I found an article on the company Set Forth and their data breach that compromised 1.5 million people. The company had discovered that they were compromised on May 21, 2024, and stated that the potentially leaked information includes names, addresses, dates of birth, and Social Security Numbers (SSNs). Additional customers may have also been affected due to the relationship connection with Centrex Software, which provides cloud-based customer relationship management solutions to get data from their customers. In November, a statement was sent out to the potentially affected customers that included 12 months of free Cyberscout services to reduce their potential for identity theft. This statement also mentions that the company is making changes to their endpoint security and changing passwords, so it is likely that the method for the breach could be through phishing, credential harvesting, social engineering, or another method of gaining initial credentials for a malicious actor to get inside the system for an extended period. This, like all breaches, should be a lesson for companies to keep cybersecurity as part of their business model, and to always remain on top when it comes to their data, not only to protect their customers but to keep themselves aware and safe.
IT 315 – Hands-On Exercise 9 Discussion
Discuss your approach to completing this Hands-on Assignment. (1) Give the URL of the resource(s) you used to find instructions for installing and using Wireshark. What advice would you give to another new user to make the process successful? (2) Briefly explain how to interpret the information in the packet details section for the server’s response to your computer’s GET command. How does understanding encapsulation help you find and interpret the contents of a frame? (3) Briefly explain the information shown in the packet capture (top) section, and how to interpret it. How does using filters help network analysts to locate the specific packets they need?
(1) Give the URL of the resource(s) you used to find instructions for installing and using Wireshark. What advice would you give to another new user to make the process successful?
There were two primary URLs used for installing and using Wireshark. The URL for downloading Wireshark and offering instructions was https://www.wireshark.org/download.html. The other URL to offer further instructions for using Wireshark for the assignment was https://www.wireshark.org/docs/wsug_html_chunked/. The advice that I would offer to newer users is to utilize Google searches and YouTube videos to better understand the process for installing and using Wireshark.
(2) Briefly explain how to interpret the information in the packet details section for the server’s response to your computer’s GET command. How does understanding encapsulation help you find and interpret the contents of a frame?
To interpret the information for the server’s response to the GET command, it starts with looking in the HTTP sections of the packet to find the necessary information and then noting how each segment of the command is broken down with the requested URI, path, query, and version of HTTP to combine to create the full command. Encapsulation helps understand the contents of a frame by understanding how its smaller components are ordered in a specific format from the inner to the outermost layer.
(3) Briefly explain the information shown in the packet capture (top) section, and how to interpret it. How does using filters help network analysts to locate the specific packets they need?
The information in the packet capture section has a large amount of interpretation, consisting of a number associated with each packet in the capture, the time it was captured, the source and destination IP addresses for a basic path, the protocols connected to most packets, the total bit length of a packet, and additional information that provides simplified information that can be found in a packet’s details. Filters can help to save a lot of time for network analysts due to thousands of packets showing in a few minutes, and if they are looking for a specific component or type of packet, they won’t need to look through the details through every packet in a capture.
IT 315 – Hands-On Exercise 8 Discussion
Discuss your approach to completing this Hands-on Assignment. (1) What IP address did you choose for Router A’s LAN port? (2) What IP address did you choose for Router B’s WAN port? (3) Is Router A’s LAN port on the same subnet as Router B’s WAN port? What about the network topology suggests that it should or should not be? (4) In addition to the rows that are created automatically, is another routing table entry needed on Router A to enable it to forward packets to the LAN subnet on Router B? (5) Is a routing table entry needed on Router B to enable it to forward packets to the LAN subnet on Router A?
(1) What IP address did you choose for Router A’s LAN port?
The IP address I chose for Router A’s LAN port was 10.0.1.1/24 to connect the first 50 workstations.
(2) What IP address did you choose for Router B’s WAN port?
The IP address I chose for Router B’s WAN port was 10.0.3.2/30 for both routers to connect on a 10.0.3.x subnet based on my diagram.
(3) Is Router A’s LAN port on the same subnet as Router B’s WAN port? What about the network topology suggests that it should or should not be?
