Essential Work Habits
- Ability to work methodically and is very detail oriented
- Eagerness to dig into technical questions and examine them from all sides
- Enthusiastic and highly adaptable
- Strong analytical and diagnostic skills
- Demonstrated skills in innovation and collaboration
- Keep a current understanding of vulnerabilities from the Internet
- Maintaining awareness and knowledge of contemporary standards, practices, procedures and methods
- Ability to get the job done
Soft Skills
- Excellent presentation and communications skills to effectively communicate with management and customers
- Ability to clearly articulate complex concepts both written and verbally
- Ability, understanding, and usage of active listening skills especially with customers
This PowerPoint presentation for CYSE 201: Cybersecurity and Social Sciences describes the intersection of Cybersecurity and Social Media.
Solid Technical Foundation
- Understand architecture, administration, and management of operating systems, networking, and virtualization software
- General programming/software development concepts and software analytical skills
- Proficiency in programming in Java, C/C++, disassemblers, and assembly language and programming knowledge of two or more scripting languages (PHP, Python, Perl, or shell)
- Understanding of how the different type of firewalls and network load balancers work
- Deep understanding of how network routers and switches work
- Evaluate and design systems and network architectures
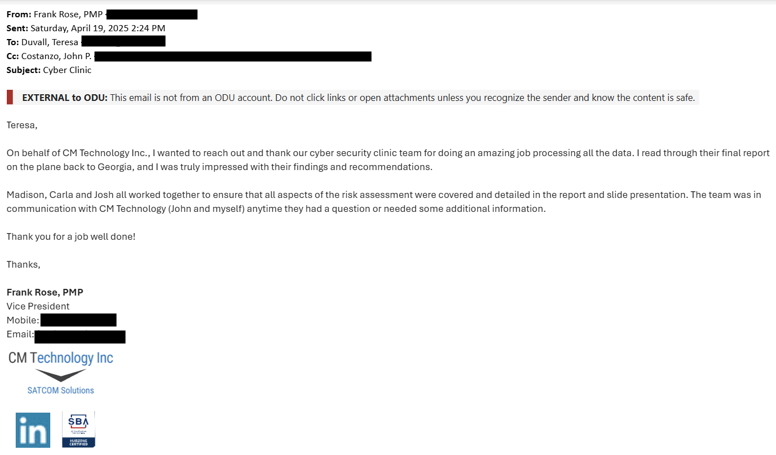
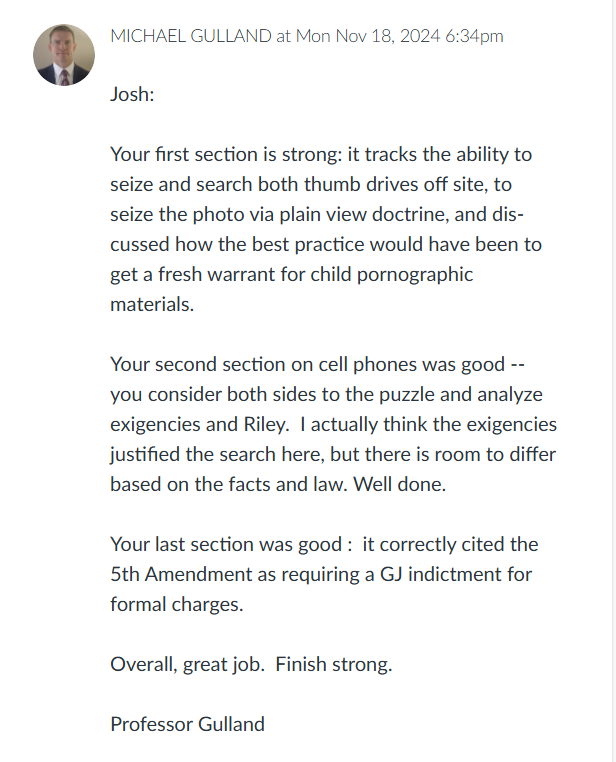
Part 1 of the assignment is to exploit the SMB on Windows XP with the Meterpreter. Part 2 of the assignment is to exploit EternalBlue on Windows Server 2008 with Metasploit. Part 3 of the assignment is to exploit Windows 7 with a Deliverable Payload.
Detailed Knowledge of Key Technologies
- Open Source Applications
- Linux Operating Systems
- Microsoft Technologies
- Wireless Technologies
- Database Modeling
- Web Application Technologies
- Compiled and Interpreted Development Languages
- Network Implementation (Operational and Security)
- Telephony Technologies (Analog and IP)
- Social Engineering
- Physical Security
- Network Security and Analytical Software
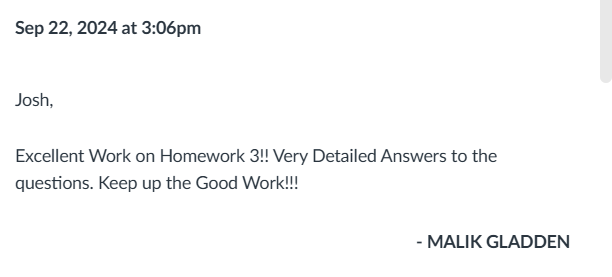
Part 1 of the assignment is to trace traffic using the packet aalyzing software Wireshark. Part 2 of the assignment is to use Wireshark and sniff traffic and analyze packets for hidden and non-hidden information.