Artifact #4
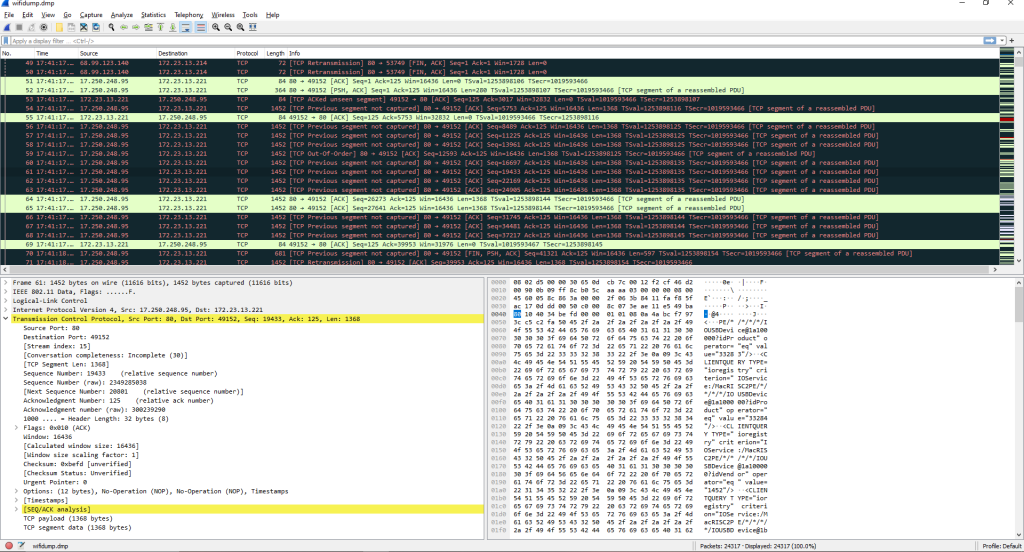
Description: One tool I’ve learned to use and downloaded myself that is detrimental to penetration testers is Wireshark. Not only have I learned to actively capture a networks traffic, I can then also analyze the packets captured to find clues about one’s network like login information or any text if unencrypted, IP’s within the network and in communication, and the transfer or download of unwanted files. These can be done efficiently by filtering the specific protocols that these actions may occur with.
Artifact #5
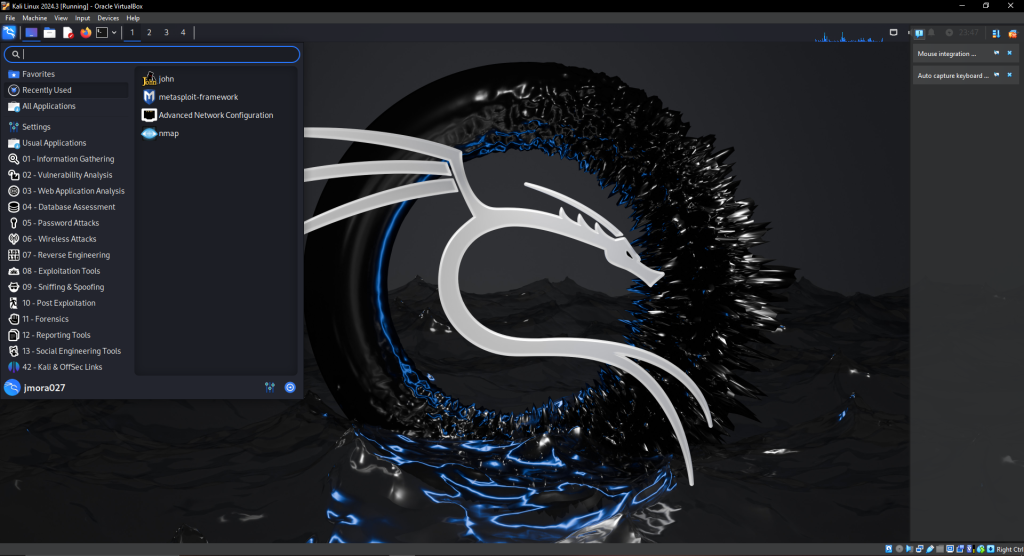
Description: To practice my skills on passive and active reconnaissance as well as vulnerability exploitation I created as virtual machine for Kali Linux. Familiarizing and using applications like Metaspoitable, nmap, and John the Ripper. Successfully combining these to break into legacy target systems using Windows 7 and Windows XP to allow me as the hacker the privilege’s of the admin user.
Artifact #6
Description: In my Ethical Hacking and Penetration testing class (CYSE 450), I had to find an open device on the internet and then conduct passive reconnaissance to find known vulnerabilities. I then had to give a description on how the device is vulnerable and possible ways the vulnerability could be mitigated.
annotated-Assinment_1_Passive_Reconnaissance.pdf.docx