During my time at Old Dominion University, I’ve developed a strong technical foundation in cybersecurity, demonstrated through a variety of Linux and Python projects. These hands-on experiences have equipped me with essential skills in system administration, scripting, and automation, enhancing my ability to tackle complex cybersecurity challenges with precision and efficiency.
CYSE 301: Cybersecurity Techniques and Operations- Password Cracking Lab
In my Cybersecurity Techniques and Operations class, I completed a password cracking lab that provided hands-on experience with Linux and Windows environments, where I explored both dictionary and brute-force attacks. Using tools like John the Ripper and Cain and Abel, I practiced techniques to crack password hashes, simulating real-world cybersecurity scenarios in which security professionals must identify weak passwords that could serve as vulnerabilities within an organization. Through these exercises, I gained insight into the complexities of password security and the importance of robust password policies. This experience emphasized how password cracking tools are used in cybersecurity to assess system vulnerabilities and reinforce security practices, directly applying my skills to real-world scenarios in penetration testing and systems auditing.
LAB-5-PASSWORD-CRACKING-PT.-1LAB-5-PASSWORD-CRACKING-PT.-2
CYSE 301: Cybersecurity Techniques and Operations- Traffic Tracing and Sniffing
In this lab, I practiced traffic tracing and packet sniffing using Wireshark, focusing on observing network traffic and filtering specific protocols like ICMP and DNS. By analyzing traffic flows and identifying key details in captured packets, I gained hands-on experience with network monitoring and protocol analysis. Skills in traffic tracing and packet sniffing are essential for cybersecurity professionals, as they enable detection of unauthorized access, monitoring for potential attacks, and understanding network vulnerabilities. This lab reinforced critical skills for real-world cybersecurity, where network visibility and data inspection are crucial for proactive threat detection and incident response.
LAB-2-TRAFFIC-TRACING-AND-SNIFFING-PT.-1LAB-2-TRAFFIC-TRACING-AND-SNIFFING-PT.-2
CYSE 301: Cybersecurity Techniques and Operations- Ethical Hacking
In this lab, I practiced ethical hacking techniques by exploiting vulnerabilities in Windows XP, Windows Server 2008, and Windows 7 systems. Using tools like Nmap and Metasploit, I identified open ports and services, then executed attacks against SMB vulnerabilities, including MS08-067 and EternalBlue. After successfully establishing connections, I performed post-exploitation tasks such as capturing screenshots, retrieving system information, and creating and transferring files to demonstrate control over the target systems. This hands-on experience reinforced the importance of ethical hacking skills in cybersecurity, allowing me to understand how attackers exploit unpatched vulnerabilities. By simulating these attacks, I gained insights into defensive strategies like timely patching, securing configurations, and monitoring network traffic for abnormal activity. This lab deepened my understanding of the tactics that are essential for protecting modern systems from real-world cyber threats.
LAB-4-ETHICAL-HACKING-PT-1LAB-4-ETHICAL-HACKING
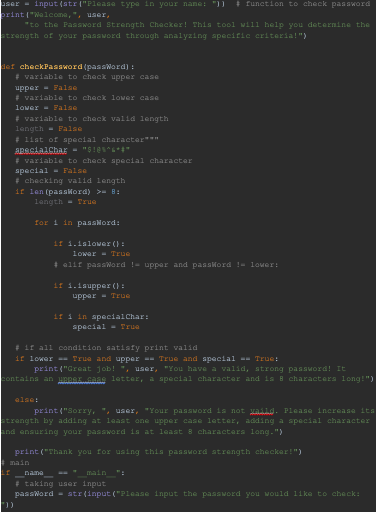
CYSE 250: Python Programming- Password Strength Checker Project
In this project, I developed a password strength checker using Python to evaluate the security of user-created passwords based on specific criteria. The code verifies that passwords meet essential security standards, such as containing both uppercase and lowercase letters, a minimum length of eight characters, and at least one special character. This project, completed as part of a class assignment, helped me understand and implement core functions in Python while working with conditional statements to handle multiple criteria. Additionally, in this class, I learned to establish server and client sockets, further enhancing my technical proficiency in network programming and security protocols.
CYSE 270: Linux Fundamentals- Bin/Bash and Crontab Scripting
For this lab, I learned essential skills in Bash scripting and automated backup processes, both vital in cybersecurity operations. Using Bash scripting, I streamlined repetitive tasks, reducing the potential for human error and enhancing efficiency—a core aspect of effective system management. Automating backups fortified data protection, ensuring that critical information remains recoverable in the event of accidental deletions, hardware failures, or security incidents like ransomware attacks. These skills are directly relevant in real-world cybersecurity, where automation and reliable backup strategies are crucial for building resilient systems and safeguarding organizational data. This experience not only strengthened my technical abilities but also deepened my understanding of proactive security measures that form the backbone of any robust cybersecurity strategy.
PDF Embedder requires a url attribute