Essential Work Habits
- Enthusiastic and highly adaptable
- Strong analytical and diagnostic skills
- Ability to get the job done
In the embedded assignment above, I used Metasploit in a Kali Linux VM to establish a reverse tcp meterpreter session (gaining access to a Windows VM). I then escalated my privileges by migrating process ID numbers (a running service on the windows VM) and proceeded to record keystrokes etc. and output the sensitive data to a text file. I ran into a lot of issues trying to escalate to admin privileges, and had to adapt when the test showed the attempts failed. In this way I had to be analytical and diagnose what the problem was as well as search for alternative methods.
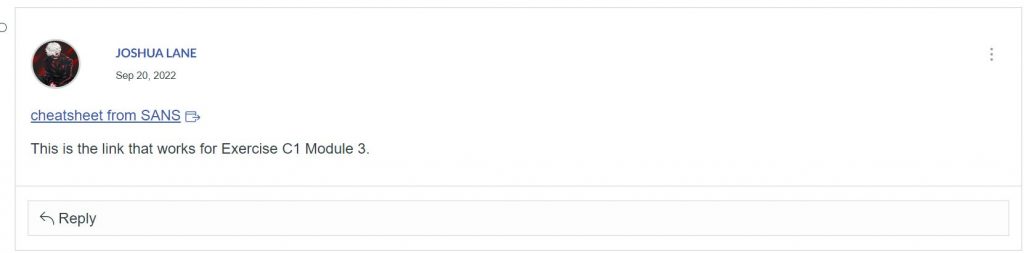
Pictured below is the discussion forums that our school used where I posted the correct link to something related to the assignment. The website had migrated, and I found the new one with a different domain using my resources. I then provided it to the class.
Soft Skills
- Excellent presentation and communications skills to effectively communicate with management and customers
- Ability to clearly articulate complex concepts both written and verbally
- Ability, understanding, and usage of active listening skills especially with customers
Pictured below is my response paper to when speech is considered violence and what ethical implications this has for academic society. I argued in favor of keeping scholarly discussion open and properly defining when speech is considered violence versus offensive in order to avoid issues. My professor asked my permission to use it as an example paper and gave me top marks.
When-Is-Speech-Violence-L1-Response-Paper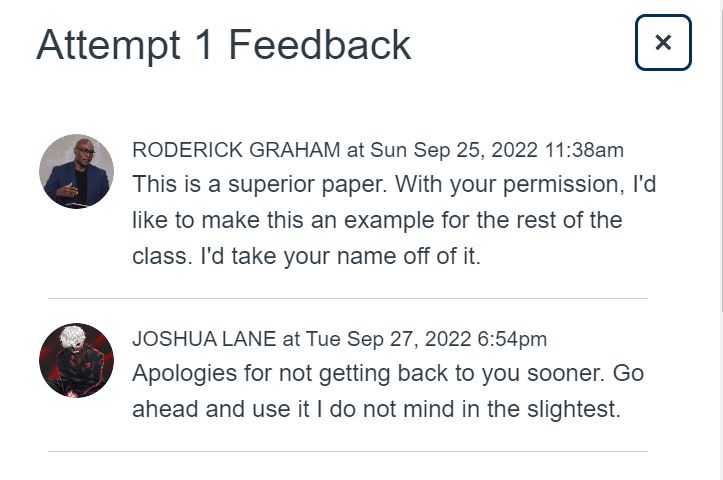
Above is a screenshot of my professor asking to use my paper as an example.
I worked as a cashier at The Home Depot for 2 years. I interacted with customers all day long with helping them find miscellaneous products, loading vehicles, and overall solving their problems (I took a public speaking course at ODU and aced it, but I do not have any saved artifacts since they were on a different pc that I no longer have). I also worked in product quality management at U.S. Port Services where I had to work as a team to offload expensive products (such as luxury vehicles) and check for damage. I had a good working relationship with my boss and the rest of the hires there. References available upon request.
Solid Technical Foundation
- Understand architecture, administration, and management of operating systems, networking, and virtualization software
- Working with Wireshark, Nmap, packet capturing/filtering
- Experience using Open Source Intelligence tools
- Threat assessment report of a business/website and stating how to solve said issues that lead to vulnerabilities
Embedded below is an assignment that shows me using OSINT and engaging and passive/active footprinting of people. This shows my skill in sleuthing using Open Source Intelligence tools.
Passive-and-Active-Footprinting-LessonExercise_UPDATED20210218Embedded below is a business memo/report that I wrote as if I was already an employee in the Cyber department writing a memo explaining the threats the business may face and what needs to be done to address them. This is an important process to securing a businesses’ infrastructure (shows my skill in properly articulating to someone why they need a cyber department or need to outsource to secure their infrastructure).
Threat-AssessmentDetailed Knowledge of Key Technologies
Include artifacts here that demonstrate your experience with some of the abilities listed below.
- Linux Operating Systems (Kali Linux, Ubuntu – linux-based)
- Microsoft Technologies (Windows 7, 8, Windows Server 2016, Windows Server 2019)
- Base knowledge of bash scripting using Python programming language
- Social Engineering
- Experience with Metasploit, Sublime Text Editor (python scripting to read websites/grab cookies).
- Ethical Hacking/Penetration Testing
The assignment from my Enterprise Cyber Defense class (business cyber defense) embedded below shows me using bash scripting (contains base knowledge of python coding to create scripts) to automate processes such as downloading text files and seeing if websites are crawlable. This was done in a Kali Linux VM environment.
Bash-Scripting-Robots-LessonExerciseEmbedded below is an assignment from my Enterprise Cyber Defense class shows me using Snort in a pfSense web interface to secure a network using intrusion detection and prevention. It also demonstrates my ability to navigate firewalls and the many packages they offer.
Intrusion-Detection-Prevention-ReportEmbedded below is another assignment demonstrating my ability to use python coding language to write scripts that read websites/grab cookies and print them out etc. in Sublime text editor. This was done to complete capture the flag exercises.
Natas-Level-0-6-H1