-
Week 1 – Journal Entry
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
-
Week 1 – Journal Entry
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
-
Week 1 – Journal Entry
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
After examining the NICE Workforce Framework, I came across a category that piqued my interest. The category is Investigate. Within this category, Cyber Investigation piqued my interest the most. A Cyber Crime Investigator is responsible for identifying, collecting, examining, and preserving evidence utilizing controlled analytical and investigative techniques. This is something I am very interested in, and believe it will keep me on my toes. An area that does not seem appealing to me would be Training, Education, and Awareness. But, to be more specific, Cyber Instructional Curriculum Developer. This is something that I could never see myself doing. Teaching is not for everyone, and I can definitely say it is not my forte. I am more so of a behind the scenes type of person, and I just don’t think this would be a role I would flourish in.
Week 2 – Journal Entry
Explain how the principles of science relate to cybersecurity.
The principles of cybersecurity and the principles of science relate in many ways. Cybersecurity is the process of defending computer systems, networks, and data from unwanted access, attacks, and damage. The scientific principles of cybersecurity aids in recognizing and combating threats effectively. Here are some ways the two relate, experimentation, hypothesis testing, continuous improvement, empirical observation, risk assessment and many more. The principles of science give a organized and evidenced based approach to understanding, addressing, and mitigating cybersecurity threats. When cybersecurity professionals apply these principles, it allows them to perform better.
Week 3 – Journal Entry
Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches?
After visiting the site and seeing what they have to offer, I came across a couple of ways researchers might find this site helpful to study breaches. This site breaks down and clarifies privacy rights and choices. On the homepage, there are two sections talking about the United States data breach reports in 2022 and 2023. In the left sidebar, you can click on resources; and listed under resources is law overviews, reports, and advocacy. I specifically want to talk about the reports sections because that is where you can find the information needed to do research on data breaches. Once you click on it, it gives you articles pertaining to information about data breaches. The articles listed are very detailed and packed with information.
Week 4 – Journal Entry
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
Maslow’s Hierarchy of Need touches on human needs and they are categorized into five different levels. Self-actualization: achieving one’s full potential, including creative activities. Esteem needs: prestige and feeling of accomplishment. Belongingness and love needs (social needs): intimate relationships/friends. Safety needs: security and safety. Physiological needs: food, water, warmth, and rest. These all then fit into larger categories self-fulfillment needs, psychological needs, and basic needs. An example I have for self-actualization that involves a digital experience would be the app Duolingo which is an app where you can learn different languages through and educate you. Another thing would be the use of technology to secure personal data used when online banking, password protection, and health/fitness apps and this has to do with the safety needs level. Something else I could talk about is esteem needs. Social media platforms such as TikTok, Instagram, and Facebook are all heavily used platforms that people use. This can fall into the level of self esteem because there are some individuals who use the amount of their views, followers, and likes to validate themselves which boosts their self esteem because of their social status.
Week 5 – Journal Entry
Review the articles linked with each individual motive in the presentation page or Slide #3. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
The seven motives are entertainment, political, revenge, boredom, recognition, for money, and multiple reasons. Based off if the articles and the reasoning’s behind these motives, if i had to rank them from 1 being the most sense and 7 being the lest sense, here is how I would rank them: 1. Revenge, 2. For Money, 3. Recognition, 4. Political, 5. Entertainment, 6. Multiple Reasons, and 7. Boredom. For money makes the most sense to me. When it comes to cybercriminals, revenge and for money are usually their main motives. Revenge made the most sense to me to be first when it came to motives. Cybercriminals usually target specific companies or individuals due to the injustice caused to them by them so seek out ways to make them hurt and cause harm. There are so many ways cybercriminals can make a lot of money from their attacks. All the way from financial fraud to ransomware. This was close to being first but is a close second. Recognition and Political are ranked in 3rd and 4th place because some cybercriminals like the attention they get for completing a really big hack. They seek the validation and it boosts their ego and this is what pushes them to go bigger and better. When it comes to political some cybercriminals like to spread propaganda and try to mess up the political process. Sometimes, there are even state-sponsored cyber attacks that could have something to do with political gain. Next, we have Entertainment and Multiple Reasons ranked in 5th and 6th place. These motives were harder for me to dissect and are some of the lesser common ones. Some cybercriminals simply attacks for the thrill and for of it they get from it while others have so many other motives that makes it really hard to pinpoint what their exact reasoning is. Lastly we have boredom coming in 7th. This one made the least sense to be. It was the least justifiable on to me.
