entry #10 –
Read this and write a journal entry summarizing your response to the article on social cybersecurity
This article raises awareness on the dangers and uprise of social cybersecurity, which differs from the traditional cybersecurity because it specifically targets people. It’s an epidemic of attacks that we must all stay aware of through our tactics such as protecting our personal information and watching what we are navigating. The article is a perfect example of the many dangers that technology brings. The further it advances, the more opportunities it gives hackers to exploit people. We must all remain vigilant on not just the dangers of social cybersecurity, but malicious activity in general.
Journal Entry #11 –
Watch this video: Social media and cybersecurityLinks to an external site. As you watch the video https://www.youtube.com/watch?v=iYtmuHbhmS0Links to an external site., think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
The duties of cybersecurity analyst not only involves independent tasks, but tasks where you will need to coordinate with others in your group in a sense that promotes social behavior. These tasks may involve responding to incidents, finding flaws in infrastructure, and having discussions in how they can improve the infrastructure. As the person in the video states, it’s a pretty versatile job and you can work basically anywhere which promotes the idea of how cybersecurity can be just as social as many other fields of work.
Journal Entry #12 –
Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
Asymmetric Information Theory- This economic theory relates to the letter because it details about how one party has more knowledge about the situation than the other. In this case, the company is informing the customer of the identity theft incident, which means that the company knew about this prior to relaying the information to them.
New Growth Theory- The economic theory “New Growth Theory” prioritizes the consumers and their issues. The company prioritized helping the victims of identity theft and telling them what they need to do immediately.
Interactionist Perspective Theory- This social science theory can be seen as how consumers expect companies to play their role when they are in need, which involves them interacting with the consumer to resolve it. This aids in the idea of how this theory is a social science.
Functionalist Perspective Theory- This social science theory is all about helping each other and being influenced by each other, in this case the people of the company have to cooperate with each other to resolve the main issue at hand.
References:
11 Types of Economic Theory | Analytics Steps
5 Nobel Prize-Winning Economic Theories You Should Know About (investopedia.com)
Popular Theories of Sociology | National University (nu.edu)
Journal Entry #13-
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
The policy of bug bounties can be an effective way to find detrimental bugs and improve security infrastructure. The idea of monetary benefits can encourage people to achieve this goal. However, the article states that their programs have received few valid reports and as programs age, bugs will become harder to find. This means unless companies find a more effective way to use bug bounties, they will meet challenges against improving infrastructure.
Journal Entry #14-
Andriy Slynchuk has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
All of the offenses are serious and are things you should never risk doing, but the five most serious ones I see are: using torrent services, bullying and trolling, collecting information about children, faking your identity online, and illegal searches on the internet.
- Using torrent services: Doing this is illegal and if caught, you could be facing charges of copyright and possibly sent to jail.
- Bullying and trolling: While this might seem mild to some people, it can lead to serious consequences and can affect the victim mentally.
- Collecting Information about Children: This can involve the FBI and the person could be targeted for doing this
- Faking your Identity Online: This one can be interpreted as good and bad. Some people may be self-conscious about themselves and may want to take on a different identity. This for the most part is fine, but there are also people who do this with a purpose of identity theft. Identity theft will always be a very serious cybercrime and will result in serious consequences.
Journal Entry #15-
Digital forensics operates the same way as normal forensic science in which everyone must work together to uncover evidence towards the investigation, but through digital means. This is how social science is incorporated into digital forensics because everyone in the group is utilizing technology and analysis through devices to uncover crime. His pathway is unique because he ventured out to something that is completely different. He still felt confident in his abilities to perform this different career, which then blossomed into a successful he is living now.