Course Description
This course introduces basic terminologies used in ethical hacking (where the good guys pay good hackers to test their own security) and useful tools for penetration testing (hacking into web application, computer itself, and much more) Kali Linux. I worked with Metasploitable, Burpsuite, Wireshark, windows machines, etc. to do things such as capture the flag exercises (to get information/files/permissions of an administrator where we should not have them).
Course Material
I worked with cross site scripting in a capture the flag exercise, and this introduced me to various scripting languages such as php, python, and BASH. This helped me develop sleuthing skills necessary to ethically hack a network among other infrastructures. I practiced changing file permissions in order to copy and change files that I typically should not have access to using an administrator account that I hacked into in a previous week’s assignment as well. What I worked on included vulnerable websites, servers, and more.
The following is the last flag in one of the capture the flag exercises. Essentially, I typed out a script in python that would read the website and print me information I needed to locate where the flag (file) is. I used things like cookies, and interesting file names in places that I would check out with Burpsuite. Sometimes these cookies or files (which were hosted on a vulnerable website) would point me to another file that would be the flag file. More often than not, the flag would be encrypted with Base64 and I would have to decrypt it. I would then make a secure copy of the flag and use that for submitting the assignment.
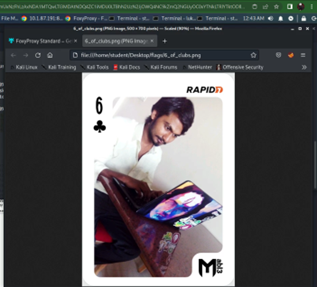
Pictured above is the flag file opened up, the 6 of clubs.
Below is the entire assignment (part 5 of my capture the flag exercises using Metasploitable and Burpsuite).
Metasploitable-CTF-Part-5-J5