Journal 1
Cyberspace Intelligence is very appealing and interesting to me because it requires collecting, processing, analyzing, and disseminating information gathered on state and non-state actors that would do harm to the United States. For Cyberspace Intelligence, being an All-Source Intelligence Analyst is something very appealing to me because I enjoy taking all the pieces of information available and putting them together to make a complete picture.
Oversight and Governance would be the least appealing to me because I come from a background where I am trying to support units who are taking action against targets, rather than implementing or drafting policy. I understand the importance of Oversight and Governance positions such as Cybersecurity Workforce Management, but it’s just too broad of a scope for me to really have an interest and I feel it would have the least amount of job satisfaction. I would much rather be the person taking action against an adversary rather than the person managing the cyberspace and the personnel working in that environment.
Journal 2
Practically all scientific principles apply to cybersecurity just as much as any other field of study, but here are three principles that should be followed when conducting cybersecurity research. A serious study of cybersecurity requires objectivity to rely solely on the facts and the data as they are observed, recorded, and analyzed. There may be multiple hypotheses for how to approach and solve a cybersecurity question/issue, but they all require an independent and objective look at the problem to find the correct solution.
Furthermore, cybersecurity must also adhere to the principle of parsimony. While there may be multiple solutions found to answering a cybersecurity issue, the easiest to understand and simplest solutions possible should be adopted. Parsimony requires a cybersecurity researcher to break down an issue to its most basic parts and in turn come up with as simple a solution as possible. This will maximize efficiency and make it so others can understand the solution and repeat the process.
Finally, a third scientific principle that cybersecurity researchers should adhere to is empiricism. Only serious discussions and research based on observable facts and data that are repeatable and observable to others should be used during research. This will ensure that any future research is well informed and also based on factually correct studies.
Journal 3
The information on data breaches contained in PrivacyRight.org could provide several key pieces of data for researchers. From a temporal perspective, the trends and patterns on data breach could provide researchers with greater information how cyber actors have used different methods to conduct their data breaches over time, what types of attacks are trending or waning in their use, and how long it takes for a new attack method to gain more prevalence in cyberspace until network defenses can be implemented. From a geospatial perspective, the locations of the victims of data breach can help researchers to determine where in the United States cyber actors are directing their attacks and what kinds of victims they are targeting. This could help inform researchers about the areas with the most threats to their data integrity, as well as identify locations that have not experienced as many cyber attacks but may still be vulnerable due to a lack of experience in defending against these attacks.
Journal 4
Maslow’s Hierarchy of Needs relating to Technology:
At the bottom of Maslow’s Hierarchy of Needs are physiological needs, such as food, water, shelter, and heat. These are things that I need to physically survive. Technology today enabled me to use digital pay to order cooked food through Uber Eats or groceries through the Amazon delivery app. I can also use online apps like YouTube to learn more about certain types of survival skills, such as how to start a fire in different climates or environments. There are even apps I can download that will help me to identify edible plants and mushrooms depending on my location in the United States.
The next level on Maslow’s Hierarchy of Needs are safety and security needs. The things I need to maintain my own personal safety. I use a camera system and fire alarm that are connected to my home’s WiFi, and the system will give me any notifications whenever there is a security breach or a fire is detected.
The third level on Maslow’s Hierarchy of Needs is a sense of love and belonging. I need a sense of community to live in. This is where social media such as Facebook, Instagram, and Reddit come into play. We use Facebook almost daily to stay in contact with our friends, family, and significant others. There is even a Facebook group for the neighborhood I live in where my neighbors can share updates on local events or happenings where I live. Of course, I also use my smart phone to access these apps, and use my phone to text, call, or video chat with my loved ones whenever I am off on a business trip.
The fourth level on Maslow’s Hierarchy of Needs are self-esteem needs. I need a way of knowing that my efforts are being validated and appreciated by others. My workplace uses an online interface to track my work performance, and my supervisor also uses this interface to provide feedback on my quarterly performance. All of my performance evaluations are saved in a database that is accessible to any current or future supervisors, that way if I want to switch positions, I can bring my previous performance ratings with me to interviews to prove my efforts are satisfactory.
Finally, at top level of Maslow’s Hierarchy of Needs are self-actualization needs. This is my need of knowing that I am improving myself as much as possible and meeting all of my personal goals in life. It is also a sense of knowing that I am the decider of my fate and that my life choices are my own. One of the many technologies I use to do this is through my online coursework at ODU. Some of the reasons why I am attending school are to better educate myself, become a more well-rounded person with marketable skills, and to keep myself on a course for personal and professional success.