Article Review #1
Week 6 – Journal Entry
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?
When it comes to identifying fake websites it can be easy or a little challenging. Depending on skilled the creator of the website is, you can easily be fooled. There are fake websites that are bad and will affecting your software in some kind of way and there are some that are harmless. There a many red flags and things to look out for when it comes to identifying a fake website. When you click on a website and you notice in the search bar there is no “https://” in the URL and a lock sign, this could be an indication of a fake website because most legitimate websites have the “https://”. If your on a website and you’re trying to purchase an item and you see that there is no contact information and you see a lot of unrealistic offers or things that may seem too good to be true, it probably is so stay away from it. Another thing to look out for would be websites that are poorly designed and do not have any privacy policies or terms of service as these can be a big red flag showing that the website was rushed to be published and there wasn’t much effort behind the creation of this website. In comparison with real websites some things you will notice it will have the “https://” in the URL. Real websites have clear information. There will be no confusion and the website will be very easy to navigate. The contact information will be very clear. They will have terms of service and policies because they take their business seriously. The layout of the website will be very nice and coherent.
FAKE WEBSITE
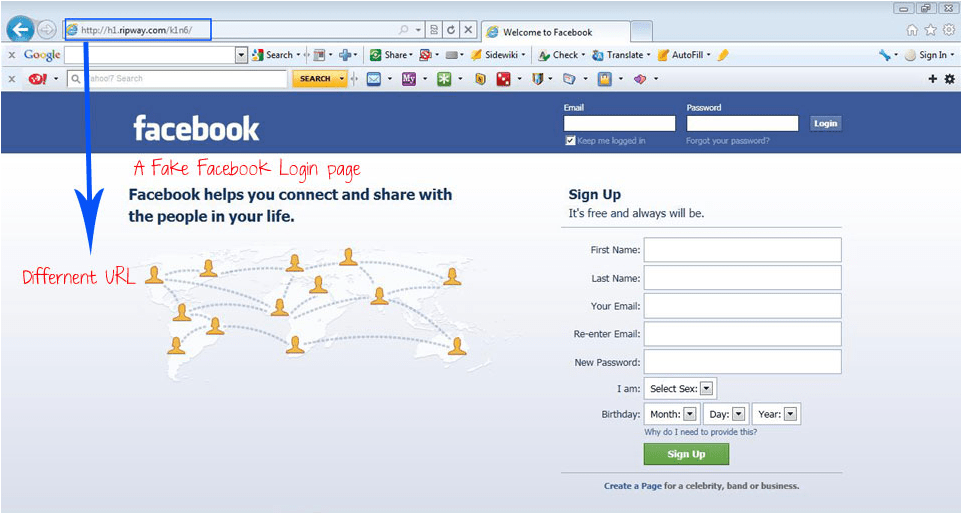
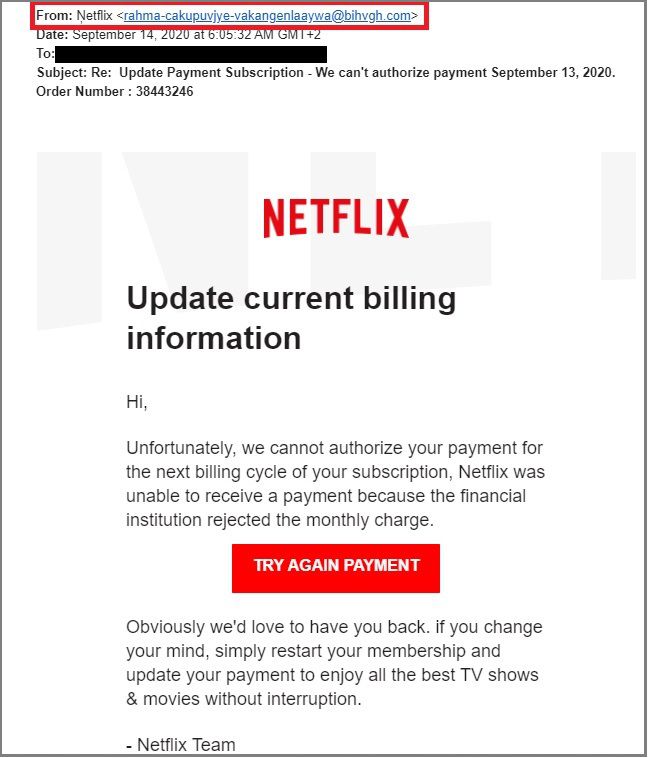
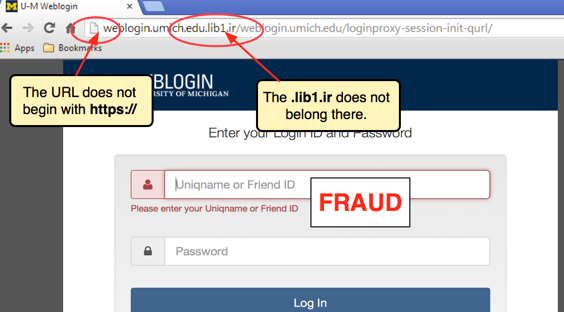
REAL WEBSITES
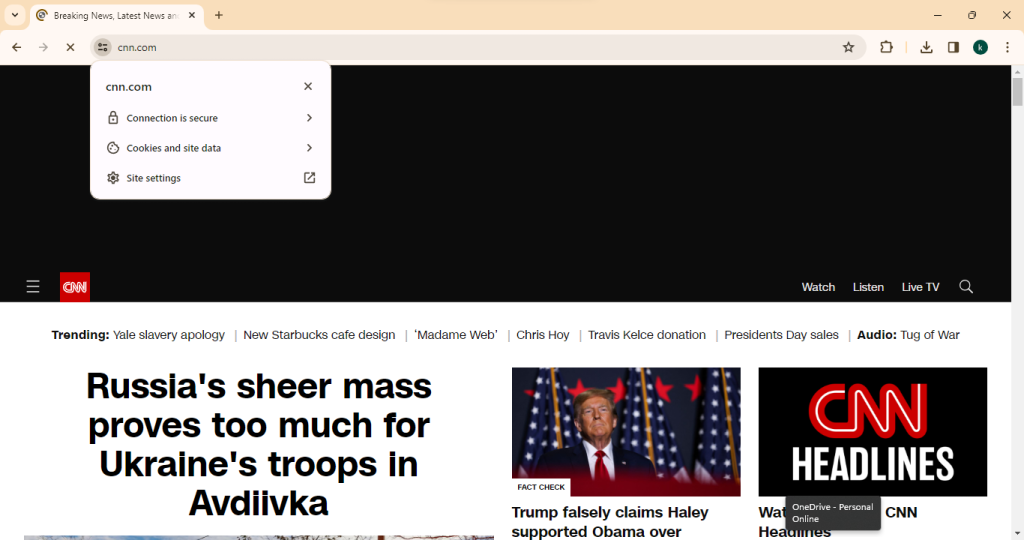
Week 7 – Journal Entry
Review the following ten photos through a cybersecurity human systems integration framework. Create a meme explaining what is going on in the individual’s or individuals’ mind(s).
https://commons.wikimedia.org/wiki/File:CellPhone_(16491636068).jpg

Meme: I love how I can capture everything in just a click of a button!