No, Router A’s LAN port and Router B’s WAN port would not be on the same subnet. While the switch connects the two routers, the purpose behind the two routers is different. Router A is not only meant to connect 50 workstations but also connect to the internet and Router B, while Router B is only meant to connect the other 50 workstations to Router A. Having them be on the different subnets is needed for communication to flow efficiently.
(4) In addition to the rows that are created automatically, is another routing table entry needed on Router A to enable it to forward packets to the LAN subnet on Router B?
Yes, a routing table entry is needed on router A to forward packets to the LAN subnet on Router B (10.0.2.0/24) via a static route. This would be via the IP address 10.0.3.2, which would connect to Router B via the WAN port into the LAN subnet.
(5) Is a routing table entry needed on Router B to enable it to forward packets to the LAN subnet on Router A?
Yes, an additional routing table entry is needed for Router B to forward packets to the LAN subnet on Router A (10.0.1.0/24) via another static route. This would be via the IP address 10.0.3.1, which would connect to Router A via the WAN port into the LAN subnet.
IT 315 – Hands-On Exercise 7 Discussion
Discuss your approach to completing this Hands-on Assignment. (1) Were there any pitfalls that you encountered that might help others? (2) How did you use the tracert results to make a subnet diagram that showed the subnets between the three networks?
(1) Were there any pitfalls that you encountered that might help others?
The main pitfall I encountered was connecting rhnet.is back to my computer. Despite multiple attempts to have the traceroute fully connect, it would not happen. So, I had to make the connection from rhnet.is to erik.co.uk instead to get the data for the final network, which fortunately worked immediately. I would recommend this not only for saving time but also to provide a reversed order of the second connection from Net B to Net C. Another small pitfall was having to deal with asterisks and periods from my other connections. While they can be annoying, they are not a significant problem, and ironically enough, the recommendation I would make is to have some patience for the remainder of the output to print.
(2) How did you use the tracert results to make a subnet diagram that showed the subnets between the three networks?
My method for using the traceroute results for the subnet diagram was to focus on the IP addresses. I went through each line of all three networks and then used the first two octets of each IP address to be representative of routers that move packets across the network. Due to the beginnings and ends of the networks overlapping with the same first two octets of IP addresses each time, this allowed for simple lines to connect each end.
IT 315 – Hands-On Exercise 6 Discussion
Discuss your approach to completing this Hands-on Assignment. (1) In general terms, what is the investment that was made? (2) In general terms, what is the return that the organization will receive from that investment? (3) How do different assumptions about network usage affect ROI? Do they affect the cost of the investment or the amount of the return?
(1) In general terms, what is the investment that was made?
Generally, the investment that is being made is an upgrade from 10Base-T to a 1000Base-T standard by implementing a new layout for Constant Hall’s network. This takes the form of new dedicated rooms, an extended star topology for switches, category 6A cabling, and new materials to adjust to the scale needed for the upgrade. However, the cost for this implementation is estimated to be around $19,571.10.
(2) In general terms, what is the return that the organization will receive from that investment?
The return from this investment will include significantly faster network performance, reduction in latency, and the potential for more numerical growth regarding more staff and students with the capability for more amounts of traffic to take place at any one period. The upgrade will also grant access to more powerful applications as well as reduce the amount of maintenance fixes that would need to occur compared to the legacy standard.
(3) How do different assumptions about network usage affect ROI? Do they affect the cost of the investment or the amount of the return?Multiple assumptions about network usage can affect the ROI, such as the number of users, the maximum and minimum range of traffic, and the kinds of applications that are used and their required usage cost. The amount of return can be significantly affected but is dependent on comparing the original network to the new one and making a proper judgement on whether the upgrade is worthwhile. If the current legacy network is not able to meet the demands of students and staff, then the ROI from an upgraded network will be beneficial by being able to provide faster speeds and reduce the maintenance required for having a legacy network in the current day. However, if the legacy network can handle the current amount of traffic fine and the cost for current maintenance is proportional, then there would not be a need to upgrade for a small amount of ROI. Regarding the cost of investment, it is less affected compared to the saved costs from the upgrade due to the initial costs being fixed but proportional to the required materials. The initial costs should still be considered with ROI, but the estimated numbers for the people who can utilize the new network are the more prominent factor.