Journal 5
Of the seven individual motivations for why people commit cybercrimes, I think I would rank them from making most sense to least sense in this order:
- For money: I find this one to make the most sense, since so many cybercriminals commit identity theft, ransomware attacks, or fraud for monetary gain everyday. Crime of many kinds are often committed for financial gain, and cybercrimes are no different.
- Political: Many cybercriminals are motivated by political/ideological reasons to target government entities or political figures. Sometimes these criminals are acting as private entities without any direction, but other times they are acting on behalf of a rival government to target another nation to undermine their opposition. Many state-sponsored cybercriminals are active throughout the world and are attempting to undermine their rivals, such as those acting on behalf of the Russia to target Ukraine.
- Multiple Reasons: I think this one is a bit of a cop-out, but honesty many cybercriminals can have multiple reasons for why they commit their crimes. Perhaps they started out for financial reasons, but learned they have fun learning how to formulate phishing attacks or get a thrill from successfully gaining access to confidential information on a company’s secure server.
- Entertainment: I find this very compelling, especially for younger people who are still teenagers or in their early twenties. Sometimes lightheartedly mocking people online can turn into harassment, or even cyberbullying. Swatting has become a common cyberattack against people, with the cybercriminals rejoicing when the police respond to a false shooting at their victim’s home with pleasure.
- Revenge: Revenge can be a powerful motivator for cybercriminals. Revenge porn especially is a recent phenomenon when the victims’ private sexual activities get leaked online without their consent. However, I don’t think this type of motive for cybercrime is nearly as prevalent as the others.
- Boredom: I think this is also a less prevalent motivation for cybercriminals. Yes, people are curious about the world, and they probably do commit crimes out of boredom, but this is a short-lived form of motivation. Cyberbullying is committed out of boredom, but they are often committed more so for the entertainment value.
- Recognition: I don’t find this motivation to be very common outside of black hat circles and very niche groups of online cybercriminals. Most cybercriminals want to remain anonymous, and don’t want any attention, adoration or admiration from their peers.
Journal 6
There are several ways to identify a fake website from the real website. One great way to tell the difference between the two is to closely look at the URL to make sure it does not contain any strange spelling or typos. The example below shows a fake site spoofing the login page for an Amazon account.
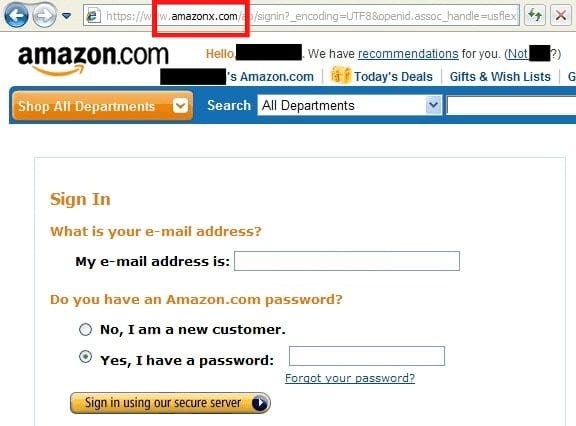
Another ways to tell the difference between the fake site and the real one is to scrutinize the HTTPS portion of the address. HTTPS means the site is using secure encryption on the internet, while HTTP means the site is not and is thus very vulnerable to hackers.