This meme/photo relates to human system integration framework because it is so important to make sure individuals know how unsafe it can be when taking pictures and videos and posting them online. The security implications that can be caused from taking a picture can lead to something preventable. By taking pictures you can involuntarily share super sensitive data that might cause harm to you and the people around you. In doing this you share information of location based off of your background. It can be a privacy concern when it comes to sharing photos online. It is so important to make sure you are double checking and being very cautious about what your privacy settings are on.
Week 8 – Journal Entry
Watch this video and pay attention to the way that movies distort hackers.
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity
This video really examines how hackers are portrayed in films and television programs, and this really made me think about how the media affects how we see cybersecurity. The differences between fact and fantasy in these portrayals is very direct, with the exaggerated hacking scenes that sometimes border on the bizarre. It is very clear to see that the media often times tends to exaggerate and misrepresent parts of cybersecurity for a more dramatic effect. To be more specific, Hollywood in particular appear to be obsessed with the idea of hackers as hoodie-clad, secretive geniuses who can enter any kind of system with just a few simple keystrokes and clicks of a button. This perception of them not only oversimplifies the complexities of the cyber dangers in the real world, but it also reinforces the perceptions of hackers as antisocial loners or even worst monster which isn’t always the case. Now when it comes to media consumers, it is important to approach these kinds of depictions with very critical and smart thinking. After watching the video, when I now see a hacking scene in a movie or on a television show, it will be easier for me to be able to point out the possible influence on public perception when it comes to cybersecurity.
Week 10 – Journal Entry
After watching the video about how cybercriminals can your your social media post to get your personal information and or even sell it. In this video, it goes to show how a man is obsessed with sharing his whole life on social media. He updates his feed multiple times a day sharing the events taking place in that very moment. It shows how this is a swimming pool for hackers and how dangerous it can be to you because you don’t t realize how much information cybercriminals can get from you posts. I then completed the “Social Media Disorder scale.” After answering those questions, I only answered yes to one of those questions. I do not find myself on social media ofter. I feel is if I have very good self control when it comes to social media. I never knew that this was even a disorder people have. The questions in the scale were interesting, but many did not apply to me. I think that many people struggle with this because this generation is revolved around social media. You’re not relevant vent to most people unless you have a big following and a well known social status. It’s honestly sad to me and I fear that it is only going to get worst as the years go on.
Article Review #2
Week 11 – Journal Entry pt.1
After reading this article, it clarified the complex relationship that exists between the social dynamics and cybersecurity risks. It really emphasized the need to incorporate social sciences into conventional cybersecurity tactics. The writers really go into detail about how the digital would has changed, and they highlight the growing importance of social media networking sites and the resulting risks they can provide. The article really stressed how important it is for security specialists and politicians to fully understand the social aspect of cybersecurity. By recognizing the connections between human behavior and technology systems, it allows for the development of a more comprehensive cybersecurity strategy. This includes using social science approaches to effectively foresee and minimize future threats.
Week 11 – Journal Entry pt.2
After watching this video, there were so many social themes pertaining to the cybersecurity analyst position surface. The focus on the communication abilities really highlights how crucial it is for professionals in the field to have productive interpersonal relationships. In order for cybersecurity analysts to properly handle security concerns, they frequently work with a variety of teams, including executives, IT specialists, and even law enforcement authorities. This shows how important it is to have good social skills in order to communicate technical knowledge to stakeholder who are not technical and to help firms develop a culture that is security aware. All in all, the video emphasizes how social behaviors and cybersecurity interacts. It highlights the importance of clear communication, the interconnection of society, and group accountability in tackling cybersecurity issues.