IT 315 – Hands-On Exercise 5 Discussion
Discuss your answers to the questions about Hands on #5( with questions in separate paragraphs): (1) Why do companies pay thousands of dollars for the rights to use a domain name? (2) Why do you think a company would want more than one IP address assigned to a single name? (3) One or more of the names on your list correspond to the same IP address, but when you type those names into your web browser, you see different pages. Why would more than one name be assigned to a single address?
(1) Why do companies pay thousands of dollars for the rights to use a domain name?
Companies have multiple reasons for choosing an expensive domain name. For one, the domain name allows for easy connectivity to a company’s brand. Next, it makes marketing cheaper due to it being a short and more memorable name that can bring in more users. Finally, by being an expensive name, its exclusivity further increases traffic by separating a company’s likelihood of being searched compared to other ones that have a similar product.
(2) Why do you think a company would want more than one IP address assigned to a single name?
Companies choosing to have multiple IP addresses to a single domain name primarily help with the back-end and scale of the business. The immediate reason for multiple IP addresses is redundancy; if there’s traffic across multiple servers and if one goes down, operations can continue. If a company is spread across long distances, then it can also help to have multiple IP addresses to have operations run smoothly regardless. A final reason would be load balancing to prevent any of the individual servers of a company from being overloaded if large amounts of traffic is common.
(3) One or more of the names on your list correspond to the same IP address, but when you type those names into your web browser, you see different pages. Why would more than one name be assigned to a single address.
Having multiple names tied to the same IP address is the result of virtual hosting. This process allows multiple names or websites to be on one server with a single address to reduce the amount of required physical resources compared to dedicated servers. It provides a cost-effective approach to companies that have multiple websites or reduces the costs for smaller business.
IT 315 – Hands-On Exercise 4 Discussion
Discuss your approach to designing the network for Hands on #4. In separate paragraphs with questions listed provide answers to:
- (1) How does the topology of the network cabling influence how the rooms will be interconnected?
- (2) What is the topology of your network?
- (3) Of the switches in your budget, which switches are “core” and which are “workgroup”?
Approach: My approach for Hands-On Exercise #4 has two general aspects. The first is to focus on all the necessary materials for finishing the cabling throughout Constant Hall. I’m focusing on having there be just enough or a little bit extra with the materials for a fitting price. The second aspect is to make sure that the switches have the appropriate specifications to handle the traffic for the network. This is to ensure that there are both proper connection and data flow.
(1) How does the topology of the network cabling influence how the rooms will be interconnected?
The most significant aspects of how topologies influence the interconnectedness of rooms is data flow and the layout of the devices. Because there is a range in how little or how much data is moving at one point, a topology needs to be both simple enough to where there is not excessive space for traffic, but also complex enough to manage all different forms of traffic without significant issue. The more complex the physical layout of a location, the more complex the topology needs to be to account for it. Furthermore, depending on the number of devices like routers, servers, computers, and outlets, they are large factors in how many switches and necessary cabling are needed to connect everything.
(2) What is the topology of your network?
The topology I’ll be using for my network is an extended star topology. This is due to the requirement of having both a “core” and “workgroup” switches that need to connect across the entire building. It also helps to retain connectivity by having the switches connect both with the “core” switch and each other, so if a “workgroup” switch fails, the network can still function.
(3) Of the switches in your budget, which switches are “core” and which are “workgroup”?
The “core” switch for my network is the S3900-48T6S-R switch with 6 SFP ports and the “workgroup” switches will be the S2805S-48T4S switch. With these switches, I will have flexibility when it comes to the interconnectedness of my network. However, while these are the initial choices, I may end up changing them if another option appears or if I need a better “core” or “workgroup” switch for my diagram.
IT 315 – Hands-On Exercise 3 Discussion
Discuss your approach to designing the network for Hands on #3. (1) How does the topology of this network compare with the topology of the network you designed for Hands on #1? (2) What is the difference between an equipment room and a telecomm closet? (3) How does meeting the Cat6a specification affect which rooms you choose for the equipment room and the telecomm closets?
