CYSE270
CYSE270 emphasizes the use of Linux through Kali Linux, exploring the underlying systems and how they function. Below are examples of the labs and hands-on exercises completed throughout the course.
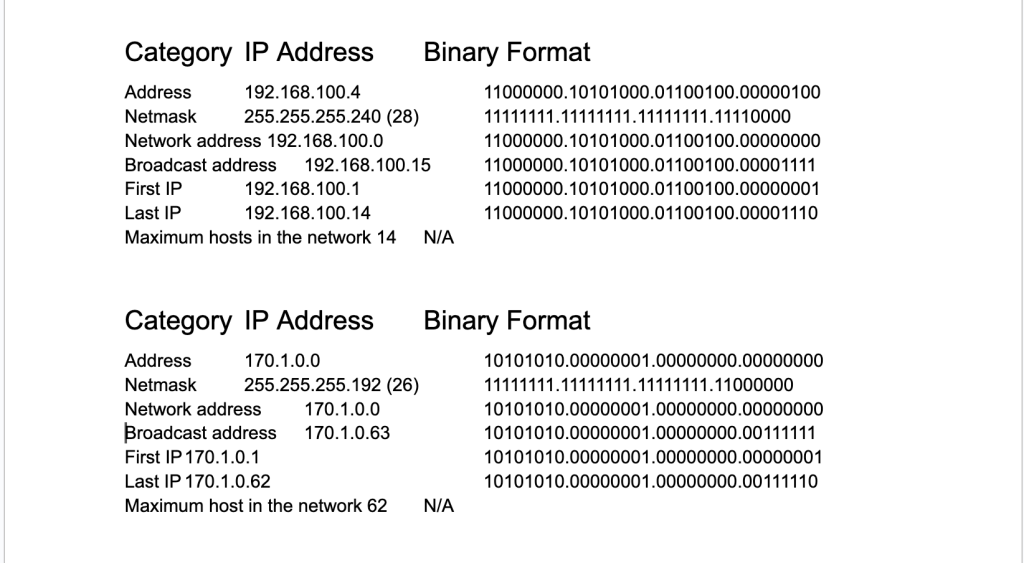
For Assignment 10, Networking Basics, we analyzed the network to identify key parameters, including the network address, broadcast address, first usable IP, last usable IP, and the maximum number of hosts within the network, as presented below as well as being in binary format.
For assignment created a shell script to automate backups of a user’s home directory by generating a timestamped, compressed tar archive and storing it in /var/backups/. The script was scheduled using crontab to run at regular intervals, providing consistent automated backups. This project strengthened my proficiency in Linux shell scripting, file management, and task automation.
Confirming Alice and running chmod (Above), after confirming that Alice exists opening Vi (below) while writing the procedure.
After this is closed and saved, you run the /var/backup which will all be presented below.
Throughout this course, I built a solid understanding of how Linux systems work and how to manage them confidently. Using Kali Linux every week helped me get comfortable with navigating the command line, working with files and processes, and understanding how different parts of the system fit together. I also learned how to automate tasks with shell scripts, set up backups, and schedule jobs using crontab—skills that make managing systems more efficient and reliable. Along the way, I strengthened my grasp of networking basics, including IP addressing, routing, DNS, and how to check and configure network interfaces.
All of these skills connect directly to cybersecurity. Being able to work smoothly in Linux is essential for using security tools, analyzing systems, and responding to issues quickly. Understanding networks helps with spotting unusual behavior and identifying potential vulnerabilities. Overall, this course gave me practical experience I can apply immediately in real cybersecurity environments.