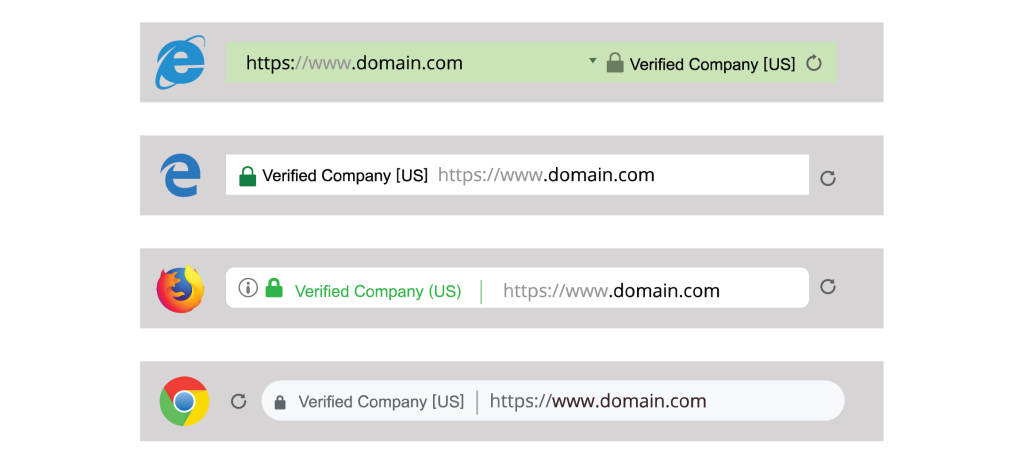
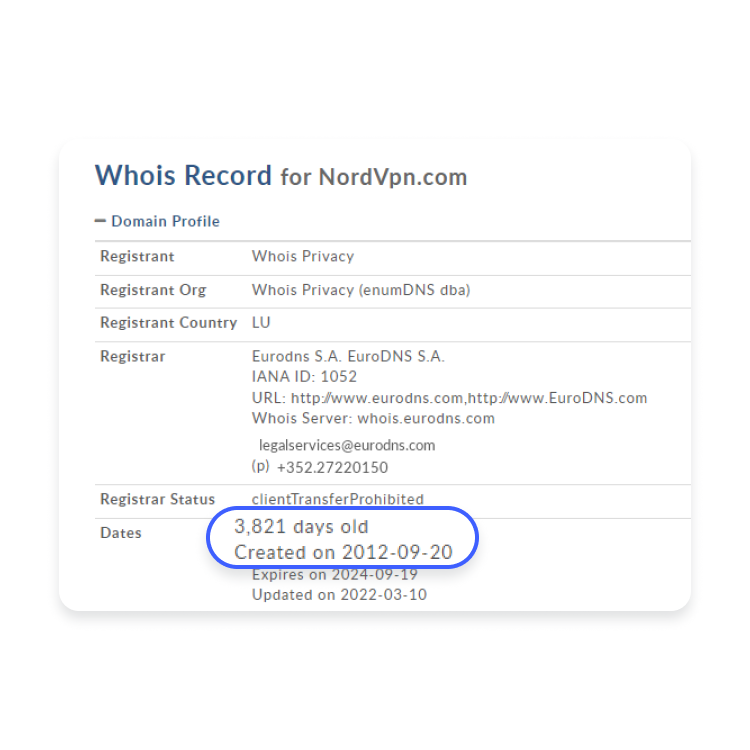
Finally, a third way to check whether a website is fake or real is to use online resources such as WhoIs. WhoIs can provide the domain information on a URL, and will provide clues on who registered the website, where are they are located, and when they created the website.
Journal 7
Here are three memes as they relate to the human factor of cyberseecurity.
This meme makes me relate to how I feel when I need to call the IT Help Desk. Sometimes I feel like a silly dog who doesn’t even know how to operate a computer, let alone fix something whenever an application goes down. Then I call the help desk and all I can do is follow their commands like a lost puppy.

Tech Bros are often seen as these computer gurus who live in upscale apartments in rich urban cities. However, they’re just like anybody else, and they can also become victims of cybercriminals just like anybody else. While members of the Tech community are often seen as immune to cybercrime, they are just as vulnerable as anyone else. This meme is a friendly reminder that we should all maintain awareness of our surroundings and cybersecurity at all times and in all places, since cybercriminals can potentially be anywhere too.

A good cybersecurity practice for any organization is to have two-factor authentication activated for all of your online accounts. Not just social media but also your banking and financial accounts should have 2FA. It can sometimes be frustrating to have to constantly use 2FA, but it will help you significantly to keep you safe from cybercriminals. Consider it as another line of defense in the “human firewall” of your online footprint.

Journal 8
Watch this video and pay attention to the way that movies distort hackers. Hacker Rates 12 Hacking Scenes In Movies And TV | How Real Is It? – YouTube
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity.
Media tends to drastically simplify the tactics, techniques, and procedures that cybersecurity professionals used to properly and securely do their job. The first clip showed a clip from the James Bond film “Skyfall”, and we see Q just go ahead and plug a uncleared device into his forensic toolkit without first securing or ensuring the device is safe to use. In addition, this first clip really shows how the media will falsely portray certain types of code or programming to look interesting, complex, and beautiful. However, these are just fancy computer graphics and stunning visuals that are meant to engage the audience and do not explain at all what is really happening. Even the Hacker Expert doing the review calls out how the film isn’t even using the correct characters to hexadecimal.