Approach: My approach for designing my network for Hands-On #3 focuses on equally spacing my telecom closets around my equipment room to allow for the necessary cabling to cover the building. I have my equipment room in the center on one side between the central presentation rooms and have telecom closets spaced equally in numberless and windowless rooms for the needed requirements.
- Other than being more complex and larger in its design, Hands-On Exercises #3 and #1 for me utilized the extended star topology. For my Exercise #1, I had the routers connect and then to the computers, printer, and server. With Exercise #3, it requires having the equipment rooms, to then connect to telecom closets, and then spreading out the cabling across the building utilizing routers, outlets, and patch panels.
- The most significant difference between an equipment room and a telecom closet is their scale. Equipment rooms are larger and are meant to house a majority of the technology used for a building or location. Telecommunication closets are much smaller, taking up a single small room, and are meant to be a connecting bridge between an equipment room and connecting all technology throughout a building. They are also meant to work and connect singular floors as opposed to the entire building.
- Meeting the Cat 6a specifications may not have a significant effect on the equipment room and telecom closets due to the cable limit being 90 meters or 295 feet. While the cabling will have to be angled within the building, it clears the width of Constant Hall which is 215 feet. This allows for the flexibility between the equipment room and the telecom closets to be spaced far apart evenly. There are also the factors of having the optimal rooms, but still, there shouldn’t be a significant issue with the layout from the cabling specifications.
IT 315 – Hands-On Exercise 2 Discussion
Post your answers to the questions (question followed by your answer in separate paragraphs).
- Why is stranded rather than solid cable used for patch cables?
Stranded cable is used more than solid cable for patch cables for multiple reasons. Stranded cable is more flexible and durable than solid cable with bending, making it easier for use in places that require it frequently. They can take more damage and have a longer life span as well.
- Why is it critical not to score the jacket too deeply when stripping the cable?
It’s important not to score a jacket too deeply to prevent the internal wires from being cut as well, damaging the cable. Slightly cut wires lead to more noise when patch cables are used, which causes connection issues.
- Why is it recommended to expose more than .5 inches of the wire pairs?
Exposing more than 0.5 inches of the wire pairs allows for proper measurements when cutting excess wire and sliding a connector onto the straightened wire pairs for a patch cable.
- Why is it critical to use the proper pin colors in order?
The standard pin color order is used to ensure that there isn’t crosstalk and worse data transmission between wires. Furthermore, having the pin colors in the correct order allows the cable to function and effectively connect to the network.
- Why is it critical to cut the wire pairs off .5 inches or less before inserting into the connector?
Having the wire pairs untwisted and straightened for more than 0.5 inches will significantly reduce the performance of the cable. It increases the likelihood of crosstalk and performance issues.
- Why is it critical to make sure that all of the wires are pushed to the end of the connector?
If the wires are not pushed to the end of a connector, then it is likely there will be no connection.
- Why is it recommended to double check the wire order and make sure the wires are to the end before crimping?
Double checking the wires before crimping confirms that the wires are in the proper place and that there is no poor crimping as a result. There is also the potential for poor connectivity from incorrect wire pair order and loose crimping.
- How is a continuity tester different from a certification tester?
The difference between a continuity tester and a certification tester is the extent of their verification. A continuity tester simply checks to see if the circuit’s connection is or isn’t connected, while the certification tester checks for that, but also checks if the implemented cabling itself is up to standard.
