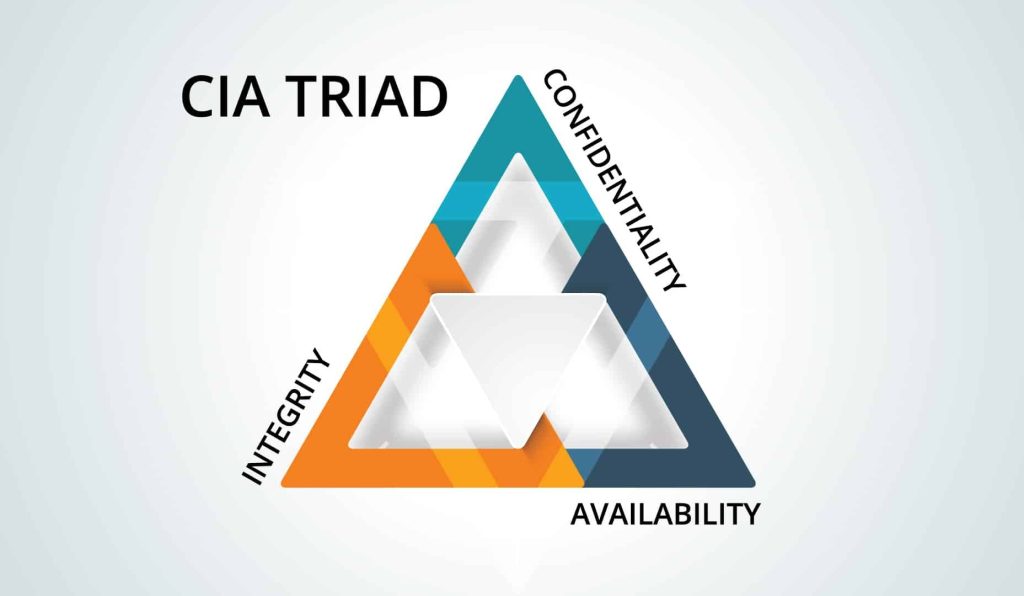
The CIA triad – Confidentiality, Integrity, and Availability – is a foundational model used within Information security that acts as a guide to create security systems or methods. Authentication and Authorization are important components of this foundation. With authentication ensuring that only verified users can access systems and authorization, they only access resources they need to. An understanding of these concepts is essential to ensuring proper cybersecurity measures.
Confidentiality
The first component, confidentiality, means to keep sensitive information a secret (Michali, 2023). This includes the various methods used to prevent leakage of that data like authorization, encryption, two-factor authentication and security tokens. In this way there are levels to gain access to important information and lowering the risks of breaches.
Integrity
Integrity is the maintenance of the authenticity and trust in data. This is to ensure that important information is free form tampering and remains accurate to use (What is the CIA triad and why is it important?). Some examples of this are seen in digital signatures to help with verification and monitoring modifications to data, Hashes and Checksums (Michali, 2023).
Availability
The last of the three, availability ensures the accessibility to systems and data when needed. This is done by having backups in case the system goes down, disaster recovery systems in place to help regain access quickly and securely (Michali, 2023). Without these in place, it can lead to a period of time where all systems are down and thus, a loss of money. Loss of systems operation can happen at any time for a variety of reasons in this way there is a plan to get it back.
Authentication vs Authorization
Authentication and Authorization are often mistaken for one another but serve two different purposes. Authentication verifies the identity of a user, system or device. In this way access to certain information is only to those who are verified to have it. Some examples of this include the use of passwords, one time pin (OTP) – which verifies a user’s identity through their device, and biometrics which are unique to each user (Authentication vs. authorization: What’s the difference?). Authorization is the access given to a user. Some examples of this includes role-based access control (RBAC), which specifies roles like admin, user and guest and attributebased access controls (ABAC), this uses aspects like location and time (Neray, 2024).
Conclusion
In conclusion, the CIA Triad and its components of authentication and authorization are fundamentals to cybersecurity. The triad establishes a guide to make sure that data stays private, intact and accessible throughout the entire security process. While authentication and authorization work together to control access to this information by appropriate and secure methods. Recognizing and leveraging this is crucial to implementing and developing cybersecurity.
References
Authentication vs. authorization: What’s the difference? OneLogin. (n.d.). https://www.onelogin.com/learn/authentication-vs-authorization
Michali. (2023, March 21). What is the CIA triad?. Check Point Software.
https://www.checkpoint.com/cyber-hub/cyber-security/what-is-it-security/what-is-the-cia-triad/
Neray, G. (2024, February 22). The 10 types of authorization. RSS.
https://www.osohq.com/post/ten-types-of-authorization
What is the CIA triad and why is it important?. Fortinet. (n.d.).