Author's posts
Mar 05
Short Research Paper 1
A Deep Dive into the 2012 LinkedIn Data Breach: Vulnerabilities, Exploited Threats, and Lessons for CybersecurityNadia SimpsonOld Dominion UniversityCYSE300Malik Gladden9/10/2023 On June 6, 2012, LinkedIn, one of the world’s largest professional networking platforms, became the target of a massive cybersecurity breach that compromised the data of millions of its users. This data breach, which primarily …
Mar 04
Reflection
After years of hard work and perseverance, I am finally preparing to graduate from ODU with a bachelor’s of science in cybersecurity. However, my journey to this port in my life has not been easy. When I transferred to ODU in 2022, I faced one of the challenging periods of my life. I was suffering …
Mar 03
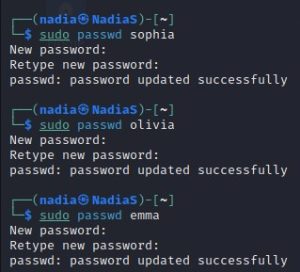
Assignment 6-File Permissions
Step 1. Create three groups- employee, payroll, and admin. (You may refer to the slides forweek-4 – Group Management) Step 2. Create three user accounts with a specified home directory for Sophia, Olivia, andEmma. Set the primary group for Sophia, Olivia, and Emma to “employee”, “payroll”, and“admin”, respectively. And change their login shell to /bin/bash. …
Mar 03
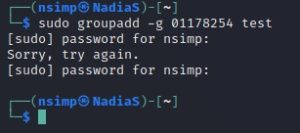
Assignment Lab4
CYSE 270: Linux System for CybersecurityAssignment: Lab 4–Group and User Accounts Task A –User Account management (8 * 5 =40 points) Open a terminal window in VM and execute the correct command to display the user accountinformation (including the login shell and home directory) for the current user using grep. 2. Execute the correct command …
Mar 03
Assignment 1
Mar 03
CS462 Term Report: Colonial Pipeline
CS462 Blog Post Background of Colonial Pipeline The Colonial Pipeline Company is a critical entity in the U.S. energy sector, which operates the largest refined products pipeline system in the nation. The company was founded in Alpharetta, Georgia in 1961 and the pipeline was fully operational in 1964. The Colonial Pipeline supplies fuel to most …
Mar 02
Homework 12
Short Answer Questions (short answers should generally be at least three to four sentences in length. However, it is important to be as concise as possible when responding.) or you may choose to Upload a Two-Minute Audio or Video recording to answer the following questions. Listen to “Episode #86: The LinkedIn Incident of the DarkNet …
Mar 02
Homework 11
Short Answer Questions (short answers should generally be at least three to four sentences in length. However, it is important to be as concise as possible when responding.) or you may choose to Upload a Two-Minute Audio or Video recording to answer the following questions. Module 9 & 10 One of the purposes of using …
Mar 02
Homework 10
Short Answer Questions (short answers should generally be at least three to four sentences in length. However, it is important to be as concise as possible when responding.) or you may choose to Upload a Two-Minute Audio or Video recording to answer the following questions. Module 7 & 8 1. What are the main problems related to fragmented files? The …
Mar 02
Homework 9
Short Answer Questions (short answers should generally be at least three to four sentences in length. However, it is important to be as concise as possible when responding.) or you may choose to Upload a Two- Minute Audio or Video recording to answer the following questions.Listen to “Episode #29: Stuxnet of the DarkNet Diaries podcast …