Even when the media does go the extra mile to portray hacking in a very realistic manner, such as with “Mr. Robot”, “Ocean’s 8”, or “The Social Network” the timelines to conduct certain types of actions or attacks are far too short and compressed for the sake of filmmaking and telling a story. Most of the hacks in the media are portrayed as being done with little time and effort, and often oversell the abilities of hackers in cyberspace. There are also still small flaws when the media gets something nearly totally faithful to real life, such as during “The Matrix” when Trinity is using fingered gloves to type her code. This is definitely a no-go for people who work regularly on computers, and makes for very difficult time when trying to write code or execute commands.
Journal 9
Complete the Social Media Disorder scale. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
Using the Social Media Disorder scale, I scored a 4 out of 9. The scale requires a score of 5 out of 9 for a formal diagnosis of “disordered social media user”. I think the items on the scale are useful for measuring dependence on social media, but are heavily focused on the negative aspects of social media. This does tend to skew things towards a biased view of how social media can affect people’s lives. The world is full of very diverse cultures and attitudes regarding technology and public engagement. Not every culture is completely like another, and naturally there will be differences in their views on social media.
Journal 10
Read this and write a journal entry summarizing your response to the article on social cybersecurity
After reading this article, the differences between traditional cybersecurity and social cybersecurity stands out most to me. From the article, ‘Traditional cybersecurity involves humans using technology to “hack” technology. The target is information systems. Social cybersecurity involves humans using technology to “hack” other humans. The targets are humans and the society that binds them. This twist on the traditional cyber paradigm is sometimes referred to as “cognitive hacking.”’ Social cybersecurity is very much akin to how psychological warfare has been waged throughout history. The aim is to convince and influence both friendly, neutral, and hostile populations enough to change their perceptions to meet the strategic goals of the attacker. However, the key difference is the method of delivering these effects through technology used in cyberspace. The information warfare that is being conducted in the 21st century will require new responses, new doctrine, and new training for governments, militaries, and civilian populations throughout the world. Preventing an adversary from “hacking” their target audience through information warfare will require increased education at the local, state, and federal level. It will also require a multidisciplinary approach, just as the author states in the article. There will not be a single effective approach to fully counter “social hacking”.
Journal 11
Watch this video. As you watch the video https://www.youtube.com/watch?v=iYtmuHbhmS0, think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
One of the key duties of a cybersecurity analyst within an organization is to provide security awareness and training to other members of the organization. This training could include teaching others about proper cyber hygiene such as using complex passwords and multi-factor authentication. The cyber awareness training could also include trying to change the social behaviors of the employees at work, such as knowing how to identify different social engineering attacks such as phishing emails, or knowing when not to click on suspicious links to fake websites from a workstation. Not only do cybersecurity analysts have to protect the software and hardware or the organization, they also have to harden the “human firewall” of the organization through increased education and training. This will require a constant amount of training and research since the threats and types of social engineering attacks facing an organization are always evolving.
Another factor mentioned in the video is the quality of life and economic opportunities for a cybersecurity analyst depending on where they live in the country. Many major urban centers offer plenty of job opportunities, but at the added cost of living in a densely populated area with increased costs of living. There are also other social factors that affect the hiring of a cybersecurity analyst, particularly for jobs with the US government that require a security clearance and background check. These types of jobs require someone to be able to operate with a high degree of trust, and a past history of committing certain types of crimes, reckless behavior, or drug use can disqualify a candidate.
Journal 12
Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdf sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
There are several economic theories related to the data breach letter, but here are two that relate to it. The letter directly relates to the Costs/Benefits Analysis that the company owning the website Glasswasherparts.com conducted after learning of the data breach. The company weighed the financial and reputational costs of allowing this data breach to go unannounced to their customers, and decided that it was most cost effective to inform their customers of the breach and handle the short-term costs of having to remediate the issue.
The second economic theory is the Risk Assessment conducted by the company when setting up their online presence. The company uses a third-party company as their “platform provider”, and it was the platform provider’s systems that experienced the intrusion. The company likely determined the risk to their assets through this third party’s cybersecurity policies was acceptable and a certain threshold of damage was acceptable.
The two social science theories that relate to the letter could include the theory of Rational Choice. The company determined that it was in their best interest to use a third-party vendor to provide a platform for the company. This decision was probably made based on the reduced costs of using an existing vendor’s platform, rather than increasing the costs of directly hiring people to build and maintain a custom platform for the company from the ground up. Using a third-party also helps reduce costs in cybersecurity, since the vendor very likely has their own cybersecurity policies and personnel in place to secure the platform.