IT 315 – Hands-On Exercise 1 Discussion
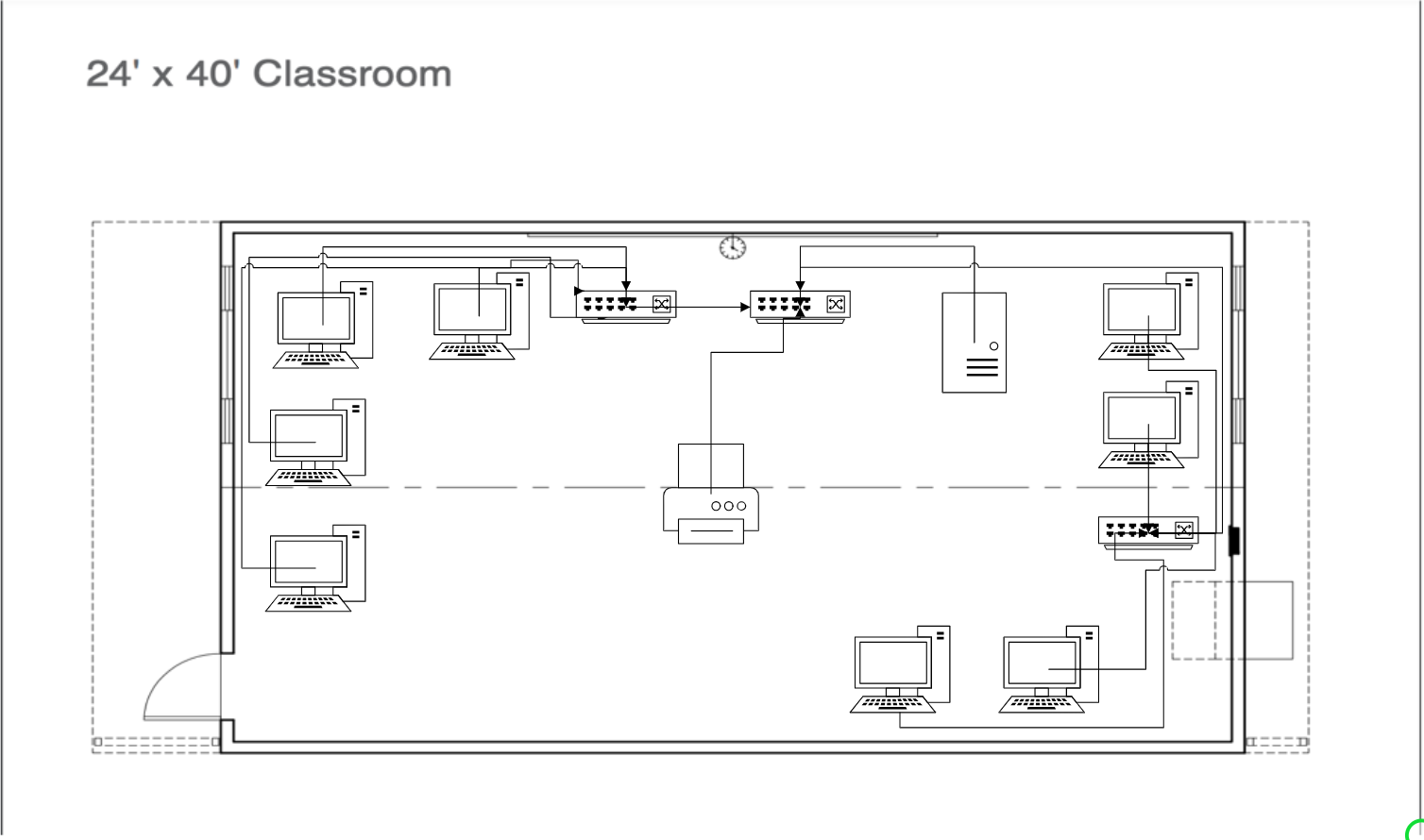
Post your design and explain why you chose it.
In my design, I wanted to focus on people having to deal with minimal difficulty when trying to access their computers, the server, or the printer. That’s why aside from the printer’s cable; all cabling is across the walls. However, this led to needing long cables to cover the distance, so I chose two packs of 14-foot cable and one of 10 feet. My total number of used cables ended up at twelve and required three 5-port switches. I also made sure that computers were grouped evenly by having one set of four on the left and two sets of two on the right sides of the room. Furthermore, from the original prompt, there was a focus on people needing to access the printer without tripping over cables, so I decided to put it in the center of the room, that way, regardless of either side, people can just walk to it without any hassle.
Costs:
- Three NETGEAR 5-Port Gigabit Ethernet Unmanaged Switch (GS105NA) = $120
- Two 14 ft. Cable Matters 10Gbps 5-Pack Snagless Cat 6 Ethernet Cable = $44
- One 10 ft. Cable Matters 10Gbps 5-Pack Snagless Cat 6 Ethernet Cable = $19
- Total: $183