Week 12 – Journal Entry pt.1
Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
After reading the sample breach letter, the economic theories that I chose that relates to this letter would be information economics and game theory. Information theory focuses on economics of information, including its creation, dissemination, and consumption. It can be used to analyze the consequences of asymmetric information between the firm and its customers in this breach notification letter. The imbalance of information is highlighted by the clients ignorance of of the breah until recently. Game theory can be examined through the strategic relationships between the business, its clients, and the possible enemies which in this case would be the invaders. The company deciding to reach out to customers, notifying them of the breach and offering suggestions for the next steps, shows us a calculated attempt to reduce the harm to its brand, uphold customer confidence, and reduce any legal risks. The social science theories I chose would be social exchange theory and crisis communication theory. In the social exchange theory, social interactions include costs and benefits bfits being exchanged. By being transparent about the incident and offering support in minimizing repercussions, the firm hope to preserve a good social exchange connection with its consumers through the breach information letter. Lastly, the crisis communication theory, looks at how companies interact with one another on times of crisis in order to protect their image while keeping their customers happy. In accordance with this theories guidelines, the breach notification letter quickly notifies the parties involved, explains the circumstances, and offers suggestions for reducing risks.
Week 12 – Journal Entry pt.2
After reading this article, you will see thorough examination of bug bounty programs and the effects that they have on cybersecurity. I would say, the study of the literature does a really good job of highlighting how important vulnerability disclosure policies (VDPs) are in motivating security researchers to report the flaws and also strengthen and organizations cybersecurity postures. The price of insensitivity of hackers taking pari in bug bounty programs is a really interesting discovery as it show businesses with minimal resources may nonetheless benefit from these initiatives. Furthermore, the study challenges the idea that larger or more prominent organizations are better positioned to fix cybersecurity vulnerabilities. This highlights the efficacy of bug bounties across all sizes and degrees of importance. In addition, the discovery of sectors like banking, retail, and healthcare that receive less complaints point to possible areas for development and heightened attention to cybersecurity measures in these businesses.
Career Paper
Week 13 – Journal Entry
Andriy Links to an external site.SlynchukLinks to an external site. Links to an external site.has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
After reading the eleven things Internet users do that may be illegal, the five that I thought were the most serious violations would be collecting information about people younger than 13, faking your identity online, illegal searches on the internet, bullying and trolling, and lastly, sharing passwords, addresses, or photos of others. Anything questionable involving a minor is not right and should be taken very seriously. Children are innocent and defenseless and could easily be taken advantage of. Identity fraud is very serious. Using another individuals information without consent is a crime and could be very dangerous for both parties. It is very important to be mindful of the things you search because the last ting you want is the Feds watching your every move because of something you once asked google. Bullying/trolling is never okay at any age. It is rude and cowardice. Cyberbullying, bullying, trolling is awful and it can be very hard on the victims. It’s simple just something you should not do. When it comes to passwords, addresses, or photos of others I just think to myself, what os someone did those things to you. You and I both know it’s not right so just don’t do it.
Week 15 – Journal Entry
Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
As i watched Davin Teo’s lecture on digital forensics, I was really able to see how his work and social sciences are so closely related. Teo explores the fields of technology and law enforcement in his work as a digital forensics investigator, but there is a little doubt that the social sciences have a role in some of his experiences. His career path seems to have combined technological knowledge with a keen grasp of human behavior, which i would say is the foundation of the social sciences. Deciphering the intentions, motives, and the behaviors of people inside the digital sphere is the core/what makes up digital forensics. It goes far beyond just decoding bits and bytes. Teo discusses in his speech, the need of comprehending human psychology and behavior in order to properly analyze cybercrimes. This emphasizes how important social sciences are the his line of work. I find his career path intriguing as it is complex and diversified. It is evidence of the multidisciplinary character of digital forensics, where technological expertise and social science ideas come together to reveal the intricacies of digital crimes. Thinking back on his speech, I’m impressed by how much Teo and other people have shaped our perceptions of crime, technology, and society.