The second social science theory that could relate to the data breach letter could be Keynesian economic theory. This theory holds that there should be increased funding and incentives from the government to support private sector businesses. The letter points out that federal law enforcement has been contacted and they have been conducting an investigation into the data breach. The more law enforcement gets involved in investigating, punishing, and preventing data breaches, the more secure the rest of the private sector could become in the event of future cyber incidents.
Journal 13
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
This study’s authors set out to help define the benefits of bug bounties for finding cyber vulnerabilities for firms and businesses from various sectors. In doing so, they were able to provide some hard, empirical evidence that bug bounties do in fact help to reduce the threat of these kinds of vulnerabilities. Also interesting was that the brand and profile of the company actually did not have an outsized affect on the efforts of ethical hackers to identify vulnerabilities.
Journal 14
Andriy Slynchuk has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
Andriy Slynchuk’s article lists the following eleven things Internet users do that may be illegal:
- Using Unofficial Streaming Services
- Using Torrent Services
- Using Copyrighted Images
- Sharing Passwords, Addresses, or Photos of Others
- Bullying and Trolling
- Recording a VoIP Call Without Consent
- Faking Your Identity Online
- Using Other People’s Internet Networks
- Collecting Information About People Younger Than 13
- Extracting Audio From YouTube
- Illegal Searches on the Internet
Out of the eleven things that Andriy Slynchuk describes as illegal, here are the top five I would consider the most serious violations based on the type of crime and severity of the penalties.
Using unofficial streaming services can carry serious fines for even casual users due to copyright infringement. These fines can range from between $750 to $30,000 per instance of using these types of service to illegally watch movies or TV shows (Huppertz and Powers, Internet Crime: Penalties for Illegal Streaming, 2019). Users who upload content onto illegal streaming services, can face up to $150,000 in fines (Huppertz and Powers, Internet Crime: Penalties for Illegal Streaming, 2019).
Faking your identity online, which can include acts of identity theft and fraud, can carry serious misdemeanor or felony charges depending on the severity of the crime. According to the US Department of Justice, identity theft “carries a maximum term of 15 years’ imprisonment, a fine, and criminal forfeiture of any personal property used or intended to be used to commit the offense.” (US Department of Justice, Criminal Division | Identity Theft, 2023).
Collecting Information about people younger than 13 is a direct violation of the Children’s Online Privacy Protection Act (COPPA). According to the Electronic Privacy Information Center, anyone found to be violating COPPA can be given a $43,792 fine per violation (Electronic Privacy Information Center, Children’s Privacy, 2024).
Conducting illegal searches on the Internet through a search engine such as Google can lead to some severe civil or criminal penalties, depending on the search. Illegal searches could include murder for hire, purchasing illegal drugs, learning how to make an improvised explosive device, and searching for sexually explicit material of minors under the age of 18.
While bullying and trolling may seem like they are just a part of everyday life on the internet, there are several instances where it can go too far and even lead to prison time. One infamous example stems from an online video game argument that led to a prank called swatting. Swatting is when someone falsely files a police report on an active crime and provides the police the address of their victim. The goal is to prank the unsuspecting victim into having a police SWAT team raid their home. In the 2017 Wichita Swatting case, police raided a home and fatally shot the victim. The individual who called in the swatting was given prisons sentence of 20 years (Almasy and Alonso, CNN, His ‘swatting’ call led to the death of a man. Now he is going to prison for 20 years, 2019).
Journal 15
Digital Forensics | Davin Teo | TEDxHongKongSalon
– YouTube
Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
The speaker, Davin Teo got his start as a digital forensic investigator almost by accident. As he recalls, there wasn’t a dedicated career path for digital forensics, no courses to take, and no clearly defined method for how to get started in the field. However, because of the way our economy was becoming more and more integrated with the cyber domain, especially in finance, this was the pathway that led Davin into this career field. As Davin states, he was originally an accountant at a small firm that enjoyed tinkering with computers and helping out his firm in the IT field. Eventually, Davin was lucky enough to be given an opportunity to join one of the first digital forensic firms in Australia, and that was when he states he felt he had found his calling. I think Davin’s path shows that our passions and hobbies can sometimes lead us down the path we were meant to go down, and it just takes that one opportunity or moment to go